|
|
|
|
7/31/2011
Virus Heat
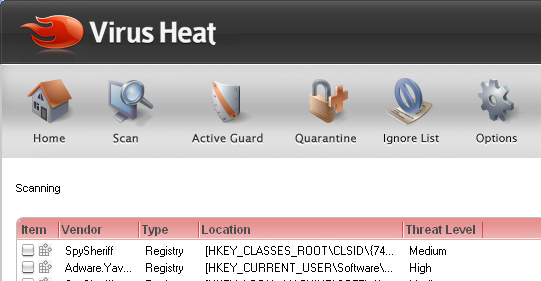
31/07/11 - Virus Heat, a new version of corrupt parasite
removers was launched some time ago.
Virus Heat owners, who host in Ukraine, claim that they have worked on this tool
since 2000 and
have the best tool around. Surely, this parasite will help you clean the fake and some known
spywares
that came with it when you pay money for the full version of it. However, your credit
card details will fall in the hands
of its manufacturers, which are not the most honest of folk, even
though they claim to be.
Virus
Heat 4.4 - a clone of Virus Heal, Spy Dawn and other similar tools - is not a reliable
spyware remover. It produces exaggerated
reports with false positives, Virus Heat does not
remove any of the most popular true parasites and should be marked
as a SCAM. Please
avoid installing this corrupt anti-spyware and if you did - remove Virus Heat as soon as possible.
 Virus Heat removal
process is quite easy, but we advise to use automated removal solutions Virus Heat removal
process is quite easy, but we advise to use automated removal solutions
for best results.
Virus Heat properties:
• Changes browser settings
• Shows commercial adverts
• Connects itself to the internet
     
8:06 pm edt
Malware Protection
4:13 am edt
7/30/2011
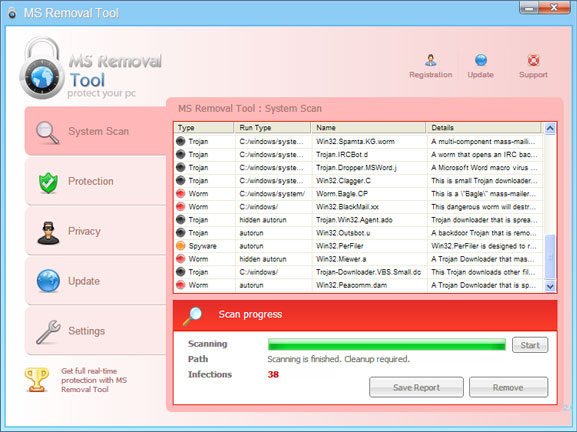
MS Removal Tool 30/07/11 - MS Removal Tool is a rogue anti-spyware application from the same family as System
tool. It pretends to be a legitimate security program,
but actually it is nothing more but a scam.
This rogue program is distributed through the use of Trojan horses, fake
online scanners, and
infected websites. Once installed, it will pretend to scan your computer for viruses and claim that
your computer is infected with spyware, adware, Trojans and other malware. MS Removal Tool
will prompt you to pay for
a full version of the program to remove the infections from your
computer. Don't pay for this rogue program. It won't
protect your computer. You should remove
MS Removal Tool from your computer as soon as possible. You can choose
to remove this virus
manually or using an automatic MS Removal Tool.
MS Removal Tool is a very annoying rogue
program because it displays fake security alerts and
popups without your permission. The rogue program blocks nearly
all programs on the infected
computer claiming that they are infected with malicious software. The fake error message
reads:
Warning!
Application cannot be executed. The file cmd.exe is infected.
Please activate your
antivirus software.
It will constantly display fake security warnings about serious security and privacy issues.
It will
state that you computer is infected.
MS Removal Tool Warning
Your PC is infected with dangerous
viruses. Activate antivirus protection to prevent data loss and
avoid the theft of your credit card details.
Click
here to activate protection.
MS Removal Tool Warning
Intercepting programs that may compromise your privacy
and harm your system have been
detected on your PC.
Click here to remove them immediately with MS Removal Tool.
Last, but not least, it will change your desktop wallpaper with its own which states that your
computer is infected
with spyware. The text of the fake background image:
Warning!
Your're in Danger!
Your Computer is infected
with Spyware!
 Everything you do with your computer is stored in
your hard disk. When you visit sites, send Everything you do with your computer is stored in
your hard disk. When you visit sites, send
emails... All your actions are logged. And it is impossible to remove them
with standard tools.
Your data is still available for forensics, and anyone else who has access to the physical
system. Every
site you access (opened with your browser) including images, downloaded
material, etc, or even - is still accessable
through forensics!
Secure yourself right now!
Removal all spyware from your PC!
It is obvious that
MS Removal Tool is yet another rogue scam. Don't trust it. If you find that your
computer has been infected with
this rogue program then please uninstall MS Removal Tool
from your computer as soon as possible. If you have already
purchased it, then you should
contact your credit card company and dispute the charges. Note, that you will have
to reboot
your computer in safe mode with networking in order to be able to download the automatic
removal
tool because MS Removal Tool blocks legitimate malware removal tools in normal mode.
MS Removal Tool
properties:
• Changes browser settings
• Shows commercial adverts
• Connects itself
to the internet
• Stays resident in background
     
3:35 pm edt
7/29/2011
Win 7 Home Security 2012
29/07/11 - Win 7 Home Security 2012 is a fake anti-spyware program that is promoted through
the use of
Trojans, browser hijackers and other similar malware. When your computer is infected
with this bogus software, you will
see many fake security alerts and notifications stating that
your computer is infected. While running, Win 7 Home Security
2012 will supposedly scan your
computer and display a variety of infections that won't be removed unless you first purchase
the
program. The scan results are false, you can safely ignore them. The same could be said about
fake system security
alerts, you should ignore them too.
To make things even worse, Win 7 Home Security 2012 will hijack Internet Explorer
so that you
will be constantly redirected to various misleading websites that promote malicious software or
display
misleading online ads. The rogue application will also block security related websites
and antivirus software to
protect itself form being deleted. As you can see, this program is
nothing more than a scam. Please remove Win 7 Home
Security 2012 from your PC as soon
as possible.
     
11:44 pm edt
7/28/2011
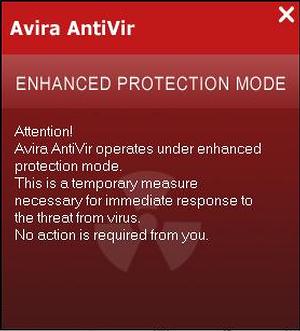
Avira AntiVir Enhanced Protection Mode 28/07/11 - Avira AntiVir Enhanced Protection
Mode is a fake security alerts that mimics Avira
AntiVir's (the Highly acclaimed Legitimate Security Suite) security
notifications. It infects a
computer via Trojans, infected websites and fake Flash Player installers. The legitimate
Avira
AntiVir application does not support Enhanced Protection Mode, the fake alert tries misleading
users
into thinking that their computers are protected when in fact they are wide open to various
security threats. If you
have this fake Avira AntiVir Enhanced Protection Mode alert on your
computer, use Spyware Doctor to remove it. Here
is an example or the 'Fake' alert text:
Attention! Avira AntiVir operates under
enhanced protection mode.
This is a temporary measure necessary for immediate response to the
threat from a virus!
 Remove this fake program with one of the automatic
removal tools listed below. Remove this fake program with one of the automatic
removal tools listed below.
     
7:56 pm edt
7/27/2011
ErrorKiller 27/07/11 - ErrorKiller is a rogue registry cleaner - a fake registry cleaner utility, which fashions
itself to be a legitimate program. This scam is in no way out of the ordinary and works exactly
the same as most rogues
do: it infects the system by using trojans, such as Zlob or Vundo, and
uses scare tactics (most commonly - popups and
fake system notifications) to convince the
user that he has errors in his registry, which can best be removed using the
"licensed version"
of ErrorKiller.
ErrorKiller has a nice website and even live support. The live
support personnel adamately defend
the product as a legitimate program. ErrorKiller is a scam and should be treated as
such: do
NOT download or buy it and block ErrorKiller.com using your HOSTS file.
ErrorKiller properties:
• Changes browser settings
• Shows commercial adverts
• Connects itself to the internet
•
Stays resident in background
     
8:15 pm edt
BAT.Winstart 27/07/11 - This is an extremely dangerous trojan, which
changes Windows settings by modifying
WINSTART.BAT. This action is already a real threat to the stability of the infected
system. What
is more diabolical, this Trojan is memory-resident - this allows the parasite to perform a wide
variety of destructive actions at any time. To sum everything up, this trojan is a really dangerous
pest, which can
cause lots of problems to the user, who has no up-to-date security installed on
the PC. Your Security software is only
as affective as your latest update ... Keep your security
software up to date and remove this parasite as soon
as possible.
BAT.Winstart properties:
• Hides from the user
• Stays resident in background
     
5:37 am edt
7/26/2011
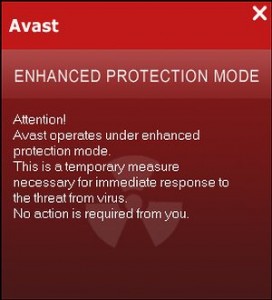
Avast Enhanced Protection Mode 26/07/11 - Avast Enhanced Protection Mode is a fake security alert that mimics Avast (a very
reputable security suite) security notifications. It comes into a
users computer via Trojans,
infected websites and fake Flash playerinstallers. The legitimate Avast! application does
not
support Enhanced Protection Mode, the fake alert tries misleading users into thinking that their
computers
are protected when in fact they are wide open to various security threats. If you have
this this fake Avast Enhanced
Protection Mode alert on your computer, use Spyware Doctor or
one of the automatic removal tools shown below, to remove
it.
Here is a sample of the 'Fake alert text':
Attention! Avast operates under enhanced protection mode.
This is a temporary measure necessary for immediate response
to the threat from a virus!
3:35 pm edt
PC MightyMax 26/07/11 - PC MightyMax can be classified as a fake and useless diagnostic tool, because it can
be difficult to exit without purchasing the
full version of this product. It seems that PC Mighty
Max was design to periodically display pop-up windows and distracting
alerts in order to scare
users into purchasing this worthless application.
PC MightyMax
runs automatically when a computer starts, and there is no easy way how to
change this attribute. What is more, it has
no setting to allow users to disable this function.
Every few hours, PC MightyMax displays "CRITICAL ALERT"
and "Alert!!!" pop-up windows that
are mainly advertisements for the full version of the this software. These
officious alerts can even
make beeping noises decreasing a user's ability to work with his computer. Summing-up, PC
MightyMax may be considered an unwanted application which should be removed without
consideration.
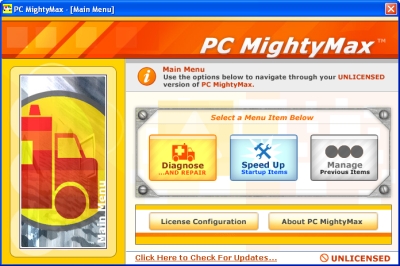 PC MightyMax properties: PC MightyMax properties:
•
Changes browser settings• Shows commercial
adverts
• Connects itself to the internet
• Stays resident in background
     
3:24 pm edt
7/25/2011
BlueFlare Antivirus 25/07/11 - BlueFlare Antivirus is a misleading security application that reports false system
security
threats and infections on your computer to make you think your PC is infected with
spyware, Trojans and other malicious
software. However, the only infection is BlueFlare Antivirus
itself. Once installed, the rogue program will imitate system
scan and display a variety of
infections that can't be removed with a trial version of the program. So you will be prompted
to
buy BlueFlare Antivirus to remove those non-existing infections. However, we strongly
recommend you not do so.
Otherwise, you will simply lose your money and won't get anything in
return. Instead, uninstall BlueFlare Antivirus from
your computer upon detection.
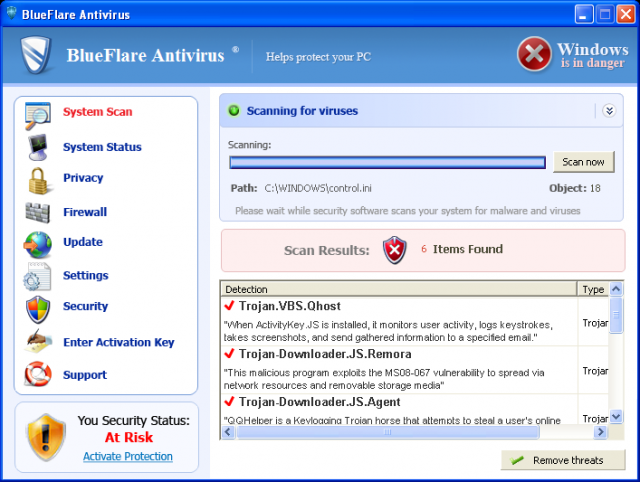 When running, BlueFlare Antivirus will display
fake security alerts every one or two minutes. When running, BlueFlare Antivirus will display
fake security alerts every one or two minutes.
The rogue program will impersonate Windows Security Center and claim
that it did not find
antivirus software on your computer. Next, BlueFlare Antivirus will suggest you to buy a licence
and activate antivirus software. What is more, you will be flooded with fake security notifications
about serious security
and privacy problems. It should be already obvious that BlueFlare
Antivirus is a scam; a totally useless application.
If you find that your computer is infected with
this parasite, please use an automatic removal tool to remove
BlueFlare Antivirus from the
system.
     
9:35 pm edt
Antivirus 2010 25/07/11 - Antivirus 2010 represents a new generation
of rogue security tools. Not only does it
use misleading advertisements to gain a purchase, but it also crashes
a system and loads fake
Blue Screen of Death. The text on BSOD is fabricated and claims that MS Windows
recommends purchasing
Antivirus 2010 to remove spyware from a machine. This
recommendation is just a trick of Antivirus 2010 and it shouldn’t
be trusted. Fake BSOD looks
like this:
“***STOP: 0×000000D1 (0×0000000,
0xF73120AE, 0xC0000008, 0xC000000)
A spyware application has been detected and Windows has been shut down to prevent damage
to
your computer
SPYWARE.MONSTER.FX_WILD_0×0000000
If this is the first time you’ve seen this
Stop error screen, restart you computer. If this screen
appears again, follow these steps:
Click to make sure your
antivirus software is properly installed. If this is a new installation, ask
you software
manufacturer for any antivirus updates you might need.
Windows detected unregistered version of Antivirus 2010 protection
on your computer. If problem
continue, please activate your antivirus software to prevent computer damage and data loss.”
If your computer displays this message, do not trust it and do not pay for Antivirus 2010 malware.
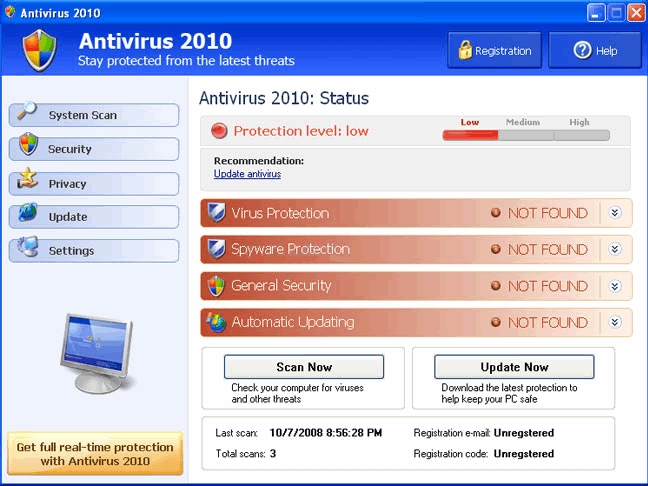 Antivirus 2010 spreads like many similar applications.
It is distributed through online Antivirus 2010 spreads like many similar applications.
It is distributed through online
advertisements that are disguised as anti-virus scanners. If a user clicks on such a
banner, he
or she receives false reports about infections detected. Antivirus2010 tries to intimidate people
by reporting nonexistent threats in order to get them interested in downloading this application.
Sometimes Antivirus
2010 might be installed by trojans without a user’s consent.
Antivirus 2010 is not a security tool; it is dangerous
computer parasite. Avoid downloading or
buying this program.
     
9:22 pm edt
Win 7 Security 2012 25/07/11 - Win 7 Security 2012 is a rogue anti-spyware program that reports false system
security
threats to make you think that your computer is infected with malware
when the only
actual infection is Win 7 Security 2012 itself. It also displays fake security alerts and pop-ups
stating
that your computer is under attack from a remote computer or that your sensitive
information can be stolen. Finally,
it will ask you to purchase the program to remove the
infections which don't even exist on your computer. As you can
see, Win 7 Security 2012 is a
total scam. Please don't purchase it and uninstall this bogus program from your computer
upon
detection.
Win 7 Security 2012 is a typical rogue program promoted through the use of Trojans
and other
malicious software. Trojan horses usually come from fake online anti-malware scanners or other
misleading web sites. Once running, Win 7 Security 2012 will scan your computer
for malware
and display a list of infections that supposedly can't be removed with a trial version of the
program, so you have to buy it. However, you already know that this is nothing more than a
scam. Win 7 Security 2012 won't make your computer more secure nor will it remove malware
from your
computer. What is more, it will block legitimate programs and hijack Internet Explorer
to protect itself from being removed. As you can see, this fake program is not only very annoying
but also
dangerous. It may install additional malware on your computer. If you find that your PC
is infected with Win 7 Security 2012 please use an automatic removal tool to remove this
infection. If
you have already purchased this program then you should contact your credit card
company and dispute the charges.
     
