|
|
3/31/2012
Choosing A Backup Drive For Your Notebook
03/31/12 - You should know that it’s easier
to select a backup drive for your laptop than for your
desktop because the choices are much simpler.
Assuming you
want a portable external drive you can carry with you in your notebook bag,
your options are virtually all USB models
with 2.5 inch or smaller hard drives inside a plastic
or metal enclosure. Interface USB 3.0 portable drives are just starting to appear on the market. Among other benefits (see
the “Bus Power” sidebar in this article), the new USB version lets a drive read and write data
as fast
as it likes, as long as your notebook has a USB 3.0 port or adapter card. In
contrast, USB 2.0 caps data transfer to about 32MBps, which makes backups take much
longer than necessary. USB 3.0 is
backward compatible with USB 2.0 and 1.1 devices also.
Storage Technology For notebook backup purposes, it’s hard to argue with the cost per GB (gigabyte) and
overall capacity
advantage of a portable hard drive over an SSD (solid state drive). Even
though the latter will take a bit more abuse,
you shouldn’t notice much of a speed difference
between the two. External
SSDs do exist, and they are certainly rugged enough for travel. On the other hand,
capacities large enough for backup
purposes are pretty costly. A mere 64GB in USB 2.0
trim will cost around $145 or more online; Plan on $220 or more for
a USB 3.0 model that
will not drastically limit its own speed.
Capacity You can get a 1TB (terabyte) portable hard drive for as little as $130 online. Compare this
with an external
SSD, which will max out at about 256GB for approximately $780 on the
Web, and it’s obvious that magnetic disk media
is still the way to go for this application. Bundled Software Look into the software that comes with a portable drive, expecially the backup app. If it’s
described
as a drive imaging or disaster recovery tool, it backs up your operating system and
programs in addition to your personal
files. Some backup drives might even boot your laptop
in an emergency, depending on your notebook.
2:21 pm edt
3/29/2012
Windows Defending Center
03/29/12 - Windows Defending Center is a dangerous program that
belongs to the category of
rogue anti-spywares. Just like its predecessors, this sneaky program gets inside the system
with a help of trojans that use security vulnerabilities to get inside. In addition, Windows
Defending Center will
do its best to scam you out of your money. It will aggressively report about
numerous viruses detected on your PC and
then will offer to purchase its licensed version. Of
course, you should have been warned that such tactic is normal for
rogue anti-spywares and you
should never fall for this rogue. If you find this virus on your machine, you must uninstall
Windows Defending Center from your PC. Note that you won’t find it on your programs list, so
use reputable anti-spyware,
like Spyhunter or 2012 version of spyware doctor for that.
Trying to rip its victims off, this malware starts its activity
with numerous alerts and scanners
reporting invented viruses. You should never remove those files reported as malicious
because
they may also be legitimate your system files, foolishly said to be infected. Windows Defending
Center begins
its activity without any delay – it starts its campaign as soon as user reboots his
computer. In addition, next
to its alerts you will also receive its scanners also giving faked
information. As you can see, Windows Defending Center
has nothing to do with legitimate
activity. After a closer look, it has been reported to have no virus database needed
to find and
remove malware.
In order to trick you, Windows Defending Center reports: Warning
Firewall has blocked a program from accessing the Internet.
Windows Media Player Resources
C:\Windows\system32\dllcache\wmploc.dll
C:\Windows\system32\dllcache\wmploc.dll is suspected to have infected your PC.
This type of virus intercepts
entered data and transmits them to a remote server.
Error
Keylogger activity detected. System information security is at risk.
It is recommended to activate
protection and run a full system scan.
Error
Software without a digital signature detected.
Your system files are at risk. We strongly advise you to activate your
protection.
Torrent Alert
Recomended: Please use secure encrypted protocol for torrent links.
Torrent link detected!
Receiving
this notification means that you have violated the copyright laws. Using
Torrent for downloading movies and licensed
software shall be prosecuted and you
may be sued for cybercrime and breach of law under the SOPA legislation.
Please
register your copy of the AV to activate anonymous data transfer protocol
through the torrent link.
All you have to do is to do your best and stay away from this malware. In addition,
remove
Windows Defending Center without any delay because it won’t stop interrupting into your
browsing. This
scareware usually lets more malware inside the system without asking any
permission of a user, so prevent this by running
a full system scan with Spyhunter or 2012
version of spyware doctor.
     
6:33 pm edt
3/28/2012
Google Antivirus
03/28/12 - Google Antivirus is a rogue program created to trick users into helping cyber criminals
into infecting
their systems. Google, Bing and other popular URLs may be hacked by cyber
criminals. If you find yourself redirected
to the page that claims that Google systems have
detected unusual traffic from your computer and that you should purchase
Google Antivirus,
leave this page immediately! There is no such application as Google AV, so there is no point
of
downloading and installing this program on your machine. That’s just another trick used by
crackers to
steal your money.
According to GFI researchers, cyber criminals have altered
some popular search pages to
redirect their visitors to malicious page that seems to be powered by Google. Just like
any other
malicious page, this one starts typically by reporting numerous viruses detected on the system.
The
user is advised that if they do not download the program, the system will block the access
to Google services: “Google systems have detected unusual traffic from your computer. Please
check
you PC on viruses. To continue, please download and install our antivirus software.
[DOWNLOAD
button] or our system will block your access to Google services”.
Security experts recommend ignoring
this alert and never downloading Google Antivirus which in
reality is malicious Trojan.Win32.Fakeav.tri. Because it is
new virus, your anti-malware program
may fail to detect the exe file as a malicious one, so ignore any suspicious antivirus
software you
are offered online. Please use one of the automatic removal tools listed below to eradicate this
malware from your system.
     
3/27/2012
Overcoming (Backup) Restoration Issues
03/27/2012 - You have made a full system backup of your hard
drive . After a few years of heavy
use your PC’s hard drive eventually crashes, and now you need to restore your
Backed up data
to a replacement drive. Unfortunately, your data
transfer to the replacement drive is not going as
planned.

Hard Drive Detection Trouble Most backup and restoration programs require
that the target hard drive (the drive to which you
plan to restore the data) have a MBR (master boot record) or GPT (GUID
or global unique
identifier partition table). These are types of markers that show the PC what portions of the hard
drive the system should read when the PC boots up. (They also show where the OS (operating
system) is stored). Typically,
new drives aren’t initialized with either an MBR or a GPT, and
you’ll need to run a bootup application to
set up the drive. If you use Windows’ built-in system backup tools,
you’ll need to insert your backup media and
press F8 to load the System Recovery interface. At the ‘Advanced
Boot Options’ screen, use
your arrow keys to highlight ‘Repair Your Computer’ and press ‘Enter’.
Click ‘Next’ enter your
user name and password, and click ‘OK’. Select ‘System Image Recovery’
and follow the on
screen instructions to restore your copy of Windows. With
most third-party restoration applications, you can insert the rescue media and it will start
the pre-boot application.
For example, with ABSplus Rescue from CMS (www.cms.com), you’ll
need to insert the ABSplus Rescue CD into your
disc drive and press the key that starts the
BIOS (Basic Input Output System). Typically, that key is the DELETE or F2
key. If those keys
don’t do the trick, watch the screen during startup for instructions (or consult your computer’s
manual). When the BIOS opens, change the boot order
so that the PC boots from the CD/DVD drive and
select Save and Exit. When restarted, CMS loads its installation application,
during which you
can select the hard drive and backup copy you want to install. Once done, CMS ABSplus
Rescue installs
the partition records and begins transferring your backup to the new hard drive. Recover Specific Files The
full system backup didn’t transfer all the files you wanted. Most system backup applications
provide a way to recover
specific files or folders from a complete backup, allowing you to still
recover key documents, photos or other data.
The file level restore also comes in handy if you’ve
installed new applications and created new files since your
last backup and only want to rescue
a few files that were accidentally deleted. Many third party restoration tools allow
you to mount
an image of your backup files, where you can search through the folders using Windows
Explorer to recover
the files you need. To rescue specific files from Windows Backup in Windows
7, click the ‘Start’ button, select
‘Control Panel’, choose ‘System And Security’.
And click ‘Backup And Restore’. Under the
Restore section, click the ‘Restore My Files’ button
and select ‘Browse For Files’ or ‘Browse For
Folders’, depending on which options is more suitable
for your restoration. Then you can double
click the disc drive (or another drive, if you have another target in mind
for external storage) and
drill down to find the files or folders you want to restore. Select the files and folders,
then right
click the ones you want and click copy. Next, open a folder on your new hard drive, right click
anywhere
in the folder, and click ‘Paste’. Your files will now copy to the new drive.
5:11 pm edt
3/17/2012
Troubleshoot Ram Problems
03/17/12 - System memory, or RAM, is just as important
as the CPU or motherboard to a PC’s
operation. Because
of their simplicity, RAM modules are very dependable , but problems do
occur. Here Are a few ways to target potential memory issues.

You Can’t Handle The Power The DRAM (dynamic RAM) chips
on memory modules are very sensitive to electrostatic
Discharge.
A static shock so slight you can’t feel it can act like an explosion within the
memory’s Microscopic cells. I always paying a few bucks for an antistatic wrist or shoe strap
and properly Grounding yourself before touching PC components. Note that power surges from
the wall can Have the same effect, which is why it’s important
to use a high quality surge
protector, preferably One with automatic
voltage regulation.
The POST System
Sometimes
you get lucky and the motherboard will tell you your memory is bad. This often
Happens early in the bootup process while the system
is running its POST (power on self test).
