|
|
|
|
1/31/2012
A-Fast Antivirus
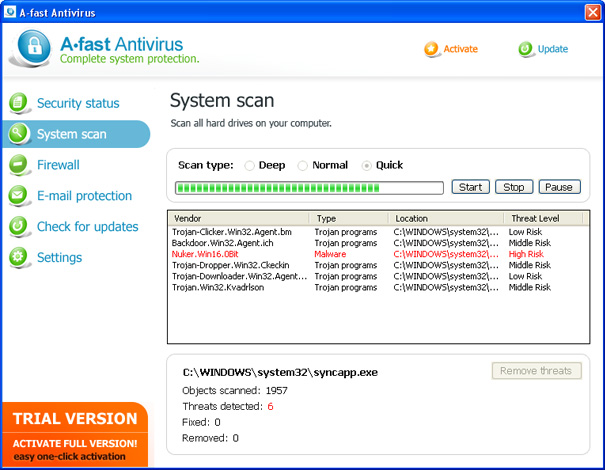
01/31/12 - A-Fast Antivirus is a rogue anti-spyware program that uses
misleading methods to scare users into thinking that their
computers are infected with malware. This scareware is promoted
through the use of Trojans and various malicious websites such as fake online scanners. Once installed, A-Fast Antivirus will simulate a system scan and report numerous infections. Then it will prompt you to pay for a full version of the program to remove the infections which don't even exist. Furthermore, A-Fast Antivirus will display fake security
alerts and pop-ups from Windows taskbar stating that your computer
is not protected or under attack from a remote computer. Some
of those fake security alerts read:
System
Warning!
To Continue working in unprotected mode
is very dangerous. Viruses can damage your
confidential
data and work on your computer. Click here to protect your computer.
Critical System Warning!
Your system is probably
infected with a version of Trojan-Spy.HTML.Visafraud.a. This may
result in website access passwords being stolen from Internet Explorer, Mozilla Firefox,
Outlook etc. Click Yes to scan and remove threats (recommended).
The rogue program also blocks legitimate anti-malware programs and system tools such as task
manager stating that it's infected. A-Fast Antivirus is a scam. Don't buy this bogus program. Instead, please use the removal instructions below to remove A-Fast Antivirus from
your computer as soon as possible. You can also use one of the
automatic removal tools listed below to eradicate his parasite from
your system as soon as possible.
Removal guide for A-Fast Antivirus:
When removing A-Fast Antivirus, reboot your computer into Safe Mode with Networking at first (Just reboot a machine and before Windows is launched start tapping F8 button.
You will see a table with this option). Then, login as the same
user you were previously using in the normal Windows mode, download
Spyware Doctor anti-spyware and save it on your desktop. Make sure you
nstall it and update the program before performing a scan. Now you will have to choose performing full system scan, the program will list and offer to remove all the detected malware. If the A-Fast Antivirus still blocks legitimate anti-malware programs, please use
of the the following erials to activate A-Fast Antivirus. Then
you will be able to use an anti-malware program to emove the
infection.
B0B302F772
C197C46C46
B20C1467B7
041E4B235A
25CCCC7329
9926220EED
A58EC19D33
C15F2FF276
F61E370D62
DDAD6A7A2C
9F8122FE00
3754DD9DA6
3DC52EA100
EE73BBFFA6
7E61C9C7DF
EE34D2E8A7
AA61971AA1
9D2510E3E8
A-Fast Antivirus
properties:
• Changes browser settings
• Shows commercial adverts
• Connects itself
to the internet
• Stays resident in background
     
HomeSiteUrls.com/Security/
01/31/12 - HomeSiteUrls.com/Security/ hijacker loads falsified security warnings and offers fake
security tools
for deleting the non-existent threats. It provides two options: downloading anti
-spyware, anti-virus and closing the
alert. No matter what is chosen by the user,
HomeSiteUrls.com/Security redirects the browser to a sale page of random,
rogue anti-spyware.
HomeSiteUrls.com/Security promotes various fraudulent tools: Windows Antivirus 2008, Win
Antivirus
2008, Ultimate Antivirus and some others. The worst thing about
HomeSiteUrls.com/Security hijacker is its persistence.
If it loads the warning message, no
matter what the user clicks, he/she is forced to visit fraudulent security websites.
HomeSiteUrls.com/Security
browser hijacker may also present itself as
HomeSiteUrls.com/Security/vista or HomeSiteUrls.com/Security/xp. Please
use one of the
automatic removal tools listed below to eradicate this parasite from your system as soon as
possible. 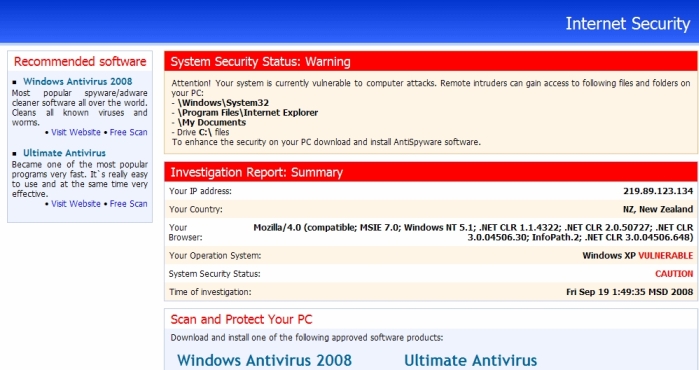
HomeSiteUrls.com/Security properties:
• Changes browser settings
• Shows commercial adverts
• Connects itself to the internet
• Stays resident in background
     