9:07 pm edt
7/24/2011
XP Security 2012 24/07/11 - XP Security 2012 is a fake security program that pretends to be a malware removal
tool.
This rogue anti-spyware usually comes unnoticeably without any permission asked, so if
you find XP Security 2012 on your
computer you are most likely to have gotten it through a
Trojan. These Trojans not only install this fake anti-spyware
thing but also change the Registry
and drop fake random files which later are detected as malware.
Security
experts announce that when installed on different OS, XP Security 2012 appears in
different name, though the malcode
stays the same. So, when using Win 7 Antispyware name,
the trial version of this parasite infects only Windows XP OS.
Installed without any knowledge
and consent, the program initially applies the tactics typical for this type of
malware. It usually
triggers fabricated general system scans that return the results which can be easily
predetermined.
Don’t get surprised after being informed that various threats of different severity
are detected. XP Security 2012
also generates fake positives that report infections that are
expected to make you doubt your PC's security. Keep
in mind that clicking on any pop-up add
will automatically get you into XP Security 2012's "official" website.
These sites must be avoided
because they aggressively promote its “full” commercial version. Don’t
buy this scam, because
you will only support the scammers. Having XP Security 2012 “licensed” version is
useless
because it will dramatically eat up your bandwidth slowing down your computer. To sum it up, it
must be clear that XP Security 2012 must be removed as soon as possible, so please, delete
this scam.
     
8:45 pm edt
Phishing Scams
Phishing Scams
"We suspect an unauthorized transaction on your account. To ensure
that your account is
not compromised, please click the link below and confirm your
identity."
"During our regular verification of accounts,
we couldn't verify your information. Please
click here to update and verify your information."
Have you received email with a similar message? It's a
scam called "phishing" — and it involves
Internet fraudsters who send spam or pop-up messages to lure personal information (credit card
numbers,
bank account information, Social Security number,
passwords, or other sensitive
information) from unsuspecting victims.
According to OnGuard Online,
phishers send an email or pop-up message that claims to be from
a business or organization that you may deal with — for example, an Internet service provider
(ISP), bank, online payment service, or even a
government agency. The message may ask you to
"update," "validate," or "confirm" your account
information. Some phishing emails threaten a
dire
consequence if you don't respond. The messages direct you to a website that looks just
like a legitimate
organization's site. But it isn't. It's a bogus site whose sole purpose is to trick
you into divulging your personal information so the operators can steal
your identity and run up
bills or commit crimes in your name.
OnGuard Online suggests these tips
to help you avoid getting hooked by a phishing scam:
If you get an email
or pop-up message that asks for personal or financial information, do
not reply. And don't click
on the link in the message, either.
Legitimate companies don't ask for this
information via email. If you are concerned about your
account, contact the organization mentioned in
the email using a telephone number you know
to be genuine, or open a new Internet browser
session and type in the company's correct Web
address yourself. In any case, don't cut and paste the link from the message into your Internet
browser — phishers can make links look like they go to one place, but that actually send you to
a different site.
Area codes can mislead. Some scammers send emails that appear to be from a legitimate
business and ask you to call a phone number to update your account or access a "refund."
Because they use Voice over Internet Protocol technology, the area code you call does not
reflect
where the scammers really are.
If you need to reach an organization
you do business with, call the number on your financial
statements or on the back of your credit card.
And delete any emails that ask you to confirm
or divulge your financial information.
Use anti-virus and anti-spyware
software, as well as a firewall, and update them all
regularly.
Some phishing emails contain software that can harm your computer or track your
activities
on the Internet without
your knowledge.
Anti-virus
software and a firewall can protect you from inadvertently accepting such unwanted files.
Anti-virus software Scans incoming communications for troublesome files. Look for anti-virus
software that recognizes current viruses as well
as older ones; that can effectively reverse the
damage; and that updates automatically.
A firewall
helps make you invisible on the Internet and blocks all communications from unauthorized
sources. It's Especially important to run a firewall if you have a broadband connection. Operating
systems (like Windows or Linux) or browsers (like
Internet Explorer or Netscape) also may offer free
software "patches" to close holes in the system that hackers or phishers could exploit.
Don't email personal or financial
information. Email is not a secure method
of transmitting
personal information. If you initiate a transaction and want to provide
your personal or
financial information
through an organization's website, look for indicators
that the site is
secure, like a
lock icon on the browser's status bar or a URL for a website that begins
"https:"
(the "s" stands for "secure"). Unfortunately, no indicator is foolproof; some phishers
have forged security icons.
Review credit card and bank
account statements as soon as you receive them to check
for unauthorized charges. If your statement is late by more than a couple of days, call your
credit card company or bank to confirm your billing address and account balances.
Be cautious about opening any
attachment or downloading any files from emails you
receive, regardless of
who sent them. These files can contain viruses
or other software that
can weaken
your computer's security.
Forward phishing emails to spam@uce.gov – and to the company, bank, or organization
impersonated in the phishing email. Most organizations
have information on their websites
about where to report problems. You also may
report phishing email to
reportphishing@antiphishing.org. The Anti-Phishing Working Group, a consortium
of ISPs, security vendors, financial
institutions and law enforcement agencies, uses these
reports to fight phishing.
If you believe you've been scammed,
file your complaint at ftc.gov, and then visit the FTC's
Identity Theft website at ftc.gov/idtheft. Victims of phishing can become victims of identity theft.
While
you can't entirely control whether you will become
a victim of identity theft, you can take
some
steps to minimize your risk. If an identity thief is opening credit accounts in your name,
these new accounts are likely to show up on your credit report. You may catch an
incident early if you order a free copy
of your credit report periodically from any of the three
major credit reporting companies.
See www.annualcreditreport.com for details
on ordering a free annual credit report.
Learn other ways to avoid email scams and deal with deceptive spam at ftc.gov/spam.
How to Report if You Have Been
a Victim of a Phishing Scam
Forward spam
that is phishing for information to spam@uce.gov – and to the company, bank, or
organization impersonated in the phishing email. Most organizations have information on their
websites about
where to report problems.
If you believe you've been scammed, file
your complaint with the FTC, and then visit the FTC's
Identity Theft website at ftc.gov/idtheft. Victims of phishing can become victims of identity theft.
You also may report phishing email to reportphishing@antiphishing.org. The Anti-Phishing
Working Group, a consortium Of ISPs, security vendors, financial institutions and law
enforcement agencies, uses these reports
to fight phishing.
Securing Your Wireless Network
Securing Your Wireless Network
Increasingly, computer
users interested in convenience and mobility are accessing the Internet
wirelessly. Today, business travelers use wireless laptops to
stay in touch with the home office;
vacationers beam snapshots to friends while still on holiday; and shoppers place orders from the
comfort of their couches.
A wireless network can connect computers in different parts of your home or business without
a
tangle of cords
and enable you to work on a laptop anywhere within the network's range.
Going wireless generally requires a broadband Internet connection
into your home, called an
"access point," like a cable
or DSL line that runs into a modem. To set up the wireless network,
you connect the access point to a wireless router that broadcasts a signal through the air,
sometimes as far as several hundred feet.Any
computer within range that's equipped with a
wireless client
card can pull the signal from the air and gainaccess to the Internet.
The downside of a wireless network is that, unless you take certain precautions, anyone with a
wireless-ready computer can use your network.
That means your neighbors, or even hackers
lurking nearby, could "piggyback" on your network, or even access the information on your
computer.
And if an unauthorized person uses your network to commit a crime or send
spam,
the activity can be traced back to your account.
Fortunately, there are steps you can take to protect your wireless network and the computers
on it. As no one step is a complete fix, taking
all of the following steps will help you be more
secure.
Precautionary Steps
1. Use encryption. The most effective way to secure your wireless
network from
intruders is to encrypt, or
2.
scramble, communications over the network.
Most wireless routers, access points,
and
base stations
3.
have a built-in encryption mechanism.
If your wireless router doesn't have an
encryption feature,
4.
consider getting one that does. Manufacturers often deliver wireless routers with the
encryption feature turned off.
You must turn it on. The directions that come with
your wireless router should explain
how to do that. If they don't, check the router manufacturer's website. Two main types
of encryption are available: Wi-Fi Protected Access (WPA) and Wired Equivalent
Privacy (WEP). Your computer, router, and other equipment must use the same
encryption. WPA
is stronger; use it if you have a choice. It should
protect you against most
hackers.
Some older routers use only WEP
encryption, which is better than no
encryption.
It should protect your wireless network against accidental
intrusions
by neighbors or attacks by less-sophisticated hackers. If you use WEP
encryption, set it to the highest security level
available. Learn how…
5.
Use anti-virus and anti-spyware
software, and a firewall. Computers on a wireless
network need the
6. same protections as any computer connected to the Internet. Install
anti-virus and
anti-spyware software,
7. and keep them up-to-date. If your firewall was shipped in the "off"
mode, turn it on.
Learn how…
8. Turn off identifier broadcasting. Most wireless routers have a mechanism called
identifier broadcasting.
9.
It sends out a signal to any device
in the vicinity announcing its presence. You don't
need to broadcast this
10.
information if the person using the
network already knows it is there. Hackers can
use identifier broadcasting
11.
to home in on vulnerable wireless networks.
Note the SSID name so you can
connect manually. Disable the
12.
identifier broadcasting mechanism if
your wireless router allows it. Learn how…
13.
Change the identifier on your
router from the default. The identifier for
your router is
likely to be a standard,
14.
default ID assigned by the manufacturer
to all hardware of that model. Even if your
router is not broadcasting
15. its identifier to the world, hackers know the default IDs and can
use them to try to
access your network.
16.
Change your identifier to something
only you know, and remember to configure the
same unique ID into your
17.
wireless router and your computer so
they can communicate. Use a password that's
at least 10 characters
18.
long: The longer your password, the
harder it is for hackers to break. Learn how…
19.
Change your router's pre-set
password for administration. The manufacturer
of
your wireless router probably
20. assigned it a standard default password that allows you to set
up and operate the
router. Hackers know these
21.
default passwords, so change it to something
only you know. The longer the
password, the tougher it is to
Click here if you don't know or can't remember your base station password.
23. Allow only specific computers to access your wireless network. Every computer
that is able to communicate
25. a mechanism to allow only devices with particular MAC addresses
access to the
network. Some hackers have
26. mimicked MAC addresses, so don't rely on this step alone. Learn how…
27.
Turn off your wireless network
when you know you won't use it. Hackers cannot
access a wireless router
28.
when it is shut down. If you turn the
router off when you're not using it, you limit the
amount of time that it is
29.
susceptible to a hack.
30.
Don't assume that public "hot
spots" are secure. Many cafés,
hotels, airports, and
other public establishments
31. offer wireless networks for their customers' use. These "hot spots" are convenient,
but they may not be secure.
32. Ask the proprietor what security measures are in place.
33. Be careful about the information you access or send from a public
wireless
network. To be on the safe side,
34. you may want to assume that other people can access any information you see or
send over a public wireless
35. network. Unless you can verify that a hot spot has effective security measures in
place, it may be best to avoid
36. sending or receiving sensitive information over that network.
Glossary
Encryption: The scrambling of data into a secret code that
can be read only by software set to
decode the information.
Extended Service Set Identifier (ESSID): The name a manufacturer assigns to a router. It may
be a standard, default name assigned by the manufacturer
to all hardware of that model. Users
can improve security by changing to a unique name. Similar to a Service Set Identifier (SSID).
Firewall: Hardware or software designed to keep hackers from using your computer to send
personal information
without
your permission.
Firewalls watch for outside attempts to access
your system and
block communications to and from sources you don't permit.
Media Access Control
(MAC) Address: A unique number that the manufacturer assigns
to each
computer or other device in a network.
Router: A device that connects two or more networks. A router finds the best path for forwarding
information
across the networks.
Wired Equivalent Privacy (WEP): A security protocol that encrypts data sent to and from
wireless devices within a network. Not as strong as WPA encryption.
Wi-Fi Protected Access (WPA): A security protocol developed to fix flaws in WEP. Encrypts
data sent to and from wireless devices within a network.
Wireless Network:
A method of accessing high speed Internet without the computer being
linked by cables.
Win 7 Internet Security 201224/07/11 - Win 7 Internet Security 2012 is a phony anti-spyware program that supposedly scans
your computer for malware and displays a list of false system
security threats to scare you into
thinking that your computer is infected with worms, trojans, spyware and other malware.
The
rogue program (then) prompts users to pay for a full version of the program to remove the
infections (which
don't even exist) to ensure full system protection against other malware. This
misleading program also displays fake
security warnings and pop-ups claiming that your
computer is severly infected or that your data might be deleted. Don't
trust it and remove Win 7
Internet Security 2012 from your computer upon detection.
Furthermore, Win 7 Internet
Security 2012 hijacks Internet Explorer and blocks almost all sites
claiming that they are infected or compromised and
may infect your computer. It prioritizes the
blocking of all security related websites. Win 7 Internet Security
2012 also blocks antivirus and
anti-spyware applications. It prevents new installation of anti-malware tools so you will
have to
ends its processes first otherwise, it will continue to block malware removal tools. If you find
that your
computer is infected with this annoying virus, please remove Win 7 Internet Security
2012 as soon as possible either
manually or with an automatic removal tool.
     
5:35 pm edt
7/23/2011
Antivirus 360 23/07/11 - Antivirus 360 is a fake spyware remover, program with evil intent. Classified a Parasite,
as are many of its kind, it tries to push
users into purchasing a licensed version with falsified
threats. The name Antivirus 360 sounds very similar to respected
security tool Norton 360 by
Symantec. The application makes its own way into user’s computers via trojan Zlob or
by
manual download. After installation, the parasite floods users with numerous pop-ups and
imaginary virus infections
(system risks). After these notifications Antivirus 360 advertises itself
as an effective program that is able to fix
all these problems, and of course it is a paid one. This
program is very dangerous, it marks windows files as an infection
or serious threat. The main
purpose of it is to show pop-ups and suck money. It does not fix any true infection.
As a
parasite, Antivirus 360 can cause many serious problems for users (computer slow down, limit
connection of
internet, increase loss of personal data, etc.) even disabling your machine. We
recommend you scan your system with reputable
spyware remover programs (and remove this
parasite) to avoid problems.
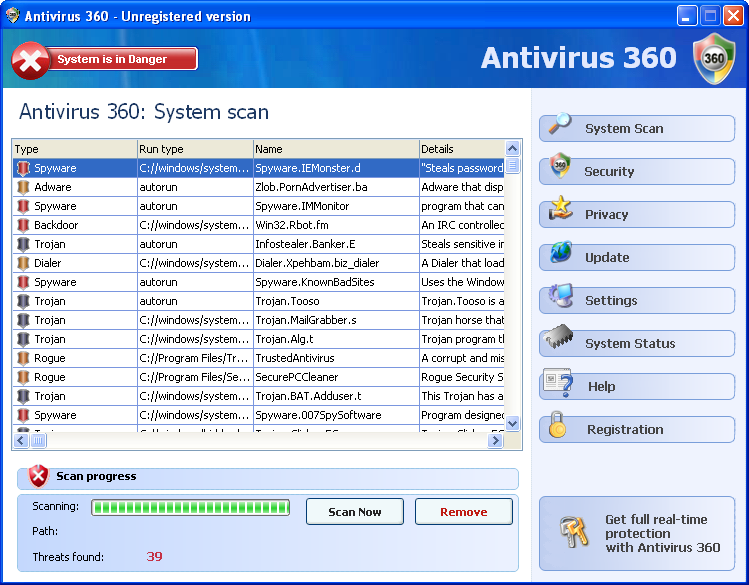 Antivirus 360 properties: Antivirus 360 properties:
•
Changes browser settings
• Shows commercial adverts
• Connects itself to the internet
• Hides
from the user
• Stays resident in background
     
9:40 pm edt
Security Protection 23/07/11 - Security Protection is another bogus anti-spyware application. Most of the time, it is
promoted
through the use of Trojans that display fake security alerts. These alerts state that
your computer is seriously infected
with malware, spyware or Trojans and that you should install
it in order to remove these threats. Furthermore, it might
be advertised on various malicious
websites or via fake online scanners. Once installed, Security Protection will supposedly
scan
your computer and provide a list of dangerous infections and security risks that can be removed
only with a
full version this bogus software. Of course, these infections do not actually exists on
your computer. Security Protection
displays these fake infections in order to scare you into
purchasing the program. The rogue will also constantly display
fake security alerts. These alerts
are similar to this one shown below:
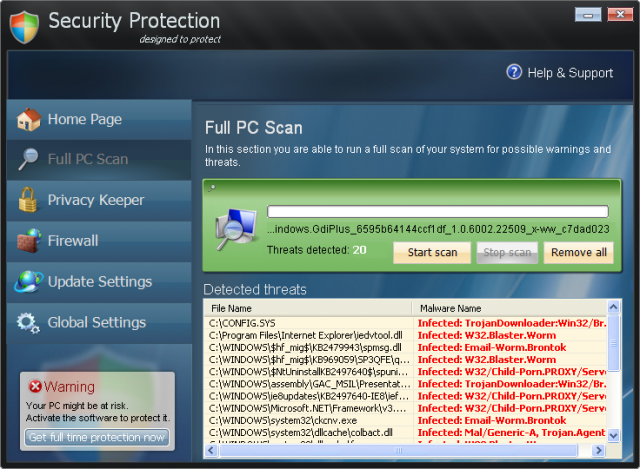 Security Protection is a scam, don't purchase it under any circumstances.
Instead, you should Security Protection is a scam, don't purchase it under any circumstances.
Instead, you should
get rid of this parasite as soon as possible. Please use one of the automatic removal programs
below to remove Security Protection from your computer.
     