If the POST detects a bad memory module, the motherboard may emit a single, continuous
(and highly annoying)
beep. Modern BIOSes (Basic Input/Output Systems) made by AMI
(www.ami.com) will issue one or three short beeps., depending on what memory functions
is
faulty.
AMI’s advice in this cae is to “reseat the memory, or replace with known good modules.”
Be particularly
on the lookout for unseated memory if you’ve just finished an upgrade or
Otherwise moved the system around. You can tell that
memory is unseated because the row of
Gold leads along the bottom edge will be partially visible, and it’s likely that one of the two locks
At each end of the memory slot
won’t be fully gripping the RAM module. Just to be safe, you
Can remove the modules and blow out their slots with compressed air to remove any
stray dust
Or
dirt that might be blocking contact points. Another way that some motherboards let you
know about bad memory is with an LED (Light
Emitting Diode) readout. This feature is sometimes found on higher end motherboards. If
There’s a memory problem, the LED will
display a code ( explained in the manual) pointing
To the memory as a source.
Blue Screen Of Death
Your next
most likely set of clues may come from Windows. A common symptom is getting the
Blue Screen of Death either during Windows installation
or while running Windows. Also crashes
During memory intensive operations, such as 3D gaming or media editing, can signal bad
Memory (or other problems, especially overheating).
Obviously, if you get an error message
In Windows citing a memory problem at a certain address, that’s a big clue.
Assuming
you consulted the manual and have your modules in the correct slots given your
Configuration, reseating the memory and/or swapping it
out for known good modules is about
Always the key to fixing hardware based memory issues. Still, if you need more confirmation
That memory is your culprit, start with Windows
Memory Diagnostic (tinyurl.com/qoy4;
Windows Vista/7? Users can find it by searching for ‘memory’ in the Start Search field) or
Memtest86 (www.memtest.org).
12:23 pm edt
3/12/2012
AntiSpyCheck
03/12/12 - AntiSpyCheck is rogue security application and although it claims to be a spyware
scanner, spam filter
and popup blocker, it's just another fake tool trying to get users money.
Once it infiltrates your system, AntiSpyCheck
will flood you with fake notifications and popups
about fictitious threats in your system. It will offer to remove infections
if you buy a full version
of the program. Do not fall victim to this rogue... use one of the automatic removal tools to
get
rid of this rogue immediately.
You should also add antispycheck.com (just another knockoff of AdProtect.com)
website to your
blacklist (your HOSTS file, for example).
AntiSpyCheck properties:
•
Shows commercial adverts
• Connects itself to the internet
• Stays resident in background
     
10:24 am edt
3/11/2012
Win32.Vitro
03/10/12 - Win32.Vitro is a very dangerous trojan virus. Just like trojan Vundo and Zlob, Win32.Vitro can be obtained by visiting various noxious
websites. Mainly, Win32.Vitro is promoted on websites that offer
free online movies. In order to watch those movies a visitor has to
download certain video codec. However, it's not a real video codec, but trojan Win32.Vitro. Once active, Win32.Vitro performs illegal actions. It downloads and installs additional malware and spyware without user's permission. What is more, it advertises rogue anti-spyware applications such as Antivirus 360 and System Protector. Win32.Vitro must be removed at earliest stage. Please
use one of the automatice removal tools listed below.
Win32.Vitro properties:
• Changes
browser settings
• Shows commercial adverts
• Hides from the user
• Stays resident in background
     
3/8/2012
BIOS Drive Recognition
03/08/12 - When you can’t get to the OS level, there
are other checks that can help determine
If the hard drive is the problem. First, see whether your BIOS (Basic Input/Output System, the
program which manages low-level PC operations such as the boot Process) can see the drive.
When you boot your PC, you should see a message To press a key ( possibly ESC, F1, F2, or
Delete) to enter Setup.
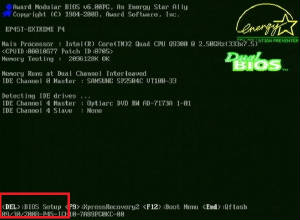
Press this key quickly at
startup and your BIOS utility will open. You may see a Listing that
includes detected drives, or you may have to switch to a different Display.
(If needed , note the
BIOS version and manufacturer and check the Internet
for assistance.) If your BIOS recognizes
the drive, it’s a positive – Although not foolproof – sign of life. Antivirus Rescue Disk
If you have a bootable rescue
disc ( www.avg.com/us-en/avg-rescue-cd-download ) from your
‘Antivirus’ program, reboot and run A
scan on the drive. It will scan the drive, including the boot
partition, for ‘Viruses’. If it finds anything, follow any instructions you are given. If the ‘Virus
Checker’ can Scan the drive or your BIOS will not start, it is probably safest to see a
Professional. Check The Cables If the BIOS doesn’t recognize your drive, the internal cables may have come
loose.If you recently
moved or jostled your PC or if you were
inside the case doing Upgrades or cleaning, you (or a
PC Technician)
should check the drive cables for A tight connection (and potentially
check the
hard drive, as well). For instructions About opening
your case to check the drive and replacing
the drive, check the Manufacturers
website.
Manufacturers
If you
do not see a BIOS message prior to OS start, consult the user manual or The
manufacturers site. The manufacturer may have overridden this feature. If Nothing happens
when you boot the PC, something else (motherboard, power Supply, etc) is the problem.
6:41 pm est
3/7/2012
Troubleshoot Legacy Hard Drive Problems
03/07/12 - Whether you hear strange noises from your computer
of your computer is crashing
intermittently, You may suspect
you have a damaged hard drive. ‘Average’ hard drive life cycles
are generally Estimated at three to five years., and some drives last 10 years or more. Those
figures are not Very comforting if your drive fails after six months and you do not have a data
backup. Why
do hard drives fail (more often that they should)? How can you tell when a hard
drive is in Trouble? The answers are pretty straightforward and knowing them can save you
hours of System misery.

Confirm The Most Likely Cause
Despite talk about data
loss due to viruses and software glitches, hardware failure remains the
Most likely cause of data failure. As a System Administrator with Storage Area
Network
Experience,
I can tell you that hardware and system failure causes 56% of data loss (making
It the most common problem). Human error comes in
second at 26%, and software (program)
Corruption around 9%. That is a one in four chance the file you cannot find is gone because
You copied (or saved) Over it, deleted it,
or damaged it. If your hard drive is actually failing,
You may have seen warning signs, and if not, there are ways to check the drive
for problems.
Traditional HDDs (Hard Disk Drives) are mechanical
devices composed of stacked platters
That spin very quickly (7200rpm is common). Read & Write heads, connected to a moving
Arm, hover above the platters separated by
a cushion of air. These heads move like
Lightening across the surface, retrieving or storing bits of data (millions of tiny magnetized
Or demagnetized areas).
Hard drives can simply wear out… the
motor that spins the platters can fail or behave
Erratically. Hard drives in PCs that are dropped or roughed up, (especially while a read
Write operation is executing) may be damaged
if the heads make contact with the surface
Of the platters. Hard drives also have filtered air intakes, which can become damaged
(clogged) or allow particles into the drive
mechanism. This can incapacitate the drive.
Drive
Failure Warning Signs
Warning signs are common with hard drives. One obvious sign of drive failure is noise. You
May hear a repetitive noise… best described
as a metallic crunching or thumping sound…
As the arm thrashes around, trying to access data. Some (but not all) HDDs make an
Audible whirring noise (the sound of the spinning
platters) when they are operating normally.
If you can hear your drive and the pitch (whirring) rises and falls repeatedly, it means the
Drive is spinning up and down. This could
indicate a problem with the drive’s power
Supply (but it definitely means trouble is at hand).
If you are hearing any noises that sound drive-related,
your best shot at saving the drive is
To cease operation immediately. If you absolutely need some critical files from the drive,
Get them off immediately and then get the
drive to a repair shop. The longer you operate
With unexpected noises, the greater the chances of total drive failure.
There are other, early hard drive trouble signs. You may notice files are missing, damaged,
Or take a long time to open. Your computer
may freeze frequently as the drive struggles
To access data. Alternately, your PC may freeze during bootup, or you may see the
Classic ‘Blue Screen of Death’.
All of
these issues can also occur with other problems, such as OS (operating system) or
Software corruption. A corrupted MBR (master boot
record)… a tiny file on your hard
Drive that indexes the data… can cause some of these problems. The MBR can be
Damaged by a bad sector (space) on your hard
drive, but a virus (or other malware)
Can also be at fault. Fortunately, there are ways to test for and eliminate drive failure.
If your
system will not boot at all, or if you start the PC and see a pre-Windows-boot
Error message that reads ‘Operating System Not Found’,
‘Missing Operating System’,
‘Setup Did Not Find Any Hard Disk Drives Installed On Your Computer’, your HDD
may have failed completely.
Drive
Checking
If you can boot into Windows and your hard drive isn’t crying for help (literally),
a
Drive-checking
utility can assist. Windows comes with a built-in disk utility
(Check Disk). It’s good for doing initial (free) scans on your drive. To
use Check
Disk,
select ‘Computer’ or ‘My Computer’ from the ‘Start’ menu. Right click your
Drive and select ‘Properties’.
Click the ‘Tools’ tab and select ‘Check Now’. You
Can opt to analyze only or to fix errors and recover bad sectors. If the hard drive
Is busy, Windows
may prompt you to schedule the task for later.
Advanced, third-party drive utilities can monitor your drive closely and are often
More thorough
in handling repairs than Check Disk. Three such tools are PC Tools
Performance-toolkit ($39.95), iolo’s System Mechanic ($29.95), and
SpotMau Power Suite 2012. Your HDD manufacturer
may provide a free tool.