2:54 pm est
Clickbank
01/31/12 - Clickbank, also known as FakeMessage, is an adware parasite that continuously
displays fake Windows
error messages. Once the user clicks on such a message, Clickbank
opens a web site that attempts to install suspicious
applications. The threat must be manually
installed. It automatically runs on every Windows startup. Use one of the automatic
removal
tools to eradicate this parasite from your system.
Clickbank properties:
• Connects itself to the internet
• Hides from the user
• Stays resident in background
     
2:33 pm est
1/29/2012
Protect Your Critical Data (Disaster Recovery in the Cloud)
01/28/12 - Tape Backup is Dead
Experience
has shown me that tape backup is expensive, difficult, slow to recover files From,
and must be administered centrally (onsite). The tape media must be carried Offsite and it is
subject to failure. How do I know this…I was a contract Storage Area Network Administrator
(Backup and Recovery) in a DoD Disaster Recovery Center for over 7 years. We recovered
90%
of Unix and about 60% of Windows platform data (on all affected entities) after Hurricane Katrina.
The vast majority of businesses rely on tape backup as their sole data protection technology.
Tape’s days are numbered—the
limitations, unreliability and expense of these systems is giving
way to the rapid evolution of online backup. The DoD
cost of the contract
we had was $110.00
per Administrator per hour. Most packages for your Business are predetermined and not
scalable to your business. Your locked
in to whatYou probably
do not need. When the budget
cuts came, backup admins were eliminated. Experience has shown me that:
- 15% of all tape backups fail - 10 – 50% of all subsequent restores from tape
fail -
Restoring dat from tape older than 5 years fails 40 – 50% of the time - 34% of companies never test
a restore from tape -
Of the companies that do test a restore from tape, 77% experienced failure - 7 out of 10 small firms that
experience a major data loss are out of business in one year - A 10 degree temperature change can reduce the life of
a tape by 10 or more years.
Backup Touches
Everyone
Unlike many technology services, everyone needs data backup. Your business and consumer
clients may not all need
other services like Exchange hosting (Email hosting), web applications,
and the like. However, every single computer
requires an effective backup solution.
Backup To The Cloud
Whether you’ve learned from experience or by hearing of someone else’s misfortune, You know
how important it is to back up your data. Although hardware storage devices (such as portable
hard drives) can create an extra copy of files, they are susceptible to physical damage and can
be easily lost. When your files are backed up using a cloud-based service, you can be sure they
won’t be misplaced or lost in a fire or flood. They are particularly useful for small offices that need
offsite storage for backups.
Cloud services use the Web
to transfer your files to a data center in a different Geographic
location. An Internet connection and a computer are all you need to retrieve Your data. Accounts
are available at a variety of price points, and generally the rates are Tied to how much capacity is
offered by the service. Many will offer a small amount Of space free, however. For example, SOS
Online Backup offers
a 14 day trial and charges $79.95 to buy for 50 - 100GB of data you upload
annually. SOS Online also offers typical online
backup features, such as automatic backup
scheduling and the ability to share files with others.
SOS recently added support for backing up a variety
of mobile and handheld devices, including
iPhones, iPads and Android devices, for an additional monthly fee.
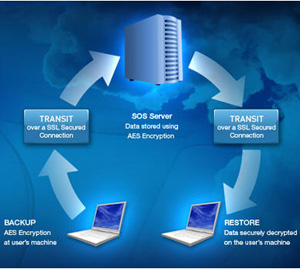
SOS protects the privacy of your data in
triplicate, encrypting your information on your computer,
in transit and when received. You can also add a private password
that no one has access to
except you so your files are 100 percent protected. This feature is called SOS UltraSafe and
it
restricts the access to your password – even to SOS employees.
The company has 11 Data Centers worldwide that
uses 256-bit AES and 128-bit encryption
methods across a SSL link, providing redundant storage in
multiple physical locations during file
transmission.. With this added protection, your data is safe even if something
happens to one of
the company's servers; your information is still secure and accessible from another SOS server.
SOS provides more than adequate security and surpasses many services with its encryption
protocols.
To give you
a better idea of how online services work, we’ll show you how to set up an account,
back up your data, and use
other features available to you in SOS Online.
Get Started
Download the SOS Online Backup installation file from
www.sosonlinebackup.com/sos-backup
-software-download.htm Although SOS Online saves your files to the Web, you control your
account
preferences And backups from a client you download to your computer.
To download
the program From the SOS Online home page:
For Windows Vista
& 7 users:
- Save
the SOS installation file (i.e. SOS V4.x.x.x.exe) to your local drive. (E.g. Desktop)` - Right
click on the SOS installation file, and choose “Run as Administrator”.
For XP & other users:
- Save the SOS installation file (i.e. SOS V4.x.x.x.exe) to your
local drive. (E.g. Desktop) - Double click on the SOS installation file.
Note: It is recommended to install SOS Online Backup software client in
the default directory.
When the installation is complete prepare to Run SOS Online Now. Select Finish. The program is
now on your computer.
Once the program
is installed, the setup process will begin. Begin Your Backup
How do you know if the software has been
installed correctly?
- Launch
an online backup
- Launch SOS Online