9:24 pm edt
7/22/2011
Total Protect 2009 22/07/11 - Total Protect 2009 is a fake spyware remover tool. Application is installed into
computer through the use of trojans. When Total Protect 2009 is on board it begins to load
imaginary system reports
with claims about infections and system risks. If you click on any
of these pop-ups you will be redirected to the website that has rogue content. Of course all
this is made
to force users into buying of Total Protect 2009 full version, which in fact doesn't
do anything. Program is configured
to start automatically every time you log on into Windows.
Manual removal of Total Protect 2009 could be very difficult
because it hides from users and
does not appear in add/remove list of programs. Also this parasite may cause numerous
problems (like system slow down or even limited internet connections).
Remember that all
notifications are falsified and only one way to keep your computer safe is to use legitimate
anti-spyware software. 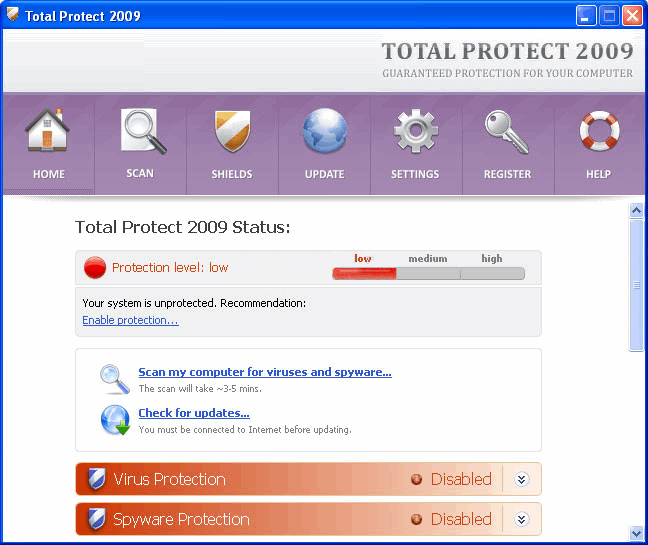 Total Protect 2009 properties: Total Protect 2009 properties:
•
Changes browser settings
• Shows commercial adverts
• Connects itself to the internet
• Hides from the user
• Stays resident in background
***Use
an automatic removal tool to remove this program.
     
8:51 pm edt
Total Protect
8:34 pm edt
Vista Security 2012 22/07/11 - Vista Security 2012 is a fake computer security program that promises its victims to
fix
their computers and remove all viruses detected. However, you should know that these
“viruses” won’t
be found by any legitimate anti-spyware because Vista Security 2012 fakes them
trying to make you concerned. This scam
hails from notorious a family of malware which expects
to steal users’ money. By changing its name according to
the OS it finds, programs from Vista
Security 2012 group infect computers unnoticeably with the help of Trojans. Vista
Security 2012
is also distributed through fake online scanners, flash updates, misleading pop-ups that appear
when
you are browsing; so make sure that your anti-spyware is usually updated!
Having infiltrated the targeted computer,
Vista Security 2012 will start causing numerous
problems though it will try to convince you that it is definitely needed.
Being quite hard to
remove, this scam displays lots of false spyware detection reports and fabricated scanners
that
will announce the same thing. This unpaid activity also includes continuous pop-up ads
and the takeover of your
browser to interrupt your normal PC functions. Going no further, Vista
Security 2012 will say that for elimination
of these problems, you first have to register its “full”
version (nd now it should become obvious that it
wants your money only). Vista Security 2012
should not be left inside your PC because it will let other scams reach
your machine and
also starts fraudulent activity. Whenever you see it, don’t take seriously anything it tells
and
stay away from it and its websites. Make sure that you remove Vista Security 2012 as soon as
possible if it's
on your machine.
     
8:22 pm edt
7/21/2011
SecurityTool21/07/11 - Security Tool is a rogue antivirus application that deliberately gives reports of false
system security threats on your computer and displays fake security alerts or notifications to
make you think your
PC is infected with malware. The misleading application is from the same
family as Total Security 2008 and System Security.
When installed, SecurityTool will be configured to start automatically when you log on into
Windows. Then it
will imitate system scan and display a variety of infections that can't be
removed unless you purchase the program. The
files detected during the scan are either
harmless or legitimate system files and can't cause any damage to your computer.
Security Tool is pushed through the use of Trojans, fake online anti-malware scanners and other
malicious
software. It is installed along with Trojans FakeAV that display fake security warnings
and promote Security Tool malware.
Once running, the bogus program will block legit programs
(especially anti-virus software). Another interesting thing
is that if you click on Updates button,
you will see "Updating", but actually there is no network activity.
It's just another argument why
Security Tool is classified as a rogue security application. What is more, this parasite
will
impersonate Windows Security Center and constantly display warnings/notifications
about serious security threats
and privacy issues. It may claim that your computer is under
attack by an Internet virus or that private data can be
stolen. Remove this malware with one of
the automatic removal tools below.
Security Tool properties:
• Changes browser settings
• Shows commercial adverts
• Stays resident in background
     
5:07 pm edt
Trojan-PSW.Win32.Dripper
4:52 pm edt
Zentom System Guard
21/07/11 - Zentom System Guard is a program which you should never spend money on.
Belonging to the category of 'rogue anti-spywares' and hailing
from the same family as
Antimalware Doctor, this scareware has been actively distributed with the help of Trojans
or
through misleading websites. Zentom System Guard on its “official” domain offers to download
its
unregistered version for absolutely free. However, either installed manually or without any
user’s permission it
starts fradulent acions. Its strategy involves specific modifications to a target
computer’s registry while inventing
some harmless files that later will be detected as malware.
When Zentom System Guard is installed onto your PC,
it starts interrupting with false positives
reporting tons of viruses detected. Phony alerts, fabricated virus scanners
and other notifications
are nothing but scam because their function is to encourage you to start thinking about the
program which will fix everything. Zentom System Guard claims that it is definitely the best
removal tool for these
trojans, keyloggers and spyware but before getting it installed asks paying
the money. However, these detections should
be simply ignored because sometimes they may
even be simple your system files.
Warning! Removed attack detected!
Zentom System Guard has detected that somebody is trying
to stole Your private
data remotely via Trojan.Win32.Generic!BT.
Transfer for Your private data via internet will
start in: 10 seconds
We strongly recommend You to block attack immediately.
Zentom System Guard – Hacker attack detected
Your
computer is subjected to hacker attack. Zentom System Guard has detected
that somebody is trying to transfer Your private
data via internet. We strongly
recommend you to block attack immediately.
Firewall file transfer detected
Warning!
Infections on your PC can cause:
- Applications won’t start
- Unwanted advertising displaying
- Loss
of Internet communication
- Lost documents and settings
- Some files can disappear from PC
- You need a registered
version of Zentom System Guard to remove
these infections.
Click “Remove threats” to activate
protection and eliminate these
security hazards.
Warning! Threat detected!
Threat module detected on your PC!
Zlob.Porn.Ad threat has been
detected. This threat module advertises
websites with explicit content. Be advised of such content being
possibly
illegal. Please click button below to locate and remove this
threat now.
Win32.Vitro
21/07/11 - Win32.Vitro is a very dangerous trojan virus. Just like trojan Vundo and Zlob,
Win32.Vitro can be obtained by visiting various noxious websites.
Mainly, Win32.Vitro is
promoted on websites that offer free online movies. In order to watch those movies the visitor
has to download certain video codec. However, it's not a real video
codec, but trojan
Win32.Vitro. Once active, Win32.Vitro performs various misleading actions. It downloads and
installs additional malware and spyware without the user's permission.
What is more, it
advertises rogue anti-spyware applications such as Antivirus 360 and System Protector.
Win32.Vitro must be removed at
earliest stage, because removal delay will cause even more
damage to the system. Use one of the automatic removal tools
listed below.
Win32.Vitro properties:
• Changes browser settings
• Shows commercial
adverts
• Hides from the user
• Stays resident in background
     
7/20/2011
QuestScan
20/07/11 - QuestScan is definitely an unwanted program that belongs to a category of adwares
known to begin their annoying activity as soon
as they enter targeted PC. Being associated with
various insecure downloads, QuestScan presents itself as a reputable
optimizer of search bar
functions. However, if you have this adware on your machine, you already aware of how
annoying
it is. Do a scan with Spyware Doctor (or any other automatic removal tools) and
remove QuestScan just after its
appearance.
A QuestScan infection completely takes over your computer: it starts continuous redirections,
displays
misleading pop up ads and interrupts every time when you start using web. You should
not hesitate and remove QuestScan
because it will continue its activity.
QuestScan properties:
• Changes browser settings
• Shows commercial adverts
     
Antivirus Action20/07/11 - Antivirus Action is a high-risk rogue spyware which appears to be created after its
“famous” forerunner Security Suite which
is known to have infected thousands of PCs. Antivirus
Action is presented as a critical malware not only for typical
malicious capabilities, like its
secret infiltration, annoying system scanners or fake alerts. This scamware is also
capable
enough to disable users from the Internet, block all security software detected and let more other
viruses
inside. Antivirus Action will ask for specialized capabilities when you try to remove it
because it is not removable
through standard uninstall option.
Being distributed through fake video codecs or misleading online scanners, Antivirus
Action
additionally starts its misinformation stage where an infected system is completely bombarded
by virus detection
alerts. These notifications continuously interrupt browsing the web,
and every time they appear they declare numerous
viruses detected, for example:
Windows
Security Alert
Windows reports that your computer is infected. Antivirus software helps to protect your
computer
against viruses and other security threats. Click here to scan your computer. Your
system might be at risk now.
Security Warning
Application
cannot be executed. The file notepad.exe is infected. Do you want to activate your
antivirus software now.
Antivirus Action's strategy is clear and obvious: being a commercial project, it asks payment (of
money) for
its so-called services and offers you updates to 'Antivirus Action Lite, Antivirus Action
Standart or Antivirus
Action Ultimate'. However, this scam has no spyware detection or removal
engine, so it won’t be able to remove
any computer virus. In addition to the above mentioned
facts, this virus has a great impact on the computer’s performance,
so you should eliminate it as
soon as it gets on your computer. It’s highly recommended to use a reliable anti-spyware
and
remove Antivirus Action with all its additional files.
Antivirus Action properties:
• Shows commercial
adverts
• Connects itself to the internet
• Stays resident in background
     
7:44 pm edt
Security Solution 201120/07/11 - Security Solution 2011 is a rogue antispyware application promoted through the use
of Trojans and advertisements that pretend to be online
virus scanners. It uses misleading
techniques to make it difficult to remove it. The rogue disables Task Manager and
other system
utilities so that you cannot end the processes associated
with this fake security program. It
terminates known security software to protect itself from being removed. Security
Solution 2011
automatically scans your computer for viruses and
displays a list of non-existent infections. If
you attempt to remove any of these infections, though, it will state that
you first need to
purchase the program to do so. Please do not purchase this rogue program and use an
automatic
removal tool to remove this program from your computer.
     
7:26 pm edt
WI345d
20/07/11 - WI345d is just another fake threat generated by rogue anti-spyware program called
Windows Security Suite. Usually, this fake
threat is displayed in fake security alerts. Here's one
of those alerts:
"Windows Security Alert To
help protect your computer, Windows Firewall has blocked some
features of this program. Do you want to keep blocking
this program? Name: WI345d; Publisher:
Unknown… Windows Firewall has blocked this program from accepting connections
from the
Internet or a network. If you recognize the program or trust the publisher, you can unblock it.
When should
I unblock a program?"
No matter what you click in this fake alert, you will be taken to the homepage or pay
page of
Windows Security Suite. Most importantly, don't purchase this program. Please use one of the
automatic removal
tools below to remove Windows Security Suite and its related malware form your computer.
WI345d properties:
• Changes browser settings
• Shows commercial adverts
• Stays resident in background
     
7/19/2011
RegDefense
18/07/11 - RegDefense is a misleading Windows registry cleaner that reports false scan results
and prompts the user to buy a full version
of the program to remove the threats and errors. This
application
must be manually installed. It can be downloaded form regdefense.com. Once
installed and active, RegDefense will scan
your computer and display a variety of system errors,
registry
problems, file references that must be fixed to ensure integrity of your computer.
However, you should avoid RegDefense
2009 and remove it if it is already installed on your PC.
     
XP Internet Security
18/07/11 - XP Internet Security is a bogus security software that at first glance might look like a
legitimate
anti-spyware program but in reality it's just another scam trying to steal money from
inexperienced computer users. Once
installed and active, it will be automatically configured to
scan your computer for malware every time Windows starts.
Of course, this fake program only
imitates a system scan and after all reports false computer threats that cannot be
removed with
a trial version of the program so you will be prompted to pay for a full version of of the bogus
software.
XP Internet Security is a total scam, don't buy it and instead remove this infection from
your computer on detection.
And by the way, if you have already purchased it, contact your
credit card company immediately and dispute the charges
if it's not too late.
While XP Internet Security is running you will notice that your computer will begin to run
slower.
This is because the program is always running in the background while using your computer's
resources. XP
Internet Security will also display many fake security alerts and impersonate
Windows Security Center to make the whole
scam look more realistic and to finally convince
you into believing that your computer is badly infected. Furthermore,
the rogue program will block
anti-virus and anti-spyware software and hijack Internet Explorer. This hijacking consists
of
XP Internet Security randomly displaying a message into Internet Explorer stating that the page
you are visiting
has been blocked due to malware activity or other security threat.
     
WinPC Defender18/07/11 - WinPC Defender is another fake anti-spyware application. The main goal of this
parasite is to ruin and compromise system integrity
and security. WinPC Defender is a clone of
malicious and infamous application called XP Police Antivirus. This parasite enters the system
after the installation of trojan application
that pretends to be a video codec.
Once installed and active, WinPC Defender performs fake system scan and basically
generates
misleading pop-up windows and fake error messages attempting to scare the user and hopping
that he will
purchase a licence of WinPC Defender. However, WinPC Defender is totally
worthless application and should be removed immediately after first appearance. It is obvious
that this rogue is unable
to detect and of course to remove any kind of infections. We strongly
recommend to remove WinPC Defender from the system
as soon as possible after detection.
Removal delay can only worsen the situation.
WinPC Defender
properties:
• Changes browser settings
• Shows commercial adverts
• Connects itself
to the internet• Stays resident in background
     
12:26 am edt
7/18/2011
Vista Internet Security 2010
18/07/11 - Vista Internet Security 2010 (can be also called as Vista Internet Security or Vista
Internet Security 2011) is a rogue anti-spyware
program that simulates a system scan and
reports false scan results just to scare you and make you think that your computer
is infected
with Trojans, worms and other malware. Once installed, it will display fake security alerts or
notifications
and then inform you that you need to pay money to register the program if you want
to remove the infections and computer
threats, which of course do not even exist. Do not pay for
this software and get rid of Vista Internet Security 2010
form your computer upon detection.
Vista Internet Security 2010 displays warnings and notifications about
serious security threats
and privacy issues. It will also state that it has detected many critical spyware objects and
that
these objects can expose private information. Of course, that's not true. This is just a part of
whole scam.
Besides, no matter what you decide to do, it will ask to pay for a full version of the
program to protect your computer
from malware and possible attacks from the Internet. Just
ignore all of this. Remove Vista Internet Security 2011 as
soon as possible!
Vista Internet Security 2010 properties:
• Changes browser settings
• Shows commercial adverts
• Connects itself to the internet
• Stays resident in background
     
XP Virus Protection18/07/11 - XP Virus Protection is another rogue anti-spyware application. It is very similar to Total
Virus Protection. Probably, those two fake
spyware removers were created by the same group of
scammers. The main goal of this parasite remains unchanged. It uses
scare tactics in order to
steal money from naive users. XP Virus Protection can also be named Vista Virus Protection
depending on the operating system.
XP Virus Protection can be installed automatically without user's permission.
All the hard work is
done by trojans, mainly Zlob or similar. Once installed and active, XP Virus Protection floods the
system with fake pop-up windows and security notices. Of course all those infections are
feigned, that's why users
have to ignore them. However, scammers keep advertising XP Virus
Protection and suggest to a buy full version of this
worthless product, because trial version has
several removal limitations.
Obviously, this is a fraud. It
is highly recommended to remove this parasite as soon as possible,
otherwise important private data can be at great risk.
XP Virus Protection properties:
• Changes browser settings
• Shows commercial adverts
• Connects itself to the internet
• Stays resident in background
     