Preventive
Maintainence
As with
so may PC components, taking care of your hard drive… defragmenting
It regularly and running drive utilities and not allowing
it to become jostled, too
Hot or cold, or otherwise abused… will help squeeze the most life from your
Hard drive. Defragmentation is especially
useful in terms of mechanical wear and
Tear, as an arm that has to move excessively to locate millions of disparate
Fragments will likely wear out sooner.
A heavily
used drive will also expire faster than one that is rarely accessed. If you
Purchase a new drive, it is worth spending more for a heavy-duty
drive if you
Perform
an excessive number of reads and writes.
3:53 pm est
3/6/2012
Smart Fortress 2012
03/06/12 - Smart Fortress 2012 is a Rogue Anti-Spyware scam hailing from
the dangerous
Rogue.SecurityTool family of malwares that is famous for 'Security Tool' and 'Smart
Protection 2012'. After infecting a user’s system, it proceeds to scare its victim into buying
the
“product” by displaying fake security messages, stating that your computer is infected with
spyware and only
Smart Fortress 2012 can help you to remove it after you download the trial
version. As soon as the victim downloads Smart
Fortress 2012 trial version, it pretends to scan
your computer and shows a grossly exaggerated amount of non-existent
errors. Then, Smart
Fortress 2012 offers to allows users to buy the full version to fix these false errors. If the user
agrees, Smart Fortress 2012 does not only fix the errors, but it also takes the user’s money
and may even install
additional spyware into the victim’s computer. Please, ignore all Smart
Fortress 2012 alerts, which will display
alerts saying something like this:
Warning: Your computer is infected
Detected spyware infection!
Click this message to install the last update of security software…
Smart Fortress 2012 Warning
Intercepting programs that may compromise
your privacy and harm your system have
been detected on your PC.
Click here to remove them immediately with Smart
Fortress 2012
Warning!
Application cannot be executed. The file notepad.exe
is infected.
Please activate your antivirus software.
Security
Monitor: WARNING!
Attention! System detected a potential hazard (TrojanSPM/LX) on your computer
that may infect
executable files. Your private information and PC safety is at risk.
To get rid of unwanted spyware and keep your computer
safe you need to update
your current security software.
Click Yes to download official intrusion detection system
(IDS software).
Some Rogue Anti-Spyware, such as Smart Fortress 2012, may
offer users the opportunity
to buy it after the victim clicks on a banner or a pop-up while surfing the internet. Usually,
a
Trojan is installed to a victim’s computer after clicking on the advertisement. It then proceeds
to download
or even install Smart Fortress 2012, which is another way for Rogue Anti-Spyware
to spread itself. Smart Fortress 2012,
is nearly impossible to remove manually. The registration
code ( AA39754E-715219CE ) worked with earlier threats
from this family to make the virus
think that you have purchased it (you can then run a scan). Please use
one of the automatic
removal tools listed below to eradicate this parasite.
-
Anti-Spyware program
- May spread via Trojans
- Displays fake security messages
- Installs additional spyware
to your computer
- Repairs its files, spreads and updates by itself
- Violates your privacy and compromises your
security
     
5:15 pm est
8 Ways to Unleash the Gaming Rig Inside Your PC
03/06/12
 Your home computer may be used
for many things, but nothing reveals its performance
Your home computer may be used
for many things, but nothing reveals its performance
deficiencies like modern 3D games. These graphics-intensive programs
tax modern CPUs,
memory, and video resources much more than typical home or home-office applications would.
In an underperforming system, the realism and smoothness of gameplay suffers. Enthusiasts use
terms such as ?FPS?
(frames per second) and ?lag? to describe these symptoms. The higher
FPS your PC can achieve and the lower the lag, the
more enjoyable gaming is.
And although the symptoms of an unoptimized PC are more noticeable while gaming, you
can
also notice them slowing down your computer during daily use. Optimize your system for
gaming, and everything
else you do on it will fly.
With this in mind, here are eight easy-to-use tools within System Mechanic
that will bring out
the beast in your PC:
1. EnergyBooster™: When FPS
rates decline and video becomes choppy, many gamers focus
on upgrading their video cards. Most don't realize the same
symptoms can be caused by a
Central Processing Unit (CPU) that's been "bottlenecked" by too many demanding
processes
running at the same time. EnergyBooster shuts down unneeded background processes and
channels maximum
power to the game or application you are running, resulting in ideal speed
and responsiveness. Learn more about EnergyBooster.
2. Program Accelerator™: Why wait between levels for your game or program to load
massive files when you could be in the action
faster? Program Accelerator uses patent-pending
technology to consolidate program files on the hard drive and reduce
disk lag. Much more
sophisticated than disk defragmenting, it resolves all the file entropy (dispersal) caused by
patches and updates that other techniques can't address.
3. Memory Mechanic®: Long stretches of computer use can result in memory leaks that lead
to sluggish performance and normally requires
a full system reboot. But with one click, Memory
Mechanic swiftly releases trapped RAM and instantly refreshes performance without
the need to
close running applications. Learn more about Memory Mechanic.
4. NetBooster®: An unoptimized internet
connection is a source of game lag, especially in
multiplayer environments. You can even get kicked off a server for
?high pings? due to a poor
connection! NetBooster can increase internet speeds up to 300%, significantly improving your
connection and even speeding up those multi-gigabyte automatic updates and patches that can
take hours to download.
5. PC Cleanup™: Sweep out over 50 types of junk files including temp downloads from game
patches that can run into gigabytes of
wasted disk space. Learn more about PC Cleanup.
6. CRUDD Remover™: Duplicate, unnecessary programs act like dead weight on your PC's
available resources. Commonly Redundant or Unnecessary
Decelerators and Destabilizers
(CRUDD) Remover takes the guesswork out of finding and classifying them so you can choose
to
remove the ones that are bloating your system and quickly achieve a leaner, faster system.
7. Designated Drivers™: Having up-to-date drivers is critical to avoid freezes and crashes.
Designated Drivers ensures every
driver update posted in the Windows database is quickly and
safely downloaded to your system.
8. SSD
Accelerator™: With regular use, even state-of-the-art
solid state drives (SSDs)
experience incremental performance loss. Keep slowdown at bay with SSD accelerator, which
uses the latest
technology to ensure that your SSD stays optimized and prevents the drive from
degrading prematurely.
Bonus Tip: Enable System Mechanic's patented
ActiveCare®
technology to tune and maintain your computer automatically
when your PC is idle so it's instantly
ready foraction whenever
you are. |
With System Mechanic, you can spend less time worrying about your computer and
more time focusing on what you
enjoy.
5:31 am est
3/5/2012
Exploit Rogue Scanner
03/05/12
- Exploit Rogue Scanner has 18 known variants and is spreading.
This Web Threat is
currently ranked 2nd in the world for online threats (according to AVG). This infection has been
detected on victims machines in 203 countries during the month of February. There
are currently
1232 websites in 69 countries that host Rogue Scanner.
AVG blocks these scan types keeping
the malicious software off systems.
Here are the 18 variants:
The most popular variants of Rogue Scanner are Rogue Scanner (type 1927), Rogue Scanner
(type 831), Rogue Scanner (type 1929) Rogue Scanner (type 1929),
Rogue Scanner (type 1868),
Rogue Scanner (type 1885),
Rogue Scanner (type 1876), Rogue Scanner (type 1870),
Rogue
Scanner (type 1886), Rogue Scanner (type 965),
Rogue Scanner (type 1852), Rogue Scanner
(type 1878),
Rogue Scanner (type 932), Rogue Scanner (type 1917),
Rogue Scanner (type
1901), Rogue Scanner (type 1879),
Rogue Scanner (type 1877), Rogue Scanner (type 1866)
This program, a rogue (or fake)
application is itself the infection. It's designed to manipulate
and scare Windows XP / Vista / 7 users into going to whatever website it wants you to and give
up your personal
information by purchasing this program.
Most anti-virus (AV) programs don't catch this type of infection due to the fact that it's not the
only
infection on your system. There is usually another infection working
in the background
trying to keep that infection hiding. I found
7 Backdoor infections at work in a system with
malwarebytes.
Catch all of the infections that may be at work in your system with one of the automatic removal
tools below.
     
Malicious program has been detected
03/05/12 - When a user receives an onscreen message saying,
“Security Warning! Malicious
program has been detected. Click here to protect your computer.” You need to immediately
make sure your Security Software has an active license
and is up to date (Your Security
Software is only as strong as your latest
update). Please Scan your system immediately!
You may see additional
warnings such as:
“Security Protection has found 82 useless and Unwanted
files on your computer”,
informing you “79 infections Are critical privacy compromising content”.
“Activate Security Protection”.
You will be prompted to “Activate Security Protection
Now”. Don’t Do It!
The Bad Grammer and
Misspellings should be a dead give away (the language does not sound
real) that you are dealing with fake Anti-Virus.
In the optimal world, you boot the system into
Safe Mode and
run your scan. The criminals making malware are very clever (utilizing parasites
such as w32/blaster.worm) because they
typically will not allow users to update the signatures
in their
Security databases, download anti-malware tools, edit the registry or hosts file and in
some cases, utilize Task Manager (to kill processes), boot into Safe Mode or Connect to the
Internet
unless you ‘Purchase Their Product’. Don’t Do It!
Download one of the
automated removal suites below to remove the parasite or in case you have
a suite that is outdated, download the free
version of Malwarebytes to run a full scan and remove
all detected infections. Then
delete Quarantined files.
If this does not
work, you may have to create a new account with admin priviledges on your
system and then download the tools to clean the system.
     
11:00 am est
3/1/2012
Remotely Connect and Repair a PC/Laptop
03/01/12 - Windows XP introduced this remote program, and it has been improved with Windows
7. Remote Assistance
is a safe way to let someone remotely log into your computer because,
unlike a lot of remote control programs, it doesn't
open up a connection to the Internet so that
anyone can connect at will if they provide the correct credentials.
In Windows 7, choose Help and Support, More Support Options, and select Remote Assistance
at the bottom of the
window. Once you've fired up Remote Assistance, it's time to send the help
invitation. In Windows 7, the invitation can
be sent as an e-mail. The credentials that will actually
let a remote computer connect with yours will be attached to
the e-mail. For further security, the
user will also need to create a password that the remote user will need to enter
before they're
granted full access.
As long as Remote Assistance is connected on both sides, the local user will be able to watch
their desktop, seeing everything that's going on. It's a great way to teach someone how
to fix
their broken computer when you can't physically be there.
Remote Desktop Connection
If you need to connect remotely to a Windows machine on a regular basis, it's easier to use the
Remote Desktop
Connection program that comes stock with Windows. Remote Desktop
Connection is an invaluable tool for many tasks, especially
for systems administrators that need
to manage their servers when they're away.
Before connecting via Remote Desktop Connection, the target PC must be configured to allow
remote connections.
In Vista or Windows 7, go to the Control Panel, select System, then
choose Remote Settings. Inside Remote Settings, you'll
be able to add users, granting them
permission to connect. Members of the Administrators Group are automatically allowed
access,
so you don't have to manually add them.
When connecting remotely with Remote Desktop, you'll need to know the remote machine's IP
address and you'll need
to provide a valid user name and a password before you'll be allowed
inside. Remote Desktop is good if you're going to
be doing a lot of remote connections, but for a
one-time fix, Remote Assistance is a better option.
Problem Step Recorder
Included with Windows 7, Problem Steps Recorder allows users to document step-by-step
actions. This process becomes
useful for showing exactly what happens just before a problem
arises. An important step in fixing a
computer problem is the ability to recreate it. Problem Steps
Recorder works by compiling a series of screen shots
(inside a MHTML file), which can be sent
in an e-mail attachment for, say, a help desk technician
to analyze. The MHTML file can be
viewed in Internet Explorer.
Oddly, as useful as Problem Steps Recorder is, it's hidden (it can't be found in the Control
Panel). In Windows
7, hit the Windows key and type in psr.exe in the search box. Many users
not only use Problem Steps Recorder for fixing
PC issues but also for creating tutorials and
lessons for others to follow.
11:46 pm est
3/1/2012
Adware.Loadscc
03/01/12 - Adware.Loadscc is a dangerous adware application
that infiltrates your system via
trojans and other computer parasites. It generates money for its creators by contacting
the
service provider to confirm the success of other malware installation.
Unfortunately, no manual removal
instructions are currently available for Adware.Loadscc.
Please use one of the automatic security suites listed below
to remove this threat immediately.
Loadscc properties:
• Shows commercial adverts
• Connects itself to the internet
• Stays resident in background
     
4:57 pm est
Cable And DSL Modems
03/01/12 - Just like most routers include firewall capabilities,
some broadband modems also
Function as a router. Whether you opt to add a separate router to manage the traffic on your
Network depends on a few things. For one,
is your modem router wireless or wired?
Wireless Modem/Routers
The obvious
advantage of a wireless modem/router is that the computers in the network don’t
Need to be physically connected (to
the modem router) by Ethernet cable in order to communi-
Cate. The downside is that wireless connections tend not to offer as much speed
and security
As
wired connections. If your network requires a high level of security and speed, you likely
Will want to make sure you’re using
a wired connection to the router.
Technological Comfort
The other thing
to consider is your level of comfort with the technology and your willingness to
Set up an additional router and configure it properly.
Having one device to manage and monitor
Is likely going to be easier than configuring a system where the router your using is separate from
The built-in version in your
modem. This is a viable option, though , if your computing situation
Calls for it. Likely your best bet for help on adding a router in this situation
would be the router
Manufacturer’s Web site and/or technical documentation.
KISS (Keep It Simple Stupid)
That being
said, if your Internet provider has already given you the hardware you’ll need to get
Online and it also functions as a router,
it’s probably best to just stick with that hardware. The
Simple reason (KISS)? You run the risk of inviting problems with hardware and software
components when you introduce additional products into the mix.
1:03 pm est
Editing Your Registry
03/01/2012 - The Windows Registry is a central location for
maintaining operating system,
application, user, And hardware
information. If you make a change to the operating system, for
instance, that Change is reflected in the Registry. In theory, you could make the change to the
Registry Yourself and get the same result, but as you’ll see, the Registry is complex, and it’s
best to Only edit it manually when you have no other option.
Look in on your Registry
To view
the contents of your Windows Registry, you use a tool called ‘Registry Editor’. In
Windows XP, click ‘Run’ in the
‘Start’ menu, type ‘regedit’, and press ‘Enter’. In Windows
Vista/7, open the ‘Start’ menu,
type ‘regedit’ in the ‘Search’ field, and press ‘Enter’.
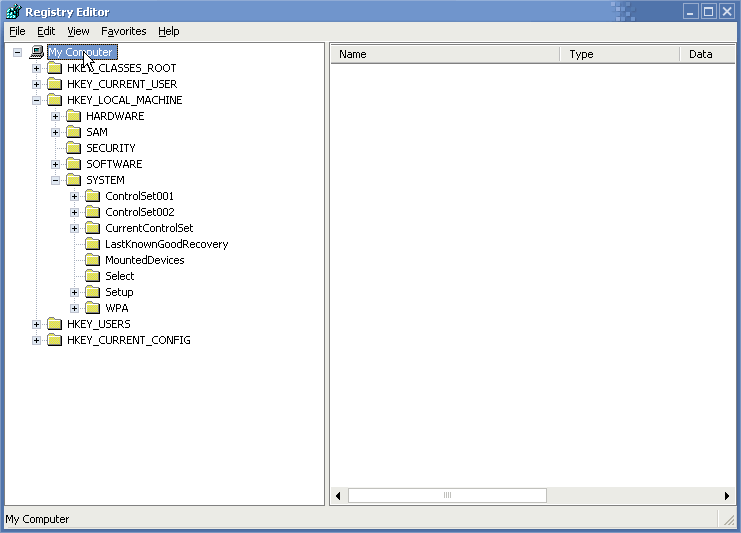
The Registry is divided
into keys, subkeys, and values. If it helps, you can think of the Registry’s
Structure as being similar to that of your folders
and files in ‘My Computer’. Keys and subkeys
Are arrange in a hierarchical order, while values reside within a specific key
like files within a
Folder. In the Registry Editor, you’ll see keys and subkeys listed on the left side of the window.
Double-click a key to view
subkeys. Click a key or subkey to see the values contained in it
Displayed on the right side of the Registry Editor.
Registry Organization
In WinXP, Vista, and Win7, you’ll notice five main keys. These keys are often abbreviated to
Save space. These keys, with
common abbreviations listed in parenthesis, are:
HKEY_CLASSES_ROOT
(HKCR)
HKEY_CURRENT_USER
(HKCU)
HKEY_LOCAL_MACHINE
(HKLM)
HKEY_USERS
(HKU)
HKEY_CURRENT_CONFIG
(HKCC).
Different types of
information are grouped into these five main keys. Aspects relating to the
Windows user interface are commonly found in HKCR. This includes file extension maps.
If you Double-click a DOC file in Windows
Explorer, Windows will consult HKCR to
Decide how to open the file (in this case, it will decide to open the file in Microsoft Word).
HKU, as the name
implies, contains data relating to each user account on the system.
HKCU is a subject of HKU that points specifically to the configuration settings
of the user
That
is currently logged into Windows.
HKLM contains information
about the hardware and software found on a particular
Computer. You can have different hardware profiles in Windows, so HKCC is a subset
Of
HKLM that relates specifically to the system’s current hardware configuration.
As you click through various keys, you’ll see values displayed on the right side of the
Registry Editor. Many keys
have more than one value, and each value contains a name,
Type, and data. Looking at values of each key, you’ll
notice five main types of values.
REG_BINARY is a raw binary value (often displayed in hexadecimal format) and is
Usually related to a hardware configuration.
REG_DWORD values are often associated
With device driver and system services and often use either 0 or 1 as the data (to
Indicate the hardware or service is disabled
or enabled, respectively). REG_SZ
Indicates a human-readable (as opposed to raw binary) string value (such as a word).
Other types of string values include REG_EXPAND_SZ,
which indicates a variable
String, and REG_MULTI_SZ, which contains a list of strings.
Back
Up Your Registry
Given that a mistake while manually editing
your Registry could result in serious
Consequences, you should always back up your Registry before working on it. There
Are two main methods you can use for backing
up and restoring your Windows
Registry.
System Restore
One
commonly recommended method for backing up your entire Registry is to create
A System Restore Point. One advantage of this method is
that you also protect other
Data essential for booting up Windows. To create a restore point in WinXP, click
the ‘Start’ menu, ‘All Programs’, ‘Accessories’,
‘System Tools’, and then ‘System
Restore’. In the ‘System Restore’ window, select
‘Create A Restore Point’ and click ‘Next’. Provide a descriptive
name for the restore
point and click ‘Create’. In Vista and Win7 , right click ‘Computer’ in the ‘Start’
menu
and
select ‘Properties’. Click ‘System Protection’ on the left side of the window. Click
the ‘Create’ button,
provide a name for the restore point, and click ‘Create’ again.