11:03 pm edt
7/17/2011
GMODULE.DLL
An engineering student Conducting cryptography research, downloaded
a program from a
website that also offered free movies, music and software. The site required the client to
download
new software (to her system) to allow complete access to this experience. The
problem... this site was launching a social engineering
attack and the program she
downloaded is malicious.
GMODULE.DLL
The 'gmodule.dll'
is the dll support file found in many types of Windows operating systems
(Windows Server 2008, 7 Professional - 7 Home
Edition, Vista, and XP Pro - Home Edition).
It plays an important role for the programs which require 'gmodule.dll' in
order to function
properly. This file can be easily infected and changed (or even replaced) by Trojans or other
malware
programs which results in gmodule.dll errors.
'GMODULE.DLL'
(upper case) functions as a virus file. This attack primarily targets Windows
users and it has proven to be very effective.
It enabled a COM object on the system, enabled
an In Process program (Common with the process as DLL Injections), enabled
Pop-up
windows with AD, gathered email addresses (and personal information), executed a process
(sending MIME email),
executed a process which enabled a COM object in the system to
create other processes on the disk, used IRC protocol
to communicate with other computers
(IM chat rooms, etc) and used special functions to hide itself from user control
panel and
processes list.
Social Engineering
Attack
Users still have to worry about
drive-by downloads (many of which target Windows IE) and
browser bugs, but they must also consider themselves. Many (about
5%) will ignore browser
warnings and download the malicious software (usually Trojan Horses) programs anyway.
Everyone
should always keep their antimalware software up-to-date and should run virus,
spyware and malware checks on any software
downloaded onto their systems.
The genius of the
cracker is to simply ask the users to download the program... they are
hacking the people! Why sneak programs onto a
system when I can get the user to give
access of their own free will. Browsers are a bit more secure and software companies
constantly push patches but many users still are not very good at applying patches.
Unfortunately, they love to
download things that they want!
The attackers have
figured out that it's not that hard to get users to download Trojans. You
might get a message from a friend telling you
to go and view a video. When you click on the
link, your told that you need to download a program (maybe some sort of
video playing
software) in order to watch. That software is actually a malicious program.
Social-engineering hackers also try to infect victims by hacking into Web pages
and popping
up fake antivirus warnings designed to look like messages from the operating system.
Download these
and you're infected. The criminals also use spam to send Trojans, and they
will trick search engines into linking to
malicious websites that look like they have
interesting stories or video about hot news such as the Casey Anthony release,
The Royal
Wedding or the death of Osama bin Laden.
Removing 'GMODULE.DLL'
1.
For Windows Me and Windows XP users, System Restore must be disabled to prevent the
GMODULE.DLL virus
from restoring itself.
2. Update installed antivirus programs.
3. Reboot computer in SafeMode.
4. Run your antivirus program (automatic scan from programs like PCtools, Kaspersky,
Norton,
AVG, BitDefender, Panda, etc.) with a full system scan and clean/delete all infected file(s).
5. Delete/Modify any values added to the Registry.
6. Restart the computer normally.
     
7/16/2011
W32.Blaster.Worm
14/07/11 - The worm attempts to perform a Denial of Service (DoS) on
the Microsoft Windows
Update Web server (windowsupdate.com).
This is an attempt to prevent you from applying a
patch on your computer against the DCOM RPC vulnerability. W32.Blaster.Worm is a worm that
exploits the DCOM RPC vulnerability (described in Microsoft Security Bulletin MS03-026) using
TCP port 135. This worm attempts to download
the msblast.exe file to the windowssystem32
directory and then execute it. Remove Blaster Worm (using an automatic removal
tool) from
your system as soon as possible.
     
Antivirus 7
14/07/11 - Antivirus 7 (also called as Antivirus 7) is a totally misleading anti-spyware
software
that just like many rogue applications seeks to convince users that they really need to purchase
its commercial
version. Every time Antivirus 7 infects computers, it announces hundreds of cyber
threats detected though in fact this
application has nothing to do with PCs security. Keep in mind
that Antivirus 7 has no spywares’ detection or removal
engine, so don’t fall into it and remove if
the program is spotted on your machine.
Antivirus 7 is mostly
propagated through fabricated online scanners and trojans viruses that hide
in video codecs foolishly required for watching
videos online. When the malware is installed, it
starts using malicious techniques trying to convince users that they
really need to purchase it.
Antivirus 7 classically loads deceptive pop up ads telling users about cyber threats they
have
and additionally redirects them to the websites actively promoting malware as well. Redirections
are the cause
of the browser hijacking technique which is also used by Antivirus 7.
Once on board, the trial version of Antivirus
7 will run permanently while people browse the Web.
Victims will be annoyed to death with these bogus security alerts
and system scanners reporting
the same fake viruses "detected" and pushed straight away into purchasing it.
Instead of taking
the suggesstion to buy this useless commercial version, remove Antivirus 7 immediately. Here
are
the examples:
Internet Shield: Identity theft
attampt detected
56.12.121.12
Warning! Identity theft attempt detected
Please click "Prevent
attack" button to heal all infected files and protect your PC
Security advisor: Important updates available
Attention! New important updates available
Always install latest updates to enhance your computer secutity and performance
Resident Shield: New
virus detected
Warning! New virus detected
Please click "Remove All" button to heal all infected
files and protect your PC
In truth, infections listed by Antivirus 7 are invented by the same scam or are even
normal and
important system files, so deleting them is absolutely wrong idea. Don’t pay for this rogue anti-
spyware and get rid of Antivirus 7 and all its associated data. Scan your computer for Antivirus 7
as soon as you
notice its misleading activity on your machine.
     
AntiMalware
14/07/11 - AntiMalware is a misleading application that reports false infections/system
security
threats, displays fake security alerts, uses browser hijacking and other methods to trick you into
believing
that your computer is infected with Trojans, Worms and other viruses. This misleading
application is a clone of the rogue
security program called Active Security. So, obviously it has
many
similarities with Active Security malware. AntiMalware is promoted mostly through the use
of Trojans that comes from
fake online scanners, fake online video websites or bundled with
other malicious software. When running, the rogue program
will perform fake system scans and
then prompt you to pay for a full version of the program to remove the threats which
do not
actually exist. This is a scam; do not purchase this bogus application. Instead, uninstall
AntiMalware from
your computer as soon as possible.
     
Unknown Win32/Trojan
14/07/11 - Security experts
warn that one day you may get unexpected alert reporting Unknown
Win32/Trojan found on your computer. Some of such alerts may even have a title with Microsoft
Security Essentials name but
they are not legitimate! Unknown Win32/Trojan is reported by
Fake MSE and ‘detected’ with the goal being
to make you concerned about your computer and
ultimately prompting you to purchasing the rogue program.
The
trick about Unknown Win32/Trojan is that users are offered an opportunity to purchase
‘licensed’ software
withch the promise to remove this nonexistent trojan. However, every time
Unknown Win32/Trojan is announced, a different
anti-malware is offered for its removal. And you
should have heard about Windows Easy Warden or Windows Armour Master
that have been
promised to help with Unknown Win32/Trojan removal.
We highly recommend you running a reputable
anti-spyware (Spyware Doctor recommended) to
fix your PC from dangerous trojans that mislead users about Unknown Win32/Trojan
detection.
     
Win 7 Security
14/07/11 - Win 7 Security is a rogue anti-spyware program that gives false or exaggerated reports
of threats on your computer and displays
fake security alerts to make you think that your PC is
infected with malicious software. This fake program comes from
fake online scanners, malicious
or infected sites, through software vulnerabilities. It may be also promoted on
popular social
networks. Once installed, Win 7 Security will run a fake system scan and display a list of false
malware
infections on your computer. Then it will ask you to pay for a full version of the program
to remove the infections.
As you can see, Win 7 Security is nothing more but a scam. Don't
purchase it. Get rid of Win 7 Security virus as soon
as possible.
As a typical rogue anti-spyware program, Win 7 Security will constantly display fake security
alerts and pop-ups claiming that your computer is infected or under attack by an Internet virus or
from a remote computer.
One way or another, such false information should be ignored just like
the false scan results. Furthermore, the rogue
program will block legitimate antivirus applications
and hijack Internet Explorer. In some cases, it blocks security
related websites too. It goes
without saying that you should remove Win 7 Security from your computer upon detection.
That's why we strongly recommend you to use an automatic removal tool.
     
7/14/2011
System Repair 13/07/11 - System Repair is a fake system optimization program that displays fake error
messages
and alerts to make you think that your computer has serious problems. It uses a
typical technique of most rogue programs
and uses numerous popups and all kinds of security
alerts in order to scare you and make you think your system is severely
infected or has many
other security or privacy issues. Then System Repair prompts you to pay for a full version of the
program to fix the errors which do not even exist. We strongly recommend you to remove
System Repair from your computer.
System Repair enters the system through Trojans... once it lays down in the system, it
completely takes control.
The program runs system scanner and (later on) reports critical errors
'detected' on your system. It warns you that some
of your private data might be lost because of
the lack of free space, RAM memory usage, etc. The truth is that it is
fake information and
System Repair only wants you to believe your system is infected. System Repair will offer you
purchasing rights (for a full version) of its program with a promise that this will fix everything.
However, its
real intention is to receive your money, but in return you won’t get anything. Do not
buy this rogue program. It
won't help you. In order to stop all malicious activities on your
computer you should remove System Repair as soon as
possible. The best solution is using a
reputable antispyware program which would deal with this program (and other malware
it has
brought in) quickly and easily.
  
6:00 pm edt
Win 7 Antispyware 2012 13/07/11 - Win 7 Antispyware 2012 is a rogue antispyware program. As a typical rogue
anti-spyware program, Win 7 Antispyware 2012 is usually distributed
and installed through the
use of Trojans that come from misleading websites that pretend to be online anti-malware
scanners. What is more, trojans can also come bundled with other malicious software. On way
or another, when this trojan
virus is installed, it will download and install Win 7 Antispyware 2012
onto your computer. Once installed, Win 7 Antispyware
2012 will be configured to run
automatically each time you logon into Windows. While running, this fake antivirus program
will
simulate a system scan and detect legitimate Windows files or non-existing files as infections.
Furthermore,
Win 7 Antispyware 2012 will flood your PC with popups and fake security warnings
to mislead you into thinking that there
are various harmful files on your computer. This is done to
create a reason for the user to buy Win 7 Antispyware 2012
"licensed version", which is
completely and utterly non-functional. If you buy it - consider yourself scammed.
As you can
see, all those fake alerts false scan results are displayed only to scare you. If you are infected
with
this rogue, please remove Win 7 Antispyware 2012 from your computer with an automatic
removal tool.
  
5:43 pm edt
Virus Sweeper
13/07/11 - Virus Sweeper is a rogue anti-spyware application, fake spyware remover. It is just a
new version of another notorious rogue - Virus
Doctor. Virus Sweeper is advertised through the
use of Trojans that display misleading alerts and security notifications
stating that user's
computer is infected with spyware, malware or other similar parasites. If user clicks on even one
of those alerts, he will automatically download and install Virus Sweeper into his computer. The
main goal of Virus
Sweeper is to display falsified alerts and to convince the user to buy a full
version of this totally worthless application.
Once installed and active, Virus Sweeper is configured to run automatically every time a users
computer starts
up. Then it performs fake system scan and displays various bogus results.
Mainly, Virus Sweeper states that user's
PC is seriously infected and has many security issues.
Virus Sweeper floods the system with pesky pop-up windows and
similar fake notifications. It
might even decrease system performance and disorganize the functionally of security
applications. It is very important to ignore all disinformation provided by Virus Sweeper and
remove it from the system
as soon possible after detection, because this parasite won't help you
to remove those infections. It's a scam designed
to steal money from naive people. Please use
one of the automatic removal programs (below) and remove Virus Sweeper
once and for all.
  
Antivirus XP 2010
13/07/11 - Antivirus XP 2010 is a rogue anti-virus application that claims to scan your computer
for malware, but in reality it only imitates legitimate
security software and tries to trick users into
thinking that their computers are badly infected. The goal is one - to
trick as many people as
possible into purchasing the so-called "full" version of the program which obviously
doesn't even
exist. Antivirus XP 2010 is "pushed" through the use of bogus online scanners and fake
video/warez websites. When running, this parasite will flood your computer with fake security
alerts and notifications stating that the system is compromised. It will even impersonate
Windows Security Center.
The worst thing about this virus is that it blocks almost all programs,
not to mention 'security software' (anti-virus
and anti-spyware programs are blocked in the first
place). It also blocks Task Manager, Regedit and other Windows functions.
Unfortunately, Antivirus XP 2010 removal is not as easy as you would expect it to be. As we
know it blocks
all .exe files, so obviously you won't be able to install or run any anti-malware
program. The virus will probably not
allow users to download any anti-malware programs. You
can attempt to remove the infection manually, or you
can use another system to download a
program (like Spyware Doctor, AVG, BitDefender, etc), update the signatures and run a full
system scan.
  
7/13/2011
Windows Easy Warden
12/07/11 - Windows Easy Warden is a fake security program that is promoted via trojans and
other malware. It imitates system check and states that
your computer in infected with spyware.
In order to remove the supposedly found infection and remove viruses you have
to pay for a full
version of Windows Easy Warden. Of course, you shouldn't do that because this program is a
scam.
Fake scan results is a method to scare you into purchasing the program. You should
remove Windows Easy Warden from your
computer manually or use an automatic removal tool
below.
Windows Easy Warden will constantly display fake
error messages stating that your computer
is infected with malicious software. It will rate major components of your
system by given scores.
They are usually very low. Once installed, it will prompt you to start your computer in protected
mode to ensure that your computer is properly protected against possible attacks and malware.
As you can see, Windows
Easy Warden is nothing more but a scam. It displays fake error
messages and security alerts to make you think that your
computer in infected. Then it prompts
you to pay for a full version of the program to clean up the computer. Do not buy.
Instead,
remove Windows Easy Warden from the system as soon as possible.
  
XP Home Security 2012
12/07/11 - XP Home Security 2012 is a rogue anti-spyware program that simulates a system
scan and reports false scan results just to scare you and make
you think that your computer is
infected with Trojans, worms and other malware. Once installed, it will display fake
security
alerts or notifications and then inform you that you need to pay money to register the program if
you want
to remove the infections and computer threats, which of course do not even exist. Do
not pay for this software and get
rid of XP Home Security 2012 form your computer upon
detection using the removal stated guide below.
XP Home
Security 2012 displays warnings and notifications about serious security threats and
privacy issues. It will also state
that it has detected many critical spyware objects and that
these objects can expose private information. Of course,
that's not true. This is just a part of
whole scam. Besides, no matter what you decide to do, it will ask to pay for
a full version of
the program to protect your computer from malware and possible attacks from the Internet. Just
ignore all of this and read the removal instructions carefully. Remove XP Home Security 2012
as soon as possible!
  
Anti-Malware Lab
12/07/11 - Anti-Malware Lab is a typical fake anti-spyware program; it imitates a system scan
and claims that your computer is infected with malicious software. The bogus program creates
harmless files on your computer and then detects
those files as viruses. Finally, it asks you to
pay for a full version of the program to remove the infections and to
make your computer more
secure. Moreover, Anti-Malware Lab displays
fake security warnings and and pop-ups claiming
that your sensitive information can be stolen or that your PC is under attack from a remote
computer. It goes without saying that you should
remove Anti-Malware Lab from your computer
as soon as possible.
Anti-Malware Lab is promoted mostly
through the use of Trojans, fake online scanners and other
misleading
websites. While running, it will block legit antivirus and anti-spyware programs,
disable task manager, registry editor
and other useful system tools to protect itself from being
removed.
It will hijack Internet Explorer and block security related websites or redirect to various
misleading websites that
promote rogue security software. As you can see, Anti-Malware Lab
is nothing more than a scam. If you find that your computer is infected with this bogus program
please remove
Anti-Malware Lab from your computer either manually or with an automatic
removal tool. If you have already purchased
this fake program, then contact your credit card
company immediately
and dispute the charges.
  
Vista Antivirus 2012
12/07/11 - Vista Antivirus 2012 is a rogue security program that is promoted through the use of
Trojans. When this fake program is running, it will
simulate a system scan and display a list of
false system security threats. Vista Antivirus 2012 will display fake security
warnings and
impersonate Windows Security Center to make this scam look more realistic. It will also hijack
your
web browser and block antivirus and anti-spyware programs. Finally
the rogue program will
ask you to pay for a full version of the program to remove the non-existing infections. Don't
purchase it and remove Vista Antivirus 2012 from your computer upon detection.
Vista Antivirus 2012 protects
itself quite effectively. It blocks legitimate security software and
hijacks web browsers. In some cases it blocks all programs, not only anti-virus or anti-spyware
software. What is more,
it will detect many well known and reputable websites as harmful and
display fake security alerts stating that you
may infect your PC if you open a particular website.
And of course, it disables certain Windows functions such as Task
Manager. It's possible to
remove it manually, but you have to
re-enable those Windows functions at first. You may also
download an automatic removal tool, but again have to fix some
registry entries and terminate
the main process of Vista Antivirus 2012 to be able to use malware removal tool. As you can
see, Vista Antivirus 2012 is nothing more but a scam. If
you have already purchased this rogue
program then contact your credit card company and dispute the charges.
  