To restore from a previously created backup point, click the ‘Start’ menu, ‘All Programs’,
‘Accessories’,
‘System Tools’, and ‘System Restore’. In WinXP, make sure ‘Restore My
Computer To An Earlier Time’ is selected
and click ‘Next’. In WinXP, flip back through
The calendar and look for valid restore points in the past. In Vista and Win7,
you’ll see
A list of valid restore points after clicking ‘Next’. Select a restore point and follow any
Further instructions.
Export Your Registry
While restore points are helpful, they have limitations. Restore points can be
deleted without
Warning.
If your cleaning the Registry after removing malware you may not want to
Memorialize an infection in a restore point.
Instead, export part or all of your Windows
Registry.
To export your entire Registry, click ‘My Computer’ (or ‘Computer’) above the list of keys
In the Registry
and click ‘File’ and ‘Export’. Choose a place to save the file and provide a
Descriptive file name. If you’re only
working on part of the Registry, right click the key
You’re working on and select ‘Export’. To restore your Registry,
select ‘Import’ from the
‘Registry Editor File’ menu, select your backup file, and click ‘OK’.
EDIT THE REGISTRY
Making
changes to the Registry is an easy process, but knowing what changes to make is the
Difficult part. Only make changes to your Windows
Registry if you have instructions from a
Trusted source and you’re clear about what the instructions are directing you to do.
Keys and values can be deleted by right clicking the key or value and selecting
‘Delete’. To
Change the data stored in a value, right click the value name, select ‘Modify’, and make the
Changes. You can also add keys
and values. To add a key, right click the key under which
The new key should appear, select ‘New’, and click ‘Key’.
To add a value, right click the
key in which the value should appear, select ‘New’, click the proper type of value, and
provide the proper data.
While the Windows Registry can be intimidating, after working with this introduction, you will gain confidence now that you know your
way around.
12:16 pm est
|
|
Q. How do I avoid rogue antispyware and antivirus software?
A. Make sure you 'Choose Industry Certified "Security Program"
Solutions'!
If your PC is connected to
the internet, uses e-mail, has software of an unknown
origin
installed and comes into contact with recordable media (jump drives, dvd's,
cd's, etc) Antispyware and Antivirus protection is a requirement. They help prevent
attacks through e-mail (and/or attachments sent with e-mail) and surfing the web.
They also help you eradicate infections which are the result
of security holes and
bugs in software. (The e-mail, web surfing
and software holes and bugs result in
the most serious internet
attacks).
One
way to know you're purchasing a trustworthy application is to confirm that
the program
you choose has earned certification from the leading labs.
Industry certification
from ICSA Labs, Virus Bulletin, West Coast Labs, the National
Association
of Specialist Computer Retailers, and others all require antispyware/
antivirus programs to meet stringent requirements to receive certification.
Smartphone and Tablet Tips to create a safe passcode.
Smartphones and tablets open the
door to your Work, friends, family, bank details, etc... No matter which device you use, follow these tips to keep your data secure.
1. Always use a passcode. If someone gets hold of your device, the person has immediate access to your apps and
data.
2. Make your passcode difficult to guess. Codes such as 1234 or 2580 can be cracked in seconds. Go for something that’s
unique but easy for you to remember.
3. Longer is stronger. The longer the passcode, the harder it is to crack. Make yours a minimum of six
digits.
4. Mix numbers and letters. If your device allows, use a passcode that combines numbers, letters and punctuation. Avoid dictionary words and
choose a memorable combination.
5. Make it unique. Don’t use the same passcode for anything else, including other devices,
bank cards or online accounts. That way, if one passcode gets hacked the rest stay secure.
6. Be discreet. Look around and make sure no one is watching you enter your passcode, just as
you would protect your PIN at the ATM machine.
Q. What steps need to be taken to secure
mobile devices (smartphones) for
personal/work phones and
tablets.
A. Follow these steps to secure your mobile
devices.
1. Secure your device
a.
Always lock it
b. Apply a complex passcode
c. Shield your passcode
d. Apply the latest patches
2.
Prevent Malware Infections
a.
Don't click on unsolicited links
b. Think before downloading apps
c. Don't "jailbreak" or "root" your mobile
3.
Be data aware
a.
Be careful what you share
b. Encrypt sensitive data
4. Stay compliant
a. Know and follow your organizations
security
policies
Q. Do you have an example of an Organizational 'Mobile Device Security Policy'
A. Here is EZMobilePC's policy.
1.
Introduction
Mobile devices, such as smartphones and tablet computers, are important tools for the
organization and their use
is supported to achieve business goals.
However, mobile devices
also represent a significant risk to information security and
data security as, if the
appropriate security applications and procedures are not applied,
they can be a conduit for
unauthorized access to the organization’s data and IT
infrastructure.
This can subsequently lead to data leakage and system infection.
EZMoblePC has a requirement to protect its information assets in order to safeguard
its customers, intellectual property and reputation. This document outlines a set of
practices and requirements for the safe use of mobile devices.
2.
Scope
1. All mobile devices, whether owned by EZMoblePC or owned by employees, that have
access to corporate networks, data and systems, not including corporate IT-managed
laptops. This includes smartphones and
tablet computers.
2. Exemptions: Where there is a business need to be exempted from this
policy
(too costly, too complex, adversely impacting other business requirements) a risk
assessment
must be conducted being authorized by security management.
3. Policy - Technical Requirements
1.
Devices must use the following Operating Systems: Android 2.2 or later,
iOS 4.x or later.
2. Devices must store all user-saved passwords in an encrypted password store.
3. Devices must be configured with a secure password that complies with EZMoblePC's
password policy. This password must not be the same as any other credentials used
within the organization.
4.
With the exception of those devices managed by IT, devices are not allowed to be
connected directly to the internal corporate network.
3.1 User Requirements
1.
Users must only load data essential to their role onto
their mobile device(s).
2.
Users must report all lost or stolen devices to EZMoblePC
IT immediately.
3.
If a user suspects that unauthorized access to company
data has taken place
via a mobile device, they must report the incident in alignment
with EZMoblePC’s
incident handling process.
4. Devices must not be “jailbroken”* or have any software/firmware installed
which
is designed to gain access to functionality not intended to be
exposed to the user.
5.
Users must not load pirated software or illegal content
onto their devices.
6.
Applications must only be installed from official platform-owner
approved sources.
Installation of code from un-trusted sources is forbidden.
If you are unsure if an
application is from an approved source contact EZMoblePC IT.
7. Devices must be kept up to date with manufacturer or network provided patches.
As a minimum patches should be checked for weekly
and applied at least once a month.
8.
Devices must not be connected to a PC which does not
have up to date and enabled
anti-malware protection and which does not comply with corporate
policy.
9.
Devices must be encrypted in line with EZMoblePC’s
compliance standards.
10.
Users may must be cautious about the merging of personal
and work email accounts on
their devices. They must take particular care
to ensure that company data is only sent
through the corporate email
system. If a user suspects that company data has been sent
from a personal email account, either in body text or as an attachment, they must notify
EZMoblePC IT immediately.
11.
(If applicable to your organization) Users must not
use corporate workstations to backup
or synchronize device content such as media files, unless such content is required
for
legitimate business purposes.
*To jailbreak a mobile device is to remove the limitations imposed by the manufacturer.
This gives access to the operating system, thereby unlocking all its features and enabling
the installation of unauthorized software.
Q. What is the first thing I should
do when I turn on my computer.
A. Back up important files
If you follow these tips, you're more likely to be free of interference from
hackers,
viruses,
and spammers. But no system is completely secure. If you have important
files stored on your computer, copy them onto a removable disc or
an external
hard
drive, and store it in a safe place.

Q. How do I protect my password?
A. Protect your passwords
Keep your passwords in a secure place, and out of plain sight. Don't share them
on the Internet, over email, or on the phone. Your Internet Service Provider (ISP)
should never ask for your password. In addition, hackers
may try to figure out your
passwords to gain access to your computer. To make it tougher for
them:
Use passwords that have at least eight characters and include numbers or symbols.
The longer the password,
the tougher it is to crack. A 12-character password is
stronger than one with eight characters.
Avoid common word: some hackers
use programs that can try every word in the
dictionary.
Don't use your personal information, your login name, or adjacent keys on the
keyboard as passwords.
Change your passwords regularly (at a minimum, every 90 days).
Don't use the same password for each online account you access.
Q. What steps need to be taken when
setting up Wireless Home Network Security.
1) Change Default Administrator Passwords (and Usernames)
Changing the default password is important because everyone
that purchases the same
Wireless access device, knows your password.
2) Turn on (Compatible) WPA / WEP Encryption
By default, your Wireless device comes
without the encryption enables. WPA / WEP are
security programs that forced your computer to provide
an encrypted password before
you are allowed access
to the wireless access point.
3) Change the Default SSID
SSID is the network name of your wireless network;
most people leave the default name,
such as, Linksys or NetGear. By changing the name, intruders have a more difficult time
identifying your system and use known vulnerabilities. (And
of course, use the unchanged
default password.) One
mistake people make is naming their home network their family
name and or address. When cruising a neighborhood of wireless devices, its always
scary to see Bobsnet444.
4) Disable SSID Broadcast
In Wi-Fi networking, the access point or router typically broadcasts
the network name
(SSID) over the air at
regular intervals. This feature was designed for businesses and
mobile hotspots where Wi-Fi clients may come and go. In the home, this feature is
unnecessary, and
it increases the likelihood an unwelcome neighbor or hacker will try
to
log in to your home network.
5) Assign Static IP Addresses to Devices
Most home networkers gravitate toward using dynamic IP addresses.
This means that
the IP Address, (the IP
Address is needed to participate on a network.) is typically
assigned automatically. A dynamic IP address on an unsecure system can also supply
a hacker with a IP Address.
6) Enable MAC Address Filtering
Each piece of Wi-Fi gear possesses a unique identifier called the "physical address"
or "MAC address." Access points and routers keep
track of the MAC addresses of all
devices that connect to them. Many such products offer the owner an option to key in the
MAC addresses of
their home equipment that restricts the network to only allow
connections from those devices. Do this, but also know that the feature is not so powerful
as it may seem. Hacker software programs
can fake MAC addresses easily.
7) Turn Off the Network During Extended Periods of Non-Use
The ultimate in security measures for any wireless network
is to shut down, or turn office
your wireless access point
when you are not using. You are the most vulnerable at work
or asleep, and mischief minded people know it.
8) Position the Router or Access Point Safely
Wi-Fi signals normally reach to the exterior of a home. A small amount
of "leakage"
outdoors is not a problem,
but the further this signal reaches, the easier it is for others
to detect and exploit. Wi-Fi signals often reach across streets and through neighboring
homes. When installing a wireless home network, the position
of the access point or
router determines it's reach. Try to position these devices near the center of the home
rather than near windows to minimize
this leakage.
Q: What are the first security steps I should take before I connect my computer to the internet?
A: Practices Before You Connect a New Computer to the Internet
We advise home users to download and install software patches
as soon as possible after connecting a
new computer to the
Internet. However, since the background intruder scanning activity
is constant, it may not be possible for the user to complete the
download and installation of software
patches before the vulner-
abilities they are trying to fix are exploited. We recommend the
following actions 'before' connecting computers to the Internet
so
that
users can complete the patching process without incident.
Q. Where do I report
Hacking or Malware activity?
A. Here is where to report:
Hacking or a Computer Virus
Alert the appropriate authorities by contacting: Your ISP and the hacker's ISP (if you can tell what it is). You can
usually find an ISP's email
address on its website. Include information on the
incident from your firewall's log file. By alerting the ISP to the
problem on its system,
you can help it prevent similar problems in the future. The FBI at www.ic3.gov. To
fight computer criminals, they need to hear from you.
Internet
Fraud If a scammer takes advantage of you through an
Internet auction,
when you're shopping
online, or in any other way, report it to the Federal Trade
Commission, at ftc.gov. The FTC enters Internet, identity theft, and other fraud-related complaints into Consumer Sentinel, a secure, online database available to hundreds
of civil and criminal law enforcement agencies in the U.S. and abroad.
Deceptive
Spam If you get deceptive spam, including email phishing
for your
information, forward it
to spam@uce.gov. Be sure to include the full header of the email, including all routing information. You also may report phishing email to
of ISPs, security vendors, financial institutions and law enforcement agencies,
uses these reports to fight phishing.
Divulged
Personal Information If you believe you have mistakenly
given your
personal information to
a fraudster, file a complaint at ftc.gov, and then visit the Federal Trade
Commission's Identity Theft website at ftc.gov/idtheft to learn how to minimize your risk
of damage from a potential theft of your identity.
Parents Parents sometimes can feel outpaced by their technologically savvy
kids. Technology aside, there are lessons that parents can teach to help kids
stay safer as they socialize online. Most ISPs provide parental
controls, or you
can buy separate
software. But no software can substitute for parental supervision.
Talk to your kids about safe computing practices, as well as the things they're
seeing and doing online.
Social Networking
Sites Many adults, teens, and tweens use social networking
sites to exchange information about themselves, share pictures and
videos, and
use blogs and private
messaging to communicate with friends, others who share
interests, and sometimes even the world-at-large. Here are some tips for parents
who want their kids to use these sites safely:
Use privacy settings to restrict who can access and post on your
child's website. Some social networking sites have strong privacy
settings. Show
your child how to
use these settings to limit who can view their online profile, and
explain to them why this is important.
Encourage your child to think about the language used in a blog,
and to think before posting pictures and videos. Employers, college
admissions
officers, team coaches,
and teachers may view your child's postings. Even a kid's
screen name could make a difference. Encourage teens to think about the
impression that screen names could make.
Remind your kids that once they post information online, they can't
take it back. Even if they delete the information from a site, older
versions may
exist on other people's
computers and be circulated online.
Talk to your kids about bullying. Online bullying can take many forms,
from spreading rumors online and posting or forwarding private messages
without
the sender's OK, to sending
threatening messages. Tell your kids that the words
they type and the images they post can have real-world consequences. They can
make the target of the bullying feel bad, make the sender look bad
— and, some-
times, can bring
on punishment from the authorities. Encourage your kids to talk to
you if they feel targeted by a bully.
Talk to your kids about avoiding sex talk online. Recent research
shows that teens who don't talk about sex with strangers online
are less likely to
come in contact
with a predator.
Tell your kids to trust their instincts if they have suspicions. If they feel threatened by
someone or uncomfortable because of something online, encourage
them to tell you.
You can then help
them report concerns to the police and to the social networking
site. Most sites have links where users can immediately report abusive, suspicious,
or inappropriate activity.

Q. What is the best way to keep malware
out.
A.
Try to minimize the threat.
Minimizing
the Effects of Malware on Your Computer
Malware is short for “malicious software;” it includes viruses —
programs that copy
themselves without your permission — and spyware, programs installed without
your consent to monitor or control your
computer activity. Criminals are hard at work
thinking up creative ways to get malware on your computer. They create appealing
web sites, desirable downloads, and compelling
stories to lure you to links that will
download malware, especially on computers that don’t use adequate security
software. Then, they use the malware to
steal personal information, send spam,
and commit fraud.It doesn’t have to be that way.
So says a website with tips from
the federal government and the technology industry that is helping consumers be on
guard against Internet fraud, secure their
computers, and protect their personal
malware can wreak, and reclaim their computers and their electronic information.
Computers may be infected with malware if they:
-
slow down, malfunction, or display repeated error messages;
- wont shut down or restart;
-
serve up a lot of pop-up ads, or display them when youre not surfing
the web;
or
-
display web pages or programs you didnt intend to use, or send emails
you
didnt write.
If you suspect malware
is on your computer
If you suspect malware is lurking on your computer, stop shopping, banking, and
other online activities that involve user names, passwords, or other
sensitive inform-
ation.
Malware on your computer could be sending your personal information to
identity thieves.
Then, confirm that your security software is active and current:
at a minimum, your
computer
should have anti-virus and anti-spyware software, and a firewall. You can
buy stand-alone programs for each element or a security suite that
includes these
programs
from a variety of sources, including commercial vendors or from your
Internet Service Provider. Security software that comes pre-installed on a computer
generally works
for a short time unless you pay a subscription fee to keep it in effect.
In any case, security software protects against the newest threats
only if it is up-to-
date.
Thats why it is critical to set your security software and operating system (like
Windows or Apples OS) to update automatically.
Some scam artists distribute malware disguised as anti-spyware software. Resist
buying software in response to unexpected pop-up messages or emails,
especially
ads
that claim to have scanned your computer and detected malware. Thats a tactic
scammers have used to spread malware, and that has attracted the attention
of the
Federal
Trade Commission, the nations consumer protection agency, as well as a
security tools from legitimate security vendors selected by GetNetWise, a project
of
the Internet
Education Foundation.
Once you confirm that
your security software is up-to-date, run it to scan your compu-
ter for viruses and spyware. Delete everything the program identifies as a problem.
You
may have to restart your computer for the changes to take effect.If you suspect
that your computer still is infected, you may want to run a second anti-spyware
or
anti-virus
program. Some computer security experts recommend installing one
program for real-time protection, and another for periodic scans of your machine
as
a
way to stop malware that might have slipped past the first program.
Finally, if the problem persists after you exhaust your own ability to diagnose and
treat it, you might want to call for professional
help. If your computer is covered by a
warranty that offers free tech support, contact the manufacturer. Before you call,
write down the model and serial number of
your computer, the name of any software
you’ve installed, and a short description of the problem. Your notes will help you give
an accurate description to the technician.If you need professional help, if your
machine isn’t covered by a warranty, or if your security software isn’t
doing the job
properly, you may need to pay for technical support. Many companies — including
some affiliated with retail stores —
offer tech support via the phone, online, at their
store, or in your home. Telephone or online help generally are the least expensive
ways
to access support services — especially if there’s a toll-free helpline — but you
may have to do some of the work yourself.
Taking your computer to a store usually is
less expensive than hiring a technician or repair person to come into your home.
Once your computer is back
up and running, think about how malware could have
been downloaded to your machine, and what you could do to avoid it in the future. If
your security software or operating system was
out-of-date, download the newest
version and set it to update automatically. Use the opportunity to back up important
files by copying them onto a removable disc. Other
ways to minimize the chances
of a malware download in the future:
-
Don’t click on a link in an email or open an attachment unless you
know who sent it and what it is. Links in email can send you to sites
that automatically download malware to your machine. Opening
attachments — even those that appear to come from a friend or
co-worker — also can install malware on your computer.
-
Download and install software only from websites you know and trust.
Downloading free games, file-sharing programs, and customized
toolbars may sound appealing, but free software can come with
malware.
-
Talk about safe computing. Tell your kids that some online activity
can
put a computer at risk: clicking on pop-ups, downloading free games or
programs, or posting personal information.
Finally, monitor your computer
for unusual behavior. If you suspect your machine
has been exposed to malware, take action immediately. Report problems with
malware to your ISP so it can try to prevent similar problems and
alert other

Q. What Should Parents know about Social
Networking Sites?