7/12/2011
Windows Armour Master11/07/11 - Windows Armour Master is a rogue anti-spyware program. It is promoted through the
use of fake online scanners and via infected websites. Once
installed, this rogue program will run
a fake system scan and then will state that your computer in infected with trojans,
worms and
other viruses. Windows Armour Master will prompt you to buy the full version of the program to
remove
found malware and to ensure system protection against other threats. However, you
shouldn't purchase this rogue program.
It's a scam.
While running, Windows Armour Master will display a bunch of fake security alerts and pop-ups
stating that your computer is infected or under attack from a remote server. The scammers want
to make you think that
your computer is infected with and to further scare you into buying their
useless program. What is more, Windows Armour
Master may block practically all programs on
your computer saying that they are either infected or may cause serious
damage to the system.
Last, but not least, Windows Armour Master will hijack Internet Explorer and redirect you to
various misleading websites that may harm your computer or install other malware. As you can
see, Windows Armour Master
is nothing more but a scam. If you find that your computer in
infected with this rogue program then, we strongly
recommend you remove this malware from
your PC using an automatic removal tool.
  
10:23 pm edt
Win 7 Security 2012
11/07/11 - Win 7 Security 2012 is a rogue anti-spyware program that reports false system
security
threats to make you think that your computer is infected with malware when the only
actual infection is Win 7 Security
2012 itself. It also displays fake security alerts and pop-ups
stating that your computer is under attack from a remote
computer or that your sensitive
information can be stolen. Finally, it will ask you to purchase the program to remove
the
infections which don't even exist on your computer. As you can see, Win 7 Security 2012 is a
total scam. Please
don't purchase it and uninstall this bogus program from your computer upon
detection.
Win 7 Security 2012
is a typical rogue program promoted through the use of Trojans and other
malicious software. Trojan horses usually come
from fake online anti-malware scanner or other
misleading web sites. Once running, Win 7 Security 2012 will scan your
computer for malware
and display a list of infections that supposedly can't be removed with a trial version of the
program, so you have to buy it. However, you already know that this is nothing more but a scam.
Win 7 Security 2012
won't make your computer more secure nor will it remove malware from
your computer. What is more, it will block legitimate
programs and hijack Internet Explorer to
protect itself from being removed. As you can see, this fake program is not
only very annoying
but also dangerous. It may install additional malware on your computer. If you find that your PC
is infected with Win 7 Security 2012 please remove this infection from the system either
manually or with
an automatic removal tool. If you have already purchased this program then you
should contact your credit card company
and dispute the charges.

Total Security Protection Center
11/07/11 - Total Security Protection Center is a fake security notification
generated by rogue
anti-spyware application called Total Security. The main purpose of this alert notice is to
promote the full version
of this parasite. Mainly, it states that user's PC is not properly
protected and suggest to buy Total Security license.
Total Security Protection Center alert
reports:
"Total Security Protection Center
Security
Notice!
To protect your computer, make sure the three security essentials are turned ON. If the settings
are not ON, follow the recommendations. To return to the security senter later, open Control
Panel.
Protection
Center reports that 'Total Security' is not activated. Antivirus software helps to prevent
your computer against viruses and other security threats.
Click Recommendations for the
suggested actions. Your system migth be at risk now.
Your version of TotalSecurity
still not activated yet.
Click here to get Total Security License
Top Threats in the last 24 hours
Virus
count
1.wm32/Netsky.Q worm 7879
2.Wn32/Stration.XW worm 1337
3.Win32/Netsky.D worm 721
4.Win32/bagle.HE
worm 491
5.Win32/Mytob.BK worm 221"
TotalSecurityProtectionCenter alert notice is only one of possible
fake pop-up windows.
Probably, user will get more similar notifications once Total Security is inside. The best option
is this situation would be manual removal of Total Security. Because user won't be able to get
rid of fake Total
Security Protection Center alert if Total Security is still active.

Red Cross Antivirus
11/07/11 - Red Cross Antivirus is a rogue antivirus program that reports false system security
threats to make you think that your computer is infected. Recently, this rogue program is being
distributed through the
use of the fake Microsoft Security Essentials Alert Trojan. Red
Cross
Antivirus is a typical rogue program just like Peak Protection
2010, Pest Detector 4.1, Major
Defense Kit or AntiSpy Safeguard. Once installed, it will pretend to scan your computer and after
that it will list numerous infections that supposedly can delete
your important files or steal your
sensitive information. Don't worry, the scan results are false. You can safely ignore
them. This
also applies for fake Red Cross Antivirus security warnings and pop-ups. Some of those fake
alerts will
state that your computer is under attack from a remote computer and that the Red
Cross Antivirus has blocked a remote
login attempt to your computer. Please don't purchase
this bogus program. Remove Red Cross Antivirus from your computer
either manually or with an
automatic removal tool. While Red Cross Antivirus is running, it will also block legitimate
programs and security related websites. It will probably block Task Manager and Registry Editor
too.

Windows Accurate Protector11/07/11 - Windows Accurate Protector is a rogue program that is promoted through the use of
Trojan which impersonates the Fake
Microsoft Security Essentials Alert. This Trojan display a
fake Microsoft Security Essentials Alert pop-up stating that
it has detected an Unknown
Win32/Trojan on your computer. Once installed, Windows Accurate Protector will show up on
your computer screen before your
normal Windows desktop. It will prompt you to scan your
computer and after the fake scan it will report numerous infections
and system errors that may
cause serious problems to your computer. This program
is a scam. It won't remove any
infections from your computer simply because they do not even exist. It goes without saying
that you should not purchase this program for any reason.

7:57 pm edt
XP Antivirus 2012Monday, July 11, 2011 4:07 AM - XP Antivirus 2012 is a deceptive and quite sophisticated rogue
anti-spyware program which applies the basic tricks of scams from this
category. Though it
declares to be a powerful virus remover, keep in mind that this program is the only one that
needs
to be eliminated because it reports invented viruses. To be more precise, XP Antivirus
2012 firstly will create numerous
harmless files that it will drop in the infected computer's
system. Then this scam will pretend to scan your computer
and immediately will report
numerous viruses that in reality are nothing else but these earlier created files. Some of
its alerts
may state about Trojan-BNK.Win32.Keylogger.gen threat for making you scared to death and
push you into
purchasing its license which will be offered additionally. Pay attention to the fact,
that XP Antivirus 2012 is dangerous
and has nothing to do with computer's protection! XP
Antivirus 2012 program has been manipulating people into believing
it is useful software.
However, this rogue anti-spyware mostly penetrates into a random computer system without the
user's knowledge and approval and opens the backdoor of the system to let more threats in
or allow the scammers to
reach your personal information. All this is done with a help of Trojans
that infect vulnerable systems through fake
video codecs and flash updates. As you can see,
you should not believe XP Antivirus 2012 and its spyware detection reports
as they are fabricated
and have in fact nothing to do with the true condition of machine. Don't buy this software
though it will definitely promise to fix your computer, but remove XP Antivirus 2012.
7:31 pm edt
Trojan-BNK.Win32.Keylogger.genSunday, July 10, 2011 5:07 PM - Trojan-BNK.Win32.Keylogger.gen is a dangerous infection that
spreads through XP Internet Security 2010 rogue anti-spyware program. It is not a real
virus and
it appears only if the system is infected with XP Internet Security 2010. Once a computer is
infected
with this fake application and you try to browse some Internet website, XP Internet
Security 2010 keeps displaying fake
notifications claiming that your system is infected with
Trojan-BNK.Win32.Keylogger.gen. The warning states that your
private data (passwords, credit
card details, etc.) might be stolen. However, this warning is a total lie.
Trojan-BNK.Win32.Keylogger.gen
was only designed to scare people into thinking it's a
dangerous infection. Such parasite doesn't even exist on your
computer and it is displayed
just because you are infected with XP Internet Security 2010. This is the only application
that must be removed. Once you get notifications that you are infected with Trojan-BNK.
Win32.Keylogger.gen,
concentrate on removing XP Internet Security 2010 application.
5:07 pm edt
Fast TrackerSaturday, July 09, 2011 6:07 AM - From the publisher: 'Managing the
online employee requires
new standards, re-engineered procedures, and intelligent information about employee surfing
patterns. Fast Tracker lets you view employee Internet use and analyze relevant information in
real time, while making more efficient use of
bandwidth. With the intelligence Fast Tracker
provides, you can turn employee Internet use into an asset, not a liability.
'
4:58 pm edt
Win 7 Security 2011Friday, July 08, 2011 11:07 PM - Win 7 Security 2011 is a new malvertised program from the
dangerous Security AntiMalware Guard family of malwares that change their
names according to
the OS which their infected computer runs. This group is represented by such scams like Win 7
AntiMalware
2011, Vista Antispyware 2011 or XP Security 2011. This one (Win 7 Security 2011)
is a similar to other variants
of malwares and shares the same GUI or misleading campaign
based on faked information. Remember that once detected you
MUST ignore its information
given and remove the same Win 7 Security 2011.Win 7 Security 2011 rogue anti-spyware is
distributed through Trojans that enter unprotected systems without any permission of the user
asked. Besides, it can
also be installed with a fake flash update or free online scanner, so watch
out! Having penetrated into your computer,
unregistered version of Win 7 Security 2011 modifies
the system and some its parameters to launch after every computer's
reboot. Then in becomes
capable to interrupt into your normal computers usage and starts its misleading campaign. This
campaign is nothing else but fake system scanners and alerts issuing numerous infections.
However, the truth is that
all these parasites are harmless your system files, so never remove
them. Some examples of such notifications: Privacy
threat! Spyware intrusion detected. Your
system is infected. System integrity is at risk. Private data can be stolen
by third parties,
including credit card details and passwords. Click here to perform a security repair. Stealth
intrusion!
Infection detected in the background. Your computer is now attacked by spyware and
rogue software. Eliminate the infection
safely, perform a security scan and deletion now. So, Win
7 Security 2011 will make you worry about your computer but
later it will offer its help. Malware
starts declaring that its 'registered' version is the only anti-spyware powerful
enough to remove
the threats detected and ...
4:51 pm edt
My Search BarFriday, July 08, 2011 9:07 AM - My Search Bar is a commercial Internet Explorer add-on. This
toolbar allows users to search the web using popular Internet search
engines. However, it also
displays advertising links. My Search Bar doesn't distribute itself and must be manually
installed. Lots of ad-supported application can add it to the system. My Search Bar runs every
time the user launches
Internet Explorer.
4:43 pm edt
Windows Test Master
Friday, July 08, 2011 8:00 AM - Windows Test Master is the member of one of the most
annoying malicious families these days. Just like earlier released members of fake
Microsoft
Security Essentials family, Windows Test Master is also designed to be capable enough to get
inside the
system undetected and the start to mislead its victims about dangerous malware
detected. However, all these 'viruses'
are harmless for legitimate system files so they
should be ignored and never removed from the system. The only thing
that must be eliminated
is Windows Test Master, so you are highly recommended to get a reputable anti-spyware and
delete all infected files and folders. In order to make you concerned, this cyber threat starts
reporting: Microsoft
Security Essentials Alert Potential Threat Details, 'Microsoft Security
Essentials detected potential threats that might
compromise your private or damage your
computer'. Your access to these items may be suspended until you take an action.
Click 'show
details' to learn more. System Security Warning Attempt to modify registry key entries is
detected.
Register entries analysis is recommended. System component corrupted! System
reboot error has occurred due to lsass.exe
system process failure.This may be caused by
severe malware infections. Automatic restore of lsass.exe backup copy completed.
The correct
system performance can not be resumed without eliminating the cause of lsass.exe
corruption. Warning!
Name: firefox.exe Name: c:program filesfirefoxfirefox.exe Application that
seems to be a key-logger is detected. System
information security is at risk. It is recommended
to enable the security mode and run total System scanning Never dream
that Windows Test
Master will help you to keep your PC protected from viruses! It's just another scam that must be
uninstalled from every computer. If you happen to receive some alerts or see scanners from
Windows Test Master that
you never initiated, kee..
Windows Vista Fix
Friday, July 08, 2011 7:35 AM - Windows Vista Fix is a serious problem on everyone's computer
as it infects PC's without any permissions asked and then starts playing
havoc there. Malware
makes users think that their computers have serious hard drive problems but then offers its paid
services for fixing everything. In other words, Windows Vista Fix is one of the best in inventing
fake errors on your
computer that are expected to make you frightened. To make you think that
your computer has a serious problem, Windows
Vista Fix will delete shortcuts found in various
locations, so that you couldn't launch those programs from your start
menu. It is also known to
modify PC's registry which makes this malware launched as soon as PC is rebooted. To stop
this scam, you must remove Windows Vista Fix with all its infected files and folders. If after
removal of this scam
you can't see some of your files and folders, follow our easy steps given in
the end of the article. This program accurately
follows its forerunners that are Windows 7 Fix and
Windows XP Fix. Similarly to these scams, Windows Vista Fix looks
almost the same and acts
identically as well. Just after it manages to get inside (in most cases it is done with a help
of
Trojans), badware starts seeking to get your money. Every time you reboot your PC, Windows
Vista Fix 'scans'
computer's hard drive and can be easily predetermined to return tons of errors.
Some of them will be the ones written
below: Critical Error Hard drive critical error. Run a system
diagnostic utility to check your hard disk drive for errors.
Windows can't find hard disk space.
Hard drive error. Fix Disk, Windows Vista Fix Diagnostics will scan the system to
identify
performance problems. Start or Cancel Windows Vista Fix Diagnostics Windows detected a
hard disk error.
A problem with the hard drive sectors has been detected. It is recommended to
download the following certified software
to fix the ..
Windows 7 Fix
Friday, July 08, 2011 7:15 AM - Windows 7 Fix is almost the same malware as Windows XP Fix
which will also pretend to be a powerful PC optimization tool. Windows
7 Fix will continuously
give you hard drive error reports that will return nothing else but completely fake results that
are
expected to make you purchase this scam. Please, never believe the problems announced on
Windows 7 Fix messages!
These should be only ignored in order to prevent more damage done
to your machine. Additionally, you must remove Windows
7 Fix before it lets more viruses inside
and steals your money together with credit card details. If you notice it, launch
updated Spyware
Doctor immediately and remove Windows 7 Fix without any delay.Windows 7 Fix is all about
deceiving
PC users. It reports multiple hard drive problems found on your computer and then
asks you to make a payment to get them
fixed. This trick is quite usual between such scams
and it can be easily said that all those âerrorsâ found
by Windows 7 Fix are non-existent. To
make you fall into this lie even more, this scamware deletes shortcuts found in
various locations,
so when trying to launch a program from your start menu, none of shortcuts appear. So,
normally,
you would think that something is really wrong with your computer. To push you into
thinking that PC is bundled, this
scam says on its alerts: Windows 7 Fix Diagnostics Windows
detected a hard disk error. A problem with the hard drive
sectors has been detected. It is
recommended to download the following certified software to fix the detected hard
drive
problems. Do you want to download recommended software? Requested registry access is not
allowed. Registry
defragmentation required, Read time of hard drive clusters less than 500% of
HDD space is unreadable, Bad sectors
on hard drive or damaged file allocation table, CPU RAM
temperature is critically high. Urgent RAM memory optimization
is required to prevent system
crash Drive C initializing error Ram Temperature is ..
Windows XP Fix
Friday, July 08, 2011 6:54 AM - Windows XP Fix is a dangerous malware which is categorized
as fake hard disk defragmenter. Though it may look trustworthy, the program
will definitely impact
your PC in the worst way by interrupting you with its continuous hard drive scanners and error
alerts. After making you think that PC has hard disk errors, Windows XP Fix will claim that you
need to pay for its
licensed version. Please, never do this mistake and pay for Windows XP Fix!
It will only steal your money and credit
card details! You must remove this malware as soon as
you notice its fake error reports:Hard Drive FailureThe system
has detected a problem with one
or more installed IDE / SATA hard disks. It is recommended that you restart the system.System
Error An error occurred while reading system files. Run a system diagnostic utility to check your
hard disk drive for
errors.Critical ErrorHard drive critical error. Run a system diagnostic utility to
check your hard disk drive for errors.
Windows canât find hard disk space. Hard drive error. Fix
DiskWindows XP Fix Diagnostics will scan the system to
identify performance problems.Start or
CancelWindows XP Fix DiagnosticsWindows detected a hard disk error.A problem with
the hard
drive sectors has been detected. It is recommended to download the following certified software
to
fix the detected hard drive problems. Do you want to download recommended software?
Windows XP Fix appears to be similar
to another rogue program known as Windows XP Repair.
It is probably the updated version of its counterpart mentioned
because its GUI looks almost
identically. As soon as Windows XP Fix, this application claims to be an efficient instrument
for
keeping computerâs hard drive optimized and safe from problems. However, this is definitely
untrue! Windows
XP Fix modifies the system to launch once PC is rebooted and deletes
shortcuts found in various locations to convince
you that your PC is seriously affected.
Additionally, this...
7/11/2011
Total PC Defender
Thursday, July 07, 2011 10:07 PM - Total PC Defender is a fake antivirus program. Please read
Total PC Defender 2010 removal instructions carefully and remove this virus
from your computer
as soon as possible. The rogue program is from the same family as Desktop Defender 2010.
More
generally speaking, it's nothing more but a typical rogue application that displays
misleading security alerts and reports
false system security threats to make you think that your
computer is infected with Trojans, worms and other malicious
software. When running, it will
imitate a system scan and display numerous infections. Of course, scan results are false.
Then
it will ask you to pay for a full version of the program in order to remove the infections which
actually do
not even exist. [Figure 1. Total PC Defender graphical user interface]What is more,
Total PC Defender will constantly
display fake security alerts stating that your computer is under
attack or seriously infected. It will also claim that
malicious programs that may steal your private
information were detected. The fake notification states:Security Warning!Malicious
programs that
may steal your private informationand prevent your system from working properly are detected on
your
computer.Click here to clean your PC immediately.There are more fake warnings and you
will likely see all of them if
your computer is already infected. However, false scan results and
fake security alerts are not the biggest problem.
The most annoying thing is that Total PC
Defender blocks particular software and disables important system tools or options.
It can
disable system restore and block safe mode too. In some cases it will block all executable
(.exe) files,
so you won't be able to launch any anti-spyware software or malware removal tool.
Try to download and run an automatic
removal tool from this page (provided below). If you can't,
then read further instructions.First of all, you have to
end the main process of Total PC Defender
w..
Windows Salvor Tool
Thursday, July 07, 2011 2:51 PM - Windows Salvor Tool is a rogue anti-spyware program that
displays fake security alerts and non-existent infections. This rogue is typically
installed through
the use of Trojans that come from fake online scanners. Windows Salvor Tool will pretend to
scan
your computer and detect malicious files but not allow them to be removed until the
program is purchased. The rogue program
wants to scare you into purchasing it. If you find that
your computer is infected then use our removal instructions below
to remove Windows Salvor
Tool and related malware automatically using the removal tool given below. While Windows
Salvor Tool is running it will also display fake security warnings and alerts on your computer.
These alerts will state
that an active infection has been found and that you should purchase
Windows Salvor Tool to remove found viruses and
to protect your computer against other
malware. Windows Salvor Tool will also block certain programs saying that they
are infected. It
may hijack your web browser as well. Windows Salvor Tool was created to trick you into thinking
that
your computer has all sorts of malware so that you then purchase it. It is a scam. If you
have already purchased the
program, then you should contact your credit card company and
dispute the charges. To remove Windows Salvor Tool and
the related Trojans, please use the
removal guide below.
Win 7 Internet Security 2012
Thursday, July 07, 2011 2:07 AM - Win 7 Internet Security 2012 is a phony anti-spyware program
that supposedly scans your computer for malware and displays a list of false system
security
threats to scare you into thinking that your computer is infected with worms, trojans, spyware
and other
malware. Then the rogue program prompts to pay for a full version of the program to
remove the infections which don't
even exist and to ensure full system protection against other
malware. This misleading program also displays fake security
warnings and pop-ups claiming
that your computer is badly infected or that your data might be deleted. Don't trust it
and remove
Win 7 Internet Security 2012 from your computer upon detection. Furthermore, Win 7 Internet
Security 2012 hijacks Internet Explorer and blocks almost all sites claiming that they are
infected or compromised
and may infect your computer. It goes without saying that it blocks
security related websites in the first place. Win
7 Internet Security 2012 also blocks antivirus
and anti-spyware applications. It prevents new installation of anti-malware
tools so you will have
to ends its processes first. Otherwise it will continue to block malware removal tools. If you
find
that your computer is infected with this annoying virus, please use the removal instructions
below to remove
Win 7 Internet Security 2012 as soon as possible either manually or with an
automatic removal tool.
XP Security 2012Thursday, July 07, 2011 1:07 AM - XP Security 2012 is a fake security program that pretends to
be a malware removal tool. This rogue anti-spyware usually comes unnoticeably
without any
permission asked, so if you find XP Security 2012 on your computer you are most likely to have
got it
through a Trojan. These Trojans not only install this fake anti-spyware thing but also
change the Registry and drop fake
random files which later are detected as malware. Security
experts announce that when installed on different
OS, XP Security 2012 appears in different
name, though the malcode stays the same. So, when using Win 7 Antispyware name,
the trial
version of this parasite infects only Windows XP OS. Installed without any knowledge and
consent, program
firstly applies the tactics typical for this type of malware. It usually triggers
fabricated general system scans that
return the results which can be easily predetermined.
Don't get surprised after being informed that various threats of
different severity are
detected. XP Security 2012 also generates fake positives that report infections that are expected
to make you doubt about your PC security. Keep in mind that clicking on any pop-up add will
automatically get you into
XP Security 2012 "official" website. These sites must be avoided
because they only aggressively promote its
full commercial version. Don't buy this scam,
because you will only support the scammers. Having XP Security 2012 licensed
version is
useless because it will lead you into finding your computer dramatically slow. To sum up, it
must
be clear that XP Security 2012 must be removed as soon as possible, so please, don't
waste any minute and delete
this scam.
9:59 pm edt
Anti-Malware LabWednesday, July 06, 2011 7:34 PM - Anti-Malware Lab is a typical fake anti-spyware program it
imitates a system scan and claims that your computer is infected with malicious
software. The
bogus program creates harmless files on your computer and then detect those files as viruses.
Finally,
it asks to pay for a full version of the program to remove the infections and to make your
computer more secure. Moreover,
Anti-Malware Lab displays fake security warnings and and
pop-ups claiming that your sensitive information can be stolen
or that your PC is under attack
from a remote computer. It goes without saying that you should remove Anti-Malware Lab
from
your computer as soon as possible. Some of the fake security alerts read: Anti-Malware Lab is
promoted
mostly through the use of Trojans, fake online scanners and other misleading
websites. While running, it will block legit
antivirus and anti-spyware programs, disable task
manager, registry editor and other useful system tools to protect itself
from being removed. It
will hijack Internet Explorer and block security related websites or redirect to various misleading
websites that promote rogue security software. As you can see, Anti-Malware Lab is nothing
more but a scam. If you
find that your computer is infected with this bogus program please use
the removal instructions below to remove Anti-Malware
Lab from your computer either manually
or with an automatic removal tool. If you have already purchased this fake program,
then contact
your credit card company immediately and dispute the charges.
9:52 pm edt
7/10/2011
Trojan Droppers and Downloaders
The Problem
A netbook (using Windows 7) used primarily for study was accessed and used to
go to WITN news (a local news
channel) to access information about the Anthony
trial and began to act sluggish. She informed me she has Norton Security
Suite
(an outstanding product), she primarily uses Google Chrome for browsing and
that she had attempted to get
rid of the problem by running a system restore
(this had worked for her before). She also deleted chrome (because she
believed it had attached to that program) and reinstalled chrome (but have lost
all of her bookmarks). She waived a
backup because she had performed one
before the restore and she wanted her system back up as soon as possible.
Diagnoses
Upon initial
inspection, Norton had identified trojan dropper 'generic3.cike'...
I informed the user that her Norton license was expired,
her chrome settings are
basically gone and I let her know using System Restore is often ineffective for
removing
virus', no matter how far back you take it. I told her many virus'
actually embed themselves in an info system in a
way that they are 'restored'
along with the system settings. The only way you can correct the license problem
is
to renew your Norton license, buy a new license with another security suite
or try one of the many free suites available
for download (for home/personal
use). I also explained that current (news) events, porno, games, music, movies
etc.,
are prime targets for cyber gangs and their weapons packages.
trojan dropper generic3 .cike
Trojan
Horse Dropper Generic, sometimes called simply Trojan.Dropper, is a
trojan virus designed to open a security hole on
your computer. This security hole,
sometimes called a backdoor, is used by hackers to steal your personal
information
and download large amounts of adware onto your computer. Once
downloaded, the adware tracks your online behavior and
launches targeted pop-
up advertisements. In addition to being a nuisance, these pop-up advertisements
may slow
your computer and contain malicious links. Note that the removal steps
presented in this article apply to the and
Vista operating systems.
End
(killing) Processes
1 - Press "Ctrl" + "Shift" + "Escape" to open the Task Manager.
2 - Click on the "Processes"
tab of the Task Manager and then click on the
"Show Processes From All
Users" button at the bottom of the Task Manager.
3 - End the following processes. To end a process, right-click on the
process and select "End Process." Note that the processes are listed under
the "Image Name" heading.
search[2].exe
sysrtmvs.exe
senh.exe
wd7gi8nnew.exe
visfx500new.exe
OEM.exe
numbsoftnew.exe
Mendoza1.exe
Mendoza.exe
4 - Close the Task Manager.
Delete
Registry Entries
1 - Click on the "Start" menu icon and type "regedit" into the "Search
Programs and Files" box and press "Enter." The Registry Editor opens.
2 - Click on "Edit" and then "Find" and type
"Microsoft\Windows\CurrentVersion\Emitt" into the "Find Box" and click
"Find Next."
3 - Right-click on the highlighted registry entry and select "Delete."
4 - Close the Registry Editor.
Delete Files
1 - Click on the "Start" menu icon and then click on the "Search
Programs
and Files" box.
2 - Search for and delete each of the following files. To delete a file,
right-click on it and select "Delete."
"search[2].exe"
"sysrtmvs.exe"
"aouei"
"senh.exe"
"wd7gi8nnew.exe"
"visfx500new.exe"
"OEM.exe"
"numbsoftnew.exe"
"Mendoza1.exe"
"Mendoza.exe"
3 - Restart
your computer.
The Solution
I loaded and ran a scan with AVG Free and it promptly detected (in
Documents and Settings/name.name/Local
Settings/Temp/)
Oxaemnscwr.tmp Trojan.downloader
Censwwmoxra.tmp Trojan
Wsxoracnem.tmp
Trojan
Generic23.ABAY Trojan
Generic22.BXUD Trojan/backdoor
Mxeroacwsn.tmp Trojan.Fraudpack.Gen
***The dropper had helped these files in***
AVG allowed me to quarantine (and eliminate) these threats in good time.
I loaded and ran Superantispyware (it gets everything out) and the system
is clean. The Result is a 'healthy
system' and one 'satisfied user'.
 