A. Social Networking
Sites
"It's 10 p.m. Do you know where your
children are?
"Remember that phrase from your own childhood? It's still a valid question, but now, it comes with a twist:
"Do you know where your kids are — and who they're chatting with online?
"Social networking sites have morphed into
a mainstream medium for teens and adults. These sites
encourage and enable people to exchange information
about themselves, share pictures and videos,
and
use blogs and private messaging to communicate with friends,
others who share interests, and
sometimes
even the world-at-large. And that's why it's important
to be aware of the possible pitfalls that
come
with networking online.
Some social networking
sites attract pre-teens – even kids as young as 5 or 6. These younger-focused
sites don't allow the same kinds of communication
that teens and adults have, but there are still things
that parents can do to help young kids socialize
safely online. In fact, when it comes to young kids, the
law provides some protections – and gives parents some control over the type of information that
children can disclose online. For sites directed to children under age 13, and for general audience sites
that know
they're dealing with kids younger than 13, there's the Children's Online Privacy Protection Act
(COPPA). It requires
these sites to get parental consent before they collect, maintain, or use kids'
Information. COPPA also allows parents to review their child's online profiles and blog pages.
Parents sometimes can feel outpaced by their technologically savvy kids.
Technology aside, there are
lessons that parents
can teach to help kids stay safer as they socialize online.
Help Kids Socialize Safely OnlineOnGuard Online shares these tips for safe social networking:
Help
your kids understand what information should be private. Tell them why it's important to
keep some things – about themselves, family members and friends
– to themselves.
Information like their full name, Social Security number, street address, phone number,
and
family financial information — like bank or credit card Account numbers
— is private and
should stay that way. Tell them not to choose a screen name that gives away too
much
personal information.
Use privacy settings to restrict who can access and post on your child's website. Some
social networking sites have strong privacy settings.
Show your child how to use these settings to limit who can view their online profile,
and
explain to them why this is important.
Explain that kids should post only information that you — and they — are comfortable
with others seeing. Even If privacy settings are turned on, some — or even all
— of your
child's profile may be seen by a broader audience Than you're comfortable with.
Encourage your child to think about the language used in a blog, and to think before
Posting pictures and videos. Employers, college admissions officers, team coaches,
and teachers may view your child's postings.
Even a kid's screen name could make a difference. Encourage teens to think about the
impression that screen names could make.
Remind your kids that once they post information online, they can't take it back.
Even if they delete the Information from a site, older versions may exist on other
people's computers and be circulated online.
Know how your kids are getting online. More and more, kids are accessing the Internet
through their cell phones.
Find out about what limits you can place on your child's cell phone. Some cellular
companies have plans that limit downloads, Internet access, and texting; other plans
allow kids to use those features only at certain times of day.
Talk to your kids about bullying. Online bullying can take many forms, from spreading
rumors online and posting or forwarding private messages without the sender's
OK, to
sending threatening messages. Tell your kids that the words they type and the
images
they post can have real-world consequences. They can make the target of the
bullying feel bad, make the sender look bad – and, sometimes, can bring on
punishment from the authorities.
Encourage your kids to talk to you if they feel targeted by a bully.
Talk to your kids about avoiding sex talk online. Recent research shows that teens who
don't talk about sex with strangers online are less likely to come in contact with
a
predator.If you're concerned that your child is engaging in risky online behavior,
you can
search the blog sites they visit to see whatinformation they're posting. Try searching
by their name, nickname, school, hobbies, grade, or area where you live.
Tell your kids to trust their gut if they have suspicions. If they feel threatened by someone
or uncomfortable because of something online, encourage them to tell you. You
can then
help them report concerns to the police and to the social networking site. Most
sites have
links where users can immediately report abusive, suspicious, or inappropriate
online
behavior.
Read sites'
privacy policies. Spend some time with a site's privacy policy, FAQs, and
parent sections to Understand its features and privacy controls. The site should
spell out
your rights as a parent to review and delete your child's profile if your child
is younger
than 13.
A Few More Tips to Protect Pre-TeensMany of the tips above apply for pre-teens, but
parents of younger children also can:
Take
extra steps to protect younger kids. Keep the computer in an open area like the
kitchen or family room, so you can keep an eye on what your kids are doing online.
Use the Internet with them to help develop safe surfing habits.
Consider taking advantage of parental control features on some operating systems
that let you manage your kids' computer use, including what sites they can visit,
whether they can download items, or what time of day they can be online.
Go where your kids go online. Sign up for – and use – the social networking spaces
that your kids visit. Let them know that you're there, and help teach them how to act
as they socialize online.
Review your child's friends list. You may want to limit your child's online “friends” to
people your child actually knows and is friendly with in real life.
Understand sites' privacy policies. Sites should spell out your rights as a parent to
review and delete your child's profile if your child is younger than 13.
For More InformationTo learn more about staying safe online, visit the websites of the following organizations:
Federal Trade Commission — www.OnGuardOnline.gov The FTC works for the consumer to prevent fraudulent, deceptive, and unfair business
practices in the marketplace and toprovide information to help consumers spot, stop, and avoid them.
To file a complaint or to get free information onconsumer issues, visit ftc.gov or call toll-free, 1-877-FTC-HELP
(1-877-382-4357); TTY: 1-866-653-4261.The FTC manages OnGuardOnline.gov, which provides practical tips
from the federal government and the technologyindustry to help you be on guard against Internet fraud,
secure your computer, and protect your personal information. ConnectSafely — www.connectsafely.org ConnectSafely is a forum for parents, teens, educators, and advocates designed
to give teens and parents a voice in thepublic discussion about youth online safety, and has tips, as
well as other resources, for safe blogging and socialnetworking. Along with NetFamilyNews.org, it is
a project of the non- profit Tech Parenting Group. Cyberbully411 — www.cyberbully411.org Cyberbully411 provides resources and opportunities for discussion and sharing
for youth - and their parents - who havequestions about or may have been targeted by online harassment.
The website was created by the non-profit Internet Solutions for Kids, Inc., with funding from the Community
Technology Foundation of California. GetNetWise — www.getnetwise.org GetNetWise is a public service sponsored by Internet industry corporations and
public interest organizations to helpensure that Internet users have safe, constructive, and educational
or entertaining online experiences. The GetNetWise coalition works to provide Internet users with the
resources they need to make informed decisions about their and theirfamily's use of the Internet.
iKeepSafe.org is a coalition of 49 governors/first spouses, law enforcement,
the American Medical Association, the American Academy of Pediatrics, and other associations dedicated
to helping parents, educators, and caregivers byproviding tools and guidelines to promote safe Internet
and technology use among children.
NCMEC is a private, non-profit organization that helps prevent child abduction
and sexual exploitation; helps find missingchildren; and assists victims of child abduction and sexual
exploitation, their families, and the professionals who serve them. staysafe —
www.staysafe.org staysafe.org is an educational site intended to help
consumers understand both the positive aspects of the Internet aswell as how to manage a variety of
safety and security issues that exist online.
WiredSafety.org is an Internet safety and help group. WiredSafety.org provides
education, assistance, and awareness on cybercrime and abuse, privacy, security, and responsible technology
use. It is also the parent group of Teenangels.org, FBI-trained teens and preteens who promote Internet
safety. See also: Social Networking Sites: Safety Tips for Tweens and Teens What to Do if There's a ProblemTrust your gut if you have
suspicions. If you feel threatened by someone or uncomfortable because of something online,Tell an adult
you trust, and report it to the police and the social networking site.The Children's Online Privacy
Protection Act (COPPA) requires websites to obtain parental consent before collecting, using,or disclosing
personal information from children under age 13.
Q. What are
Nigerian con-men or internet scams?
A.
Phony Lotteries, Nigerian 419s, Advanced Fee Fraud, and Scams
While you're online:
Know who you're
dealing with.
In any electronic transaction, independently confirm the other party's name, street
address, and telephone number.
Resist the urge to enter foreign lotteries. These solicitations are phony
and illegal.
Delete requests that claim to be from foreign nationals
asking you to help transfer their money through your bank account. They're fraudulent.
Ignore unsolicited
emails that request your money, credit card or account numbers, or other personal information.
If you are selling something over the Internet, don't accept a potential buyer's offer to send you a check
for more than the purchase price, no matter how tempting the plea or convincing the story. End the transaction immediately
if someone insists that you wire back funds.The Internet gives buyers access to a world of goods and services, and gives sellers access to a world of customers.
Unfortunately, the Internet also gives con artists the very same access. But being on guard online can help you maximize the
global benefits of electronic commerce and minimize your chance of being defrauded. OnGuard Online wants you to know how to
spot some cross-border scams — including foreign lotteries, money offers, and check overpayment schemes — and
report them to the appropriate authorities.
Foreign Lotteries
For years, scam operators have used the telephone and direct mail to entice U.S. consumers into buying chances in supposedly
high-stakes foreign lotteries. Now they're using email, too — either to sell tickets or suggest that a large cash prize
has your name on it. No matter what country's name is used to promote a lottery, the pitch follows a pattern: you should send
money to pay for taxes, insurance, or processing or customs fees. The amount may seem small at first, but as long as you keep
paying, the requests for funds will keep coming — for higher and higher amounts. Some victims have lost thousands of
dollars.Most scam operators never buy the lottery tickets on your behalf. Others buy some tickets, but keep the "winnings"
for themselves. In any case, lottery hustlers generally try to get you to share your bank account or credit card numbers,
so they can make unauthorized withdrawals.If you're thinking about responding to a foreign lottery, OnGuard Online wants you to remember:
Playing
a foreign lottery is against the law.
There are no secret systems for winning foreign lotteries. Your chances of getting any money back are
slim to none.
If you buy even one foreign lottery ticket, you can expect many more bogus offers
for lottery or investment "opportunities." Your name will be placed on "sucker lists" that fraudsters
buy and sell.
Keep your
credit card and bank account numbers to yourself. Scam artists often ask for them during an unsolicited sales pitch. Once
they get your account numbers, they may use them to commit identity theft.Resist solicitations for foreign lottery promotions. Report them to the appropriate government officials, then hit delete.View a sample fraudulent foreign lottery solicitation.
"Nigerian" Foreign Money Offers
The "Nigerian" scam got its name from emails that supposedly came
from Nigerian "officials" who needed your help getting at their money — which was tied up due to strife in
their country. Today, people claiming to be officials, businesspeople, or the surviving relatives of former government honchos
in countries around the world send countless offers via email to transfer thousands of dollars into your bank account if you
will just pay a fee or "taxes" to help them access their money. If you respond to the initial offer, you may receive
documents that look "official." But then, you will get more email asking you to send more money to cover transaction
and transfer costs, attorney's fees, blank letterhead, and your bank account numbers, among other information. Subsequent
emails will encourage you to travel to another country to complete the transaction. Some fraudsters have even produced trunks
of dyed or stamped money to verify their claims.The emails are from crooks trying to steal your money or commit identity
theft. Victims of this scam report that emergencies arise that require more money and delay the "transfer" of funds;
in the end, you lose your money, and the scam artist vanishes. According to the U.S. State Department, people who have responded
to these solicitations have been beaten, subjected to threats and extortion, and in some cases, murdered.If you receive an
email from someone claiming to need your help getting money out of another country, don't respond. After all, why would a stranger from another country pick you out at random to share thousands of
dollars? Report the solicitation to the appropriate government officials, and then hit delete.View a sample fraudulent foreign money offer.
Check Overpayment Schemes
Say
no to a check for more than your selling price, no matter how tempting the plea or convincing the story. Check overpayment
schemes generally target people who have posted an item for sale online. The con artist, posing as a potential buyer from
a foreign country (or a distant part of the U.S.), emails the seller and offers to buy the item with a cashier's check, money
order, personal check, or corporate check. Or the scammer may pretend to be a business owner from a foreign country, needing
"financial agents" to process payments for their U.S. orders; in exchange, they promise a commission.Regardless of the cover, here's what happens:
The scammer sends you a check that looks authentic — complete with watermarks — made payable for more money than
you expected. They ask you to deposit it in your bank account, and then wire-transfer some portion of the funds to a foreign
account. They provide convincing reasons why the check is for more than the necessary amount, and why the funds must be transferred
quickly. Sometimes, the counterfeit checks fool a bank teller, but be aware that the check still can bounce. The scammer vanishes
with the money you wired from your own account and you are on the hook for the entire amount of the worthless check. In addition,
a scammer who has your bank account number is likely to use it to withdraw more money from your account.
Reporting a Cross-Border Scam
If you think you may have responded to a cross-border scam, file a complaint at www.econsumer.gov, a project of 20 countries of the International Consumer Protection and Enforcement
Network. Then visit the FTC's identity theft website at www.ftc.gov/idtheft. While you can't completely control whether you will become a victim
of identity theft, you can take some steps to minimize your risk.If you've responded to a "Nigerian" scheme, contact your
local Secret Service field office using contact information from the Blue Pages of your telephone directory, or from www.secretservice.gov/field_offices.shtml.In addition, report telemarketing fraud and check overpayment scams to your state
Attorney General, using contact information at www.naag.org.Report unsolicited email offers to spam@uce.gov — including offers inviting you to participate in a foreign
lottery, looking for help getting money out of a foreign country, or asking you to wire back extra funds from a check you
received.If you receive what looks like lottery material from a foreign country through the postal mail, give it to your local
postmaster.
For More InformationForeign Lottery Scams
U.S. Federal Trade Commission — The FTC works for the consumer to prevent fraudulent, deceptive,
and unfair business practices in the marketplace and to provide information to help consumers spot, stop, and avoid them.
To file a complaint or to get free information on consumer issues, visit www.ftc.gov or call toll-free, 1-877-FTC-HELP (1-877-382-4357); TTY: 1-866-653-4261.
The FTC enters Internet, telemarketing, identity theft, and other fraud-related complaints into Consumer Sentinel, a secure,
online database available to hundreds of civil and criminal law enforcement agencies in the U.S. and abroad.Competition Bureau in Canada — The Competition Bureau is an independent law enforcement agency
in Canada that investigates anti-competitive practices and promotes compliance with the
laws under its jurisdiction. To file a complaint or to get free information, visit www.competitionbureau.gc.ca or call toll-free, 1-800-348-5358. The Bureau has the ability to refer criminal matters to the Attorney General of Canada,
who then decides whether to prosecute before the courts.United Kingdom's Office of Fair Trading — The United Kingdom's
Office of Fair Trading is responsible for making markets work well for consumers. They protect and promote consumer interests
throughout the United Kingdom, while ensuring that businesses are fair and competitive. To file a complaint or to get free information,
visit www.oft.gov.uk or send an email to enquiries@oft.gsi.gov.uk.Australian Competition and Consumer Commission — The Australian Competition and Consumer Commission encourages vigorous
competition in the marketplace and enforces consumer protection and fair trading laws. To file a complaint or to get more
information, visit www.accc.gov.au. The ACCC advocates consultation and negotiation as the first and
best option to settle disputes, but once the ACCC pursues legal action any sort of mediation becomes less likely.
"Nigerian" Advance-Fee Scams
U.S. Secret Service — The Secret Service investigates violations of laws relating to financial
crimes, including access device fraud, financial institution fraud, identity theft, and computer fraud. To file a complaint
or to get free information, visit www.secretservice.gov or call 202-406-5708.U.S. Department of State — The Department of State's mission is to create a more secure, democratic,
and prosperous world for the benefit of the American people and the international community. As part of that mission, the
Department of State seeks to minimize the impact of international crime, including cross-border internet scams, on the United States and its citizens. To get free information, visit www.state.gov.
Q. What should I do prior to disposing of an old computer?
A. Computer Disposal
Once you have a “clean” computer,
consider recycling, donating, or reselling it – and keep the environment in mind when
disposing of your computer.If you want to get rid of your old computer, options include recycling,
reselling, and donating.
But before
you log off for thelast time, there are important
things to do to prepare it for disposal. Computers
often hold
personal and financial
information, including passwords, account numbers, license keys or registration numbers for software
programs, addresses and phone numbers, medical and prescription information, tax returns, and other personal documents.
Before getting rid of your old computer, it’s a good idea to use software to “wipe”the hard drive clean. If you don’t, consider
your old hard drive a 21st century treasure chest for identity thieves
and information pirates. The Federal Trade Commission
(FTC), the nation’s consumer
protection agency, says you can deter identity theft and information piracy by taking a few
preventive steps.
Understanding Hard Drives
A computer’s hard
drive stores data, and maintains an index of files. When you save a file, especially a large one, it is
scattered around the hard drive in bits and
pieces. Files also are automatically created by browsers
and operating
systems. When you open a file, the hard drive checks the index, then gathers
the bits and pieces and reconstructs them.
When you
delete a file, the links between the index and the file disappear, signaling to your system that the file isn’t needed
any longer and that hard drive space
can be overwritten. But the bits and pieces of the deleted file stay on your computer
until they’re overwritten, and they can be retrieved with a data recovery program.
To remove data from your hard drive
permanently,
it needs to be wiped clean.
Cleaning Hard Dives
Before you clean your hard
drive, save the files that are important to you on an external storage device – for example,
a USB drive, a CDRom, or an external
hard drive – or transfer them to a new computer. Check your owner’s manual, the
manufacturer’s website, or its customer support line for information on how to
save data and transfer it to a new
computer. Utility programs to wipe your hard drive are available both online and in stores where computers are
sold.
They’re generally inexpensive; some are available on the Internet for free. Wipe utility
programs vary in their capabilities:
some
erase the entire disk, while others allow you
to select files or folders to erase. They also vary in their effectiveness:
programs that overwrite
or wipe the hard drive many times are very effective; those that overwrite or wipe the drive only once
may not prevent information being wiped from being recovered later.
If your old computer contains sensitive information
that would be valuable to an identity
thief, consider using a program that overwrites or wipes the hard drive many times. Or,
remove the hard
drive, and physically destroy it. One more thing to keep in mind: If you use your home or personal
computer
for business purposes, check with your employer about how to manage information on your computer that’s business-related.
The law requires businesses to follow
data security and disposal requirements for certain information that’s related to
customers.
Disposal
Options
Once you have a “clean”
computer, here’s how to dispose of it:
Recycle it. Many computer manufacturers have programs to recycle computers
and components. Check their
websites or call their toll-free numbers
for more information. The Environmental Protection Agency (EPA) has
information on electronic product recycling
programs at
program. Check with your county or local government,
including the local landfill office for regulations.
Donate it. Many organizations collect old computers and donate them to charities.
Resell it. Some people and organizations buy old computers.
Check online. Keep
the environment in mind when disposing of your computer.
Most computer equipment contains hazardous materialsthat don’t belong in a landfill.
For example, many computers have heavy metals that can contaminate the earth.
The EPA recommends that you check with your local health and sanitation agencies for ways to dispose
of electronics safely.
www.hypersmash.com
hostgator promo