|
|
Q. How do I avoid rogue antispyware and antivirus software? A. Make sure you 'Choose Industry Certified "Security Program"
Solutions'! If your PC is connected to
the internet, uses e-mail, has software of an unknown origin
installed and comes into contact with recordable media (jump drives, dvd's, cd's, etc) Antispyware and Antivirus protection is a requirement. They help prevent attacks through e-mail (and/or attachments sent with e-mail) and surfing the web.
They also help you eradicate infections which are the result
of security holes and bugs in software. (The e-mail, web surfing
and software holes and bugs result in the most serious internet
attacks). One
way to know you're purchasing a trustworthy application is to confirm that the program
you choose has earned certification from the leading labs.
Industry certification
from ICSA Labs, Virus Bulletin, West Coast Labs, the National Association
of Specialist Computer Retailers, and others all require antispyware/ antivirus programs to meet stringent requirements to receive certification.
Smartphone and Tablet Tips to create a safe passcode. Smartphones and tablets open the
door to your Work, friends, family, bank details, etc... No matter which device you use, follow these tips to keep your data secure.
1. Always use a passcode. If someone gets hold of your device, the person has immediate access to your apps and
data. 2. Make your passcode difficult to guess. Codes such as 1234 or 2580 can be cracked in seconds. Go for something that’s
unique but easy for you to remember. 3. Longer is stronger. The longer the passcode, the harder it is to crack. Make yours a minimum of six
digits. 4. Mix numbers and letters. If your device allows, use a passcode that combines numbers, letters and punctuation. Avoid dictionary words and
choose a memorable combination. 5. Make it unique. Don’t use the same passcode for anything else, including other devices,
bank cards or online accounts. That way, if one passcode gets hacked the rest stay secure.
6. Be discreet. Look around and make sure no one is watching you enter your passcode, just as
you would protect your PIN at the ATM machine.
Q. What steps need to be taken to secure
mobile devices (smartphones) for personal/work phones and
tablets.
A. Follow these steps to secure your mobile
devices. 1. Secure your device a.
Always lock it
b. Apply a complex passcode
c. Shield your passcode
d. Apply the latest patches
2.
Prevent Malware Infections a.
Don't click on unsolicited links
b. Think before downloading apps
c. Don't "jailbreak" or "root" your mobile
3.
Be data aware a.
Be careful what you share
b. Encrypt sensitive data
4. Stay compliant
a. Know and follow your organizations security
policies
Q. Do you have an example of an Organizational 'Mobile Device Security Policy'
A. Here is EZMobilePC's policy.
1.
Introduction Mobile devices, such as smartphones and tablet computers, are important tools for the organization and their use
is supported to achieve business goals. However, mobile devices
also represent a significant risk to information security and data security as, if the
appropriate security applications and procedures are not applied, they can be a conduit for
unauthorized access to the organization’s data and IT infrastructure.
This can subsequently lead to data leakage and system infection.
EZMoblePC has a requirement to protect its information assets in order to safeguard its customers, intellectual property and reputation. This document outlines a set of practices and requirements for the safe use of mobile devices. 2.
Scope
1. All mobile devices, whether owned by EZMoblePC or owned by employees, that have
access to corporate networks, data and systems, not including corporate IT-managed
laptops. This includes smartphones and
tablet computers. 2. Exemptions: Where there is a business need to be exempted from this
policy
(too costly, too complex, adversely impacting other business requirements) a risk assessment
must be conducted being authorized by security management.
3. Policy - Technical Requirements
1.
Devices must use the following Operating Systems: Android 2.2 or later,
iOS 4.x or later.
2. Devices must store all user-saved passwords in an encrypted password store.
3. Devices must be configured with a secure password that complies with EZMoblePC's
password policy. This password must not be the same as any other credentials used
within the organization.
4.
With the exception of those devices managed by IT, devices are not allowed to be
connected directly to the internal corporate network.
3.1 User Requirements 1.
Users must only load data essential to their role onto
their mobile device(s).
2.
Users must report all lost or stolen devices to EZMoblePC
IT immediately.
3.
If a user suspects that unauthorized access to company
data has taken place
via a mobile device, they must report the incident in alignment
with EZMoblePC’s
incident handling process.
4. Devices must not be “jailbroken”* or have any software/firmware installed
which
is designed to gain access to functionality not intended to be
exposed to the user.
5.
Users must not load pirated software or illegal content
onto their devices.
6.
Applications must only be installed from official platform-owner
approved sources.
Installation of code from un-trusted sources is forbidden.
If you are unsure if an
application is from an approved source contact EZMoblePC IT.
7. Devices must be kept up to date with manufacturer or network provided patches.
As a minimum patches should be checked for weekly
and applied at least once a month.
8.
Devices must not be connected to a PC which does not
have up to date and enabled
anti-malware protection and which does not comply with corporate
policy.
9.
Devices must be encrypted in line with EZMoblePC’s
compliance standards.
10.
Users may must be cautious about the merging of personal
and work email accounts on
their devices. They must take particular care
to ensure that company data is only sent
through the corporate email
system. If a user suspects that company data has been sent
from a personal email account, either in body text or as an attachment, they must notify
EZMoblePC IT immediately.
11.
(If applicable to your organization) Users must not
use corporate workstations to backup or synchronize device content such as media files, unless such content is required
for legitimate business purposes. *To jailbreak a mobile device is to remove the limitations imposed by the manufacturer. This gives access to the operating system, thereby unlocking all its features and enabling the installation of unauthorized software.
Q. What is the first thing I should
do when I turn on my computer.
A. Back up important files
If you follow these tips, you're more likely to be free of interference from
hackers,
viruses,
and spammers. But no system is completely secure. If you have important files stored on your computer, copy them onto a removable disc or
an external
hard
drive, and store it in a safe place.

Q. How do I protect my password? A. Protect your passwords
Keep your passwords in a secure place, and out of plain sight. Don't share them
on the Internet, over email, or on the phone. Your Internet Service Provider (ISP)
should never ask for your password. In addition, hackers
may try to figure out your passwords to gain access to your computer. To make it tougher for
them:
Use passwords that have at least eight characters and include numbers or symbols.
The longer the password,
the tougher it is to crack. A 12-character password is
stronger than one with eight characters.
Avoid common word: some hackers
use programs that can try every word in the dictionary.
Don't use your personal information, your login name, or adjacent keys on the
keyboard as passwords.
Change your passwords regularly (at a minimum, every 90 days).
Don't use the same password for each online account you access.
Q. What steps need to be taken when
setting up Wireless Home Network Security. 1) Change Default Administrator Passwords (and Usernames)
Changing the default password is important because everyone
that purchases the same Wireless access device, knows your password. 2) Turn on (Compatible) WPA / WEP Encryption
By default, your Wireless device comes
without the encryption enables. WPA / WEP are security programs that forced your computer to provide
an encrypted password before you are allowed access
to the wireless access point. 3) Change the Default SSID
SSID is the network name of your wireless network;
most people leave the default name, such as, Linksys or NetGear. By changing the name, intruders have a more difficult time identifying your system and use known vulnerabilities. (And
of course, use the unchanged default password.) One
mistake people make is naming their home network their family name and or address. When cruising a neighborhood of wireless devices, its always scary to see Bobsnet444.
4) Disable SSID Broadcast
In Wi-Fi networking, the access point or router typically broadcasts
the network name (SSID) over the air at
regular intervals. This feature was designed for businesses and mobile hotspots where Wi-Fi clients may come and go. In the home, this feature is
unnecessary, and
it increases the likelihood an unwelcome neighbor or hacker will try
to log in to your home network.
5) Assign Static IP Addresses to Devices
Most home networkers gravitate toward using dynamic IP addresses.
This means that the IP Address, (the IP
Address is needed to participate on a network.) is typically
assigned automatically. A dynamic IP address on an unsecure system can also supply a hacker with a IP Address. 6) Enable MAC Address Filtering Each piece of Wi-Fi gear possesses a unique identifier called the "physical address" or "MAC address." Access points and routers keep
track of the MAC addresses of all devices that connect to them. Many such products offer the owner an option to key in the
MAC addresses of
their home equipment that restricts the network to only allow connections from those devices. Do this, but also know that the feature is not so powerful as it may seem. Hacker software programs
can fake MAC addresses easily.
7) Turn Off the Network During Extended Periods of Non-Use
The ultimate in security measures for any wireless network
is to shut down, or turn office your wireless access point
when you are not using. You are the most vulnerable at work or asleep, and mischief minded people know it.
8) Position the Router or Access Point Safely
Wi-Fi signals normally reach to the exterior of a home. A small amount
of "leakage" outdoors is not a problem,
but the further this signal reaches, the easier it is for others to detect and exploit. Wi-Fi signals often reach across streets and through neighboring homes. When installing a wireless home network, the position
of the access point or router determines it's reach. Try to position these devices near the center of the home rather than near windows to minimize
this leakage.
Q: What are the first security steps I should take before I connect my computer to the internet?
A: Practices Before You Connect a New Computer to the Internet
We advise home users to download and install software patches as soon as possible after connecting a
new computer to the Internet. However, since the background intruder scanning activity is constant, it may not be possible for the user to complete the download and installation of software
patches before the vulner- abilities they are trying to fix are exploited. We recommend the following actions 'before' connecting computers to the Internet
so
that
users can complete the patching process without incident.
Q. Are there any references you can recommend? A. References: A. Computer Emergency Response Team (CERT) B. Microsoft Windows
C. Apple Macintosh
OSX D. Linux
Q. How do I keep my system up to date once I go online. A. Keep your operating system
and Web browser Up-to-Date, and learn about their security features.
Hackers also take advantage of Web browsers (like Firefox or Internet Explorer) and operating system software
(like Windows or Mac's OS) that don't have the latest security updates. Operating system companies issue security
patches for flaws that they find in their systems, so it's important to set
your operating system and Web browser software to download and install security patches
automatically. In addition,
you can increase your online security by changing the built-in security and privacy settings in your operating system or browser. Check
the "Tools" or "Options" menus to learn how to upgrade from the default
settings. Use your "Help" function for more information about your choices. If you're not using your computer for an extended period, disconnect
it from the Internet. When it's disconnected, the computer doesn't send or
receive information
from the Internet and isn't vulnerable to
hackers.

Q. How do I keep my security software up to date. A. Use security
software that updates automatically Keep
your security software active and current: at a minimum, your computer should have anti-virus and anti-spyware software, and a firewall.
You can buy stand-alone programs for each element or a security suite that includes these programs from a variety
of sources, including commercial vendors or from your Internet Service Provider. Security software that comes pre-installed
on a computer generally works for a short time unless you pay a subscription fee to keep it in effect. In any
case, security software protects against the newest threats only if it is up-to-date. That's why it is critical to set your
security software to update automatically.Some scam artists distribute
malware disguised as anti-spyware software. Resist buying software in response to unexpected pop-up
messages or emails, especially ads that claim to have scanned your computer and detected malware. That's a tactic
scammers have used to spread malware. OnGuardOnline.gov can connect you to a list of security tools from legitimate security
vendors selected by GetNetWise, a project of the Internet Education Foundation.Once you confirm that your security software is up-to-date, run it to scan your computer
for viruses and spyware. If the program identifies a file as a problem, delete it. Anti-Virus Software Anti-virus software protects your computer from viruses that can destroy your data, slow your computer's performance, cause
a crash, or even allow spammers to send email through your account. It works by scanning your computer and your incoming
email for viruses, and then deleting them.
Anti-Spyware
Software Installed on your computer without
your consent, spyware software monitors or controls your computer use. It may be used to send you pop-up ads, redirect your computer
to websites, monitor your Internet surfing, or record your keystrokes, which, in turn, could lead to the theft of your personal
information. A computer may be infected with spyware if
it: Slows down, malfunctions, or displays repeated error messages
Won't shut down or restart
Serves up a lot of pop-up ads, or displays them when you're not surfing the web Displays web pages or programs you didn't intend to use,
or sends emails you didn't write. Firewalls
A firewall helps keep hackers from using your computer
to send out your personal information without your permission. While anti-virus software scans incoming email and files,
a firewall is like a guard, watching for outside attempts to access your system and blocking communications to and from sources
you don't permit. Don't Let Your Computer Become Part of a "BotNet"
Some spammers search the Internet for unprotected computers they can control and
use anony- mously to send spam, turning them into a robot network, known as a "botnet." Also known as a "zombie
army," a botnet is made up of many thousands of home computers sending emails by the millions. Most spam is sent remotely
this way; millions of home computers are part of botnets.Spammers
scan the Internet to find computers that aren't protected by security software, and then install bad software – known as "malware"
– through those "open doors." That's one reason why up-to-date security software is critical.Malware may be hidden in free software applications. It can be appealing to download free software like games, file-sharing
programs, customized toolbars, and the like. But sometimes just visiting a website or down- loading files may cause
a "drive-by download," which could turn your computer into a "bot." Another way spammers take over your computer
is by sending you an email with
attachments,
links or images which, if you click on or open them, install hidden software. Be cautious about opening any attachments or downloading files from emails you receive. Don't open an email attachment —
even if it looks like it's from
a
friend or coworker — unless you are expecting it or know what it contains. If you send an email with an attached file, include a text message explaining what
it is.
Q. What do I do in an emergency?
A. Here is what to do in an e-mergency
If you suspect malware is lurking on your computer, stop shopping, banking, and
other online activities that involve user names, passwords, or other sensitive information. Malware
could be sending your personal information
to identity thieves.
- Confirm that your security software is up-to-date, then use it to
scan your computer.
- Delete everything the program identifies as a problem.
- You may have to restart your computer for the changes to take effect.
- If the problem persists after you exhaust your ability to diagnose and treat it, you
might want to call for professional help.
- If your computer is covered by a warranty that offers free tech support, contact
the manufacturer.
- Before you call, write down the model and serial number of your computer, the
name of any software you've installed, and a short description of the problem.
- Your notes will help you give an accurate description to the technician.
- If you need professional help, if your machine isn't covered by a warranty, or if
your security software isn't doing the job properly, you may need to pay for
technical support.
- Many companies — including some affiliated with retail stores — offer tech
support via the phone, online, at their store, or in your home.
- Telephone or online help generally are the least expensive ways to access
support services — especially if there's a toll-free helpline — but you may
have to do some of the work yourself. -
Taking your computer to a store usually is less expensive than hiring a technician or
repair person to come into your home.
- Once your computer is back up and running, think about how
malware could have been downloaded
to your machine, and what
you could do to avoid it in the future.
- Also, talk about safe computing with anyone else who uses the computer.
Q. Where do I report
Hacking or Malware activity?
A. Here is where to report:
Hacking or a Computer Virus
Alert the appropriate authorities by contacting: Your ISP and the hacker's ISP (if you can tell what it is). You can usually find an ISP's email
address on its website. Include information on the incident from your firewall's log file. By alerting the ISP to the
problem on its system, you can help it prevent similar problems in the future. The FBI at www.ic3.gov. To fight computer criminals, they need to hear from you.
Internet
Fraud If a scammer takes advantage of you through an
Internet auction, when you're shopping
online, or in any other way, report it to the Federal Trade Commission, at ftc.gov. The FTC enters Internet, identity theft, and other fraud-related complaints into Consumer Sentinel, a secure, online database available to hundreds of civil and criminal law enforcement agencies in the U.S. and abroad.
Deceptive
Spam If you get deceptive spam, including email phishing
for your information, forward it
to spam@uce.gov. Be sure to include the full header of the email, including all routing information. You also may report phishing email to of ISPs, security vendors, financial institutions and law enforcement agencies, uses these reports to fight phishing.
Divulged
Personal Information If you believe you have mistakenly
given your personal information to
a fraudster, file a complaint at ftc.gov, and then visit the Federal Trade
Commission's Identity Theft website at ftc.gov/idtheft to learn how to minimize your risk
of damage from a potential theft of your identity.
Parents Parents sometimes can feel outpaced by their technologically savvy kids. Technology aside, there are lessons that parents can teach to help kids stay safer as they socialize online. Most ISPs provide parental
controls, or you can buy separate
software. But no software can substitute for parental supervision. Talk to your kids about safe computing practices, as well as the things they're seeing and doing online.
Social Networking
Sites Many adults, teens, and tweens use social networking sites to exchange information about themselves, share pictures and
videos, and use blogs and private
messaging to communicate with friends, others who share interests, and sometimes even the world-at-large. Here are some tips for parents who want their kids to use these sites safely:
Use privacy settings to restrict who can access and post on your child's website. Some social networking sites have strong privacy
settings. Show your child how to
use these settings to limit who can view their online profile, and explain to them why this is important. Encourage your child to think about the language used in a blog, and to think before posting pictures and videos. Employers, college
admissions officers, team coaches,
and teachers may view your child's postings. Even a kid's screen name could make a difference. Encourage teens to think about the impression that screen names could make. Remind your kids that once they post information online, they can't take it back. Even if they delete the information from a site, older
versions may exist on other people's
computers and be circulated online.
Talk to your kids about bullying. Online bullying can take many forms, from spreading rumors online and posting or forwarding private messages
without the sender's OK, to sending
threatening messages. Tell your kids that the words they type and the images they post can have real-world consequences. They can make the target of the bullying feel bad, make the sender look bad
— and, some- times, can bring
on punishment from the authorities. Encourage your kids to talk to you if they feel targeted by a bully. Talk to your kids about avoiding sex talk online. Recent research shows that teens who don't talk about sex with strangers online
are less likely to come in contact
with a predator.
Tell your kids to trust their instincts if they have suspicions. If they feel threatened by someone or uncomfortable because of something online, encourage
them to tell you. You can then help
them report concerns to the police and to the social networking site. Most sites have links where users can immediately report abusive, suspicious, or inappropriate activity.

Q. What is the best way to keep malware
out.
A.
Try to minimize the threat.
Minimizing
the Effects of Malware on Your Computer
Malware is short for “malicious software;” it includes viruses —
programs that copy themselves without your permission — and spyware, programs installed without your consent to monitor or control your
computer activity. Criminals are hard at work thinking up creative ways to get malware on your computer. They create appealing web sites, desirable downloads, and compelling
stories to lure you to links that will download malware, especially on computers that don’t use adequate security software. Then, they use the malware to
steal personal information, send spam, and commit fraud.It doesn’t have to be that way.
So says a website with tips from the federal government and the technology industry that is helping consumers be on guard against Internet fraud, secure their
computers, and protect their personal malware can wreak, and reclaim their computers and their electronic information. Computers may be infected with malware if they:
-
slow down, malfunction, or display repeated error messages;
- wont shut down or restart; -
serve up a lot of pop-up ads, or display them when youre not surfing
the web;
or
-
display web pages or programs you didnt intend to use, or send emails
you
didnt write.
If you suspect malware
is on your computer
If you suspect malware is lurking on your computer, stop shopping, banking, and other online activities that involve user names, passwords, or other
sensitive inform- ation.
Malware on your computer could be sending your personal information to identity thieves.
Then, confirm that your security software is active and current:
at a minimum, your
computer
should have anti-virus and anti-spyware software, and a firewall. You can buy stand-alone programs for each element or a security suite that
includes these programs
from a variety of sources, including commercial vendors or from your Internet Service Provider. Security software that comes pre-installed on a computer
generally works
for a short time unless you pay a subscription fee to keep it in effect. In any case, security software protects against the newest threats
only if it is up-to- date.
Thats why it is critical to set your security software and operating system (like Windows or Apples OS) to update automatically.
Some scam artists distribute malware disguised as anti-spyware software. Resist buying software in response to unexpected pop-up messages or emails,
especially ads
that claim to have scanned your computer and detected malware. Thats a tactic scammers have used to spread malware, and that has attracted the attention
of the Federal
Trade Commission, the nations consumer protection agency, as well as a security tools from legitimate security vendors selected by GetNetWise, a project
of the Internet
Education Foundation.
Once you confirm that
your security software is up-to-date, run it to scan your compu- ter for viruses and spyware. Delete everything the program identifies as a problem.
You
may have to restart your computer for the changes to take effect.If you suspect that your computer still is infected, you may want to run a second anti-spyware
or anti-virus
program. Some computer security experts recommend installing one program for real-time protection, and another for periodic scans of your machine
as a
way to stop malware that might have slipped past the first program.
Finally, if the problem persists after you exhaust your own ability to diagnose and treat it, you might want to call for professional
help. If your computer is covered by a warranty that offers free tech support, contact the manufacturer. Before you call, write down the model and serial number of
your computer, the name of any software you’ve installed, and a short description of the problem. Your notes will help you give an accurate description to the technician.If you need professional help, if your machine isn’t covered by a warranty, or if your security software isn’t
doing the job properly, you may need to pay for technical support. Many companies — including some affiliated with retail stores —
offer tech support via the phone, online, at their store, or in your home. Telephone or online help generally are the least expensive
ways
to access support services — especially if there’s a toll-free helpline — but you may have to do some of the work yourself.
Taking your computer to a store usually is less expensive than hiring a technician or repair person to come into your home.
Once your computer is back
up and running, think about how malware could have been downloaded to your machine, and what you could do to avoid it in the future. If your security software or operating system was
out-of-date, download the newest version and set it to update automatically. Use the opportunity to back up important files by copying them onto a removable disc. Other
ways to minimize the chances of a malware download in the future:
-
Don’t click on a link in an email or open an attachment unless you
know who sent it and what it is. Links in email can send you to sites
that automatically download malware to your machine. Opening
attachments — even those that appear to come from a friend or
co-worker — also can install malware on your computer.
-
Download and install software only from websites you know and trust.
Downloading free games, file-sharing programs, and customized
toolbars may sound appealing, but free software can come with
malware.
-
Talk about safe computing. Tell your kids that some online activity
can
put a computer at risk: clicking on pop-ups, downloading free games or
programs, or posting personal information.
Finally, monitor your computer
for unusual behavior. If you suspect your machine has been exposed to malware, take action immediately. Report problems with malware to your ISP so it can try to prevent similar problems and
alert other

Q. What Should Parents know about Social
Networking Sites?
A. Social Networking
Sites
"It's 10 p.m. Do you know where your
children are? "Remember that phrase from your own childhood? It's still a valid question, but now, it comes with a twist: "Do you know where your kids are — and who they're chatting with online? "Social networking sites have morphed into
a mainstream medium for teens and adults. These sites encourage and enable people to exchange information
about themselves, share pictures and videos, and
use blogs and private messaging to communicate with friends,
others who share interests, and sometimes
even the world-at-large. And that's why it's important
to be aware of the possible pitfalls that come
with networking online. Some social networking
sites attract pre-teens – even kids as young as 5 or 6. These younger-focused sites don't allow the same kinds of communication
that teens and adults have, but there are still things that parents can do to help young kids socialize
safely online. In fact, when it comes to young kids, the law provides some protections – and gives parents some control over the type of information that children can disclose online. For sites directed to children under age 13, and for general audience sites that know
they're dealing with kids younger than 13, there's the Children's Online Privacy Protection Act (COPPA). It requires
these sites to get parental consent before they collect, maintain, or use kids' Information. COPPA also allows parents to review their child's online profiles and blog pages. Parents sometimes can feel outpaced by their technologically savvy kids.
Technology aside, there are lessons that parents
can teach to help kids stay safer as they socialize online.
Help Kids Socialize Safely OnlineOnGuard Online shares these tips for safe social networking:
Help
your kids understand what information should be private. Tell them why it's important to
keep some things – about themselves, family members and friends
– to themselves.
Information like their full name, Social Security number, street address, phone number,
and
family financial information — like bank or credit card Account numbers
— is private and
should stay that way. Tell them not to choose a screen name that gives away too
much
personal information.
Use privacy settings to restrict who can access and post on your child's website. Some
social networking sites have strong privacy settings.
Show your child how to use these settings to limit who can view their online profile,
and
explain to them why this is important.
Explain that kids should post only information that you — and they — are comfortable
with others seeing. Even If privacy settings are turned on, some — or even all
— of your
child's profile may be seen by a broader audience Than you're comfortable with.
Encourage your child to think about the language used in a blog, and to think before
Posting pictures and videos. Employers, college admissions officers, team coaches,
and teachers may view your child's postings.
Even a kid's screen name could make a difference. Encourage teens to think about the
impression that screen names could make.
Remind your kids that once they post information online, they can't take it back.
Even if they delete the Information from a site, older versions may exist on other
people's computers and be circulated online.
Know how your kids are getting online. More and more, kids are accessing the Internet
through their cell phones.
Find out about what limits you can place on your child's cell phone. Some cellular
companies have plans that limit downloads, Internet access, and texting; other plans
allow kids to use those features only at certain times of day.
Talk to your kids about bullying. Online bullying can take many forms, from spreading
rumors online and posting or forwarding private messages without the sender's
OK, to
sending threatening messages. Tell your kids that the words they type and the
images
they post can have real-world consequences. They can make the target of the
bullying feel bad, make the sender look bad – and, sometimes, can bring on
punishment from the authorities.
Encourage your kids to talk to you if they feel targeted by a bully.
Talk to your kids about avoiding sex talk online. Recent research shows that teens who
don't talk about sex with strangers online are less likely to come in contact with
a
predator.If you're concerned that your child is engaging in risky online behavior,
you can
search the blog sites they visit to see whatinformation they're posting. Try searching
by their name, nickname, school, hobbies, grade, or area where you live.
Tell your kids to trust their gut if they have suspicions. If they feel threatened by someone
or uncomfortable because of something online, encourage them to tell you. You
can then
help them report concerns to the police and to the social networking site. Most
sites have
links where users can immediately report abusive, suspicious, or inappropriate
online
behavior.
Read sites'
privacy policies. Spend some time with a site's privacy policy, FAQs, and
parent sections to Understand its features and privacy controls. The site should
spell out
your rights as a parent to review and delete your child's profile if your child
is younger
than 13.
A Few More Tips to Protect Pre-TeensMany of the tips above apply for pre-teens, but
parents of younger children also can: Take
extra steps to protect younger kids. Keep the computer in an open area like the
kitchen or family room, so you can keep an eye on what your kids are doing online.
Use the Internet with them to help develop safe surfing habits.
Consider taking advantage of parental control features on some operating systems
that let you manage your kids' computer use, including what sites they can visit,
whether they can download items, or what time of day they can be online.
Go where your kids go online. Sign up for – and use – the social networking spaces
that your kids visit. Let them know that you're there, and help teach them how to act
as they socialize online.
Review your child's friends list. You may want to limit your child's online “friends” to
people your child actually knows and is friendly with in real life.
Understand sites' privacy policies. Sites should spell out your rights as a parent to
review and delete your child's profile if your child is younger than 13. For More InformationTo learn more about staying safe online, visit the websites of the following organizations:
Federal Trade Commission — www.OnGuardOnline.gov The FTC works for the consumer to prevent fraudulent, deceptive, and unfair business
practices in the marketplace and toprovide information to help consumers spot, stop, and avoid them.
To file a complaint or to get free information onconsumer issues, visit ftc.gov or call toll-free, 1-877-FTC-HELP
(1-877-382-4357); TTY: 1-866-653-4261.The FTC manages OnGuardOnline.gov, which provides practical tips
from the federal government and the technologyindustry to help you be on guard against Internet fraud,
secure your computer, and protect your personal information. ConnectSafely — www.connectsafely.org ConnectSafely is a forum for parents, teens, educators, and advocates designed
to give teens and parents a voice in thepublic discussion about youth online safety, and has tips, as
well as other resources, for safe blogging and socialnetworking. Along with NetFamilyNews.org, it is
a project of the non- profit Tech Parenting Group. Cyberbully411 — www.cyberbully411.org Cyberbully411 provides resources and opportunities for discussion and sharing
for youth - and their parents - who havequestions about or may have been targeted by online harassment.
The website was created by the non-profit Internet Solutions for Kids, Inc., with funding from the Community
Technology Foundation of California. GetNetWise — www.getnetwise.org GetNetWise is a public service sponsored by Internet industry corporations and
public interest organizations to helpensure that Internet users have safe, constructive, and educational
or entertaining online experiences. The GetNetWise coalition works to provide Internet users with the
resources they need to make informed decisions about their and theirfamily's use of the Internet. iKeepSafe.org is a coalition of 49 governors/first spouses, law enforcement,
the American Medical Association, the American Academy of Pediatrics, and other associations dedicated
to helping parents, educators, and caregivers byproviding tools and guidelines to promote safe Internet
and technology use among children. NCMEC is a private, non-profit organization that helps prevent child abduction
and sexual exploitation; helps find missingchildren; and assists victims of child abduction and sexual
exploitation, their families, and the professionals who serve them. staysafe —
www.staysafe.org staysafe.org is an educational site intended to help
consumers understand both the positive aspects of the Internet aswell as how to manage a variety of
safety and security issues that exist online. WiredSafety.org is an Internet safety and help group. WiredSafety.org provides
education, assistance, and awareness on cybercrime and abuse, privacy, security, and responsible technology
use. It is also the parent group of Teenangels.org, FBI-trained teens and preteens who promote Internet
safety. See also: Social Networking Sites: Safety Tips for Tweens and Teens What to Do if There's a ProblemTrust your gut if you have
suspicions. If you feel threatened by someone or uncomfortable because of something online,Tell an adult
you trust, and report it to the police and the social networking site.The Children's Online Privacy
Protection Act (COPPA) requires websites to obtain parental consent before collecting, using,or disclosing
personal information from children under age 13.
Q. What are
Nigerian con-men or internet scams?
A.
Phony Lotteries, Nigerian 419s, Advanced Fee Fraud, and Scams
While you're online:
Know who you're
dealing with. In any electronic transaction, independently confirm the other party's name, street
address, and telephone number. Resist the urge to enter foreign lotteries. These solicitations are phony
and illegal. Delete requests that claim to be from foreign nationals
asking you to help transfer their money through your bank account. They're fraudulent. Ignore unsolicited
emails that request your money, credit card or account numbers, or other personal information.
If you are selling something over the Internet, don't accept a potential buyer's offer to send you a check
for more than the purchase price, no matter how tempting the plea or convincing the story. End the transaction immediately
if someone insists that you wire back funds.The Internet gives buyers access to a world of goods and services, and gives sellers access to a world of customers.
Unfortunately, the Internet also gives con artists the very same access. But being on guard online can help you maximize the
global benefits of electronic commerce and minimize your chance of being defrauded. OnGuard Online wants you to know how to
spot some cross-border scams — including foreign lotteries, money offers, and check overpayment schemes — and
report them to the appropriate authorities. Foreign Lotteries For years, scam operators have used the telephone and direct mail to entice U.S. consumers into buying chances in supposedly
high-stakes foreign lotteries. Now they're using email, too — either to sell tickets or suggest that a large cash prize
has your name on it. No matter what country's name is used to promote a lottery, the pitch follows a pattern: you should send
money to pay for taxes, insurance, or processing or customs fees. The amount may seem small at first, but as long as you keep
paying, the requests for funds will keep coming — for higher and higher amounts. Some victims have lost thousands of
dollars.Most scam operators never buy the lottery tickets on your behalf. Others buy some tickets, but keep the "winnings"
for themselves. In any case, lottery hustlers generally try to get you to share your bank account or credit card numbers,
so they can make unauthorized withdrawals.If you're thinking about responding to a foreign lottery, OnGuard Online wants you to remember: Playing
a foreign lottery is against the law.
There are no secret systems for winning foreign lotteries. Your chances of getting any money back are
slim to none. If you buy even one foreign lottery ticket, you can expect many more bogus offers
for lottery or investment "opportunities." Your name will be placed on "sucker lists" that fraudsters
buy and sell. Keep your
credit card and bank account numbers to yourself. Scam artists often ask for them during an unsolicited sales pitch. Once
they get your account numbers, they may use them to commit identity theft.Resist solicitations for foreign lottery promotions. Report them to the appropriate government officials, then hit delete.View a sample fraudulent foreign lottery solicitation.
"Nigerian" Foreign Money Offers
The "Nigerian" scam got its name from emails that supposedly came
from Nigerian "officials" who needed your help getting at their money — which was tied up due to strife in
their country. Today, people claiming to be officials, businesspeople, or the surviving relatives of former government honchos
in countries around the world send countless offers via email to transfer thousands of dollars into your bank account if you
will just pay a fee or "taxes" to help them access their money. If you respond to the initial offer, you may receive
documents that look "official." But then, you will get more email asking you to send more money to cover transaction
and transfer costs, attorney's fees, blank letterhead, and your bank account numbers, among other information. Subsequent
emails will encourage you to travel to another country to complete the transaction. Some fraudsters have even produced trunks
of dyed or stamped money to verify their claims.The emails are from crooks trying to steal your money or commit identity
theft. Victims of this scam report that emergencies arise that require more money and delay the "transfer" of funds;
in the end, you lose your money, and the scam artist vanishes. According to the U.S. State Department, people who have responded
to these solicitations have been beaten, subjected to threats and extortion, and in some cases, murdered.If you receive an
email from someone claiming to need your help getting money out of another country, don't respond. After all, why would a stranger from another country pick you out at random to share thousands of
dollars? Report the solicitation to the appropriate government officials, and then hit delete.View a sample fraudulent foreign money offer.
Check Overpayment Schemes
Say
no to a check for more than your selling price, no matter how tempting the plea or convincing the story. Check overpayment
schemes generally target people who have posted an item for sale online. The con artist, posing as a potential buyer from
a foreign country (or a distant part of the U.S.), emails the seller and offers to buy the item with a cashier's check, money
order, personal check, or corporate check. Or the scammer may pretend to be a business owner from a foreign country, needing
"financial agents" to process payments for their U.S. orders; in exchange, they promise a commission.Regardless of the cover, here's what happens:
The scammer sends you a check that looks authentic — complete with watermarks — made payable for more money than
you expected. They ask you to deposit it in your bank account, and then wire-transfer some portion of the funds to a foreign
account. They provide convincing reasons why the check is for more than the necessary amount, and why the funds must be transferred
quickly. Sometimes, the counterfeit checks fool a bank teller, but be aware that the check still can bounce. The scammer vanishes
with the money you wired from your own account and you are on the hook for the entire amount of the worthless check. In addition,
a scammer who has your bank account number is likely to use it to withdraw more money from your account.
Reporting a Cross-Border Scam If you think you may have responded to a cross-border scam, file a complaint at www.econsumer.gov, a project of 20 countries of the International Consumer Protection and Enforcement
Network. Then visit the FTC's identity theft website at www.ftc.gov/idtheft. While you can't completely control whether you will become a victim
of identity theft, you can take some steps to minimize your risk.If you've responded to a "Nigerian" scheme, contact your
local Secret Service field office using contact information from the Blue Pages of your telephone directory, or from www.secretservice.gov/field_offices.shtml.In addition, report telemarketing fraud and check overpayment scams to your state
Attorney General, using contact information at www.naag.org.Report unsolicited email offers to spam@uce.gov — including offers inviting you to participate in a foreign
lottery, looking for help getting money out of a foreign country, or asking you to wire back extra funds from a check you
received.If you receive what looks like lottery material from a foreign country through the postal mail, give it to your local
postmaster.
For More InformationForeign Lottery Scams
U.S. Federal Trade Commission — The FTC works for the consumer to prevent fraudulent, deceptive,
and unfair business practices in the marketplace and to provide information to help consumers spot, stop, and avoid them.
To file a complaint or to get free information on consumer issues, visit www.ftc.gov or call toll-free, 1-877-FTC-HELP (1-877-382-4357); TTY: 1-866-653-4261.
The FTC enters Internet, telemarketing, identity theft, and other fraud-related complaints into Consumer Sentinel, a secure,
online database available to hundreds of civil and criminal law enforcement agencies in the U.S. and abroad.Competition Bureau in Canada — The Competition Bureau is an independent law enforcement agency
in Canada that investigates anti-competitive practices and promotes compliance with the
laws under its jurisdiction. To file a complaint or to get free information, visit www.competitionbureau.gc.ca or call toll-free, 1-800-348-5358. The Bureau has the ability to refer criminal matters to the Attorney General of Canada,
who then decides whether to prosecute before the courts.United Kingdom's Office of Fair Trading — The United Kingdom's
Office of Fair Trading is responsible for making markets work well for consumers. They protect and promote consumer interests
throughout the United Kingdom, while ensuring that businesses are fair and competitive. To file a complaint or to get free information,
visit www.oft.gov.uk or send an email to enquiries@oft.gsi.gov.uk.Australian Competition and Consumer Commission — The Australian Competition and Consumer Commission encourages vigorous
competition in the marketplace and enforces consumer protection and fair trading laws. To file a complaint or to get more
information, visit www.accc.gov.au. The ACCC advocates consultation and negotiation as the first and
best option to settle disputes, but once the ACCC pursues legal action any sort of mediation becomes less likely. "Nigerian" Advance-Fee Scams U.S. Secret Service — The Secret Service investigates violations of laws relating to financial
crimes, including access device fraud, financial institution fraud, identity theft, and computer fraud. To file a complaint
or to get free information, visit www.secretservice.gov or call 202-406-5708.U.S. Department of State — The Department of State's mission is to create a more secure, democratic,
and prosperous world for the benefit of the American people and the international community. As part of that mission, the
Department of State seeks to minimize the impact of international crime, including cross-border internet scams, on the United States and its citizens. To get free information, visit www.state.gov.
Q. What should I do prior to disposing of an old computer?
A. Computer Disposal Once you have a “clean” computer,
consider recycling, donating, or reselling it – and keep the environment in mind when disposing of your computer.If you want to get rid of your old computer, options include recycling,
reselling, and donating. But before
you log off for thelast time, there are important
things to do to prepare it for disposal. Computers
often hold personal and financial
information, including passwords, account numbers, license keys or registration numbers for software programs, addresses and phone numbers, medical and prescription information, tax returns, and other personal documents. Before getting rid of your old computer, it’s a good idea to use software to “wipe”the hard drive clean. If you don’t, consider your old hard drive a 21st century treasure chest for identity thieves
and information pirates. The Federal Trade Commission
(FTC), the nation’s consumer
protection agency, says you can deter identity theft and information piracy by taking a few preventive steps.
Understanding Hard Drives A computer’s hard
drive stores data, and maintains an index of files. When you save a file, especially a large one, it is scattered around the hard drive in bits and
pieces. Files also are automatically created by browsers
and operating systems. When you open a file, the hard drive checks the index, then gathers
the bits and pieces and reconstructs them. When you
delete a file, the links between the index and the file disappear, signaling to your system that the file isn’t needed any longer and that hard drive space
can be overwritten. But the bits and pieces of the deleted file stay on your computer until they’re overwritten, and they can be retrieved with a data recovery program.
To remove data from your hard drive permanently,
it needs to be wiped clean.
Cleaning Hard Dives Before you clean your hard
drive, save the files that are important to you on an external storage device – for example, a USB drive, a CDRom, or an external
hard drive – or transfer them to a new computer. Check your owner’s manual, the manufacturer’s website, or its customer support line for information on how to
save data and transfer it to a new computer. Utility programs to wipe your hard drive are available both online and in stores where computers are
sold. They’re generally inexpensive; some are available on the Internet for free. Wipe utility
programs vary in their capabilities: some
erase the entire disk, while others allow you
to select files or folders to erase. They also vary in their effectiveness: programs that overwrite
or wipe the hard drive many times are very effective; those that overwrite or wipe the drive only once may not prevent information being wiped from being recovered later.
If your old computer contains sensitive information that would be valuable to an identity
thief, consider using a program that overwrites or wipes the hard drive many times. Or, remove the hard
drive, and physically destroy it. One more thing to keep in mind: If you use your home or personal
computer for business purposes, check with your employer about how to manage information on your computer that’s business-related. The law requires businesses to follow
data security and disposal requirements for certain information that’s related to customers. Disposal
Options
Once you have a “clean”
computer, here’s how to dispose of it:
Recycle it. Many computer manufacturers have programs to recycle computers
and components. Check their
websites or call their toll-free numbers
for more information. The Environmental Protection Agency (EPA) has information on electronic product recycling
programs at
program. Check with your county or local government,
including the local landfill office for regulations.
Donate it. Many organizations collect old computers and donate them to charities.
Resell it. Some people and organizations buy old computers.
Check online. Keep
the environment in mind when disposing of your computer. Most computer equipment contains hazardous materialsthat don’t belong in a landfill. For example, many computers have heavy metals that can contaminate the earth. The EPA recommends that you check with your local health and sanitation agencies for ways to dispose of electronics safely.
www.hypersmash.com
hostgator promo
|
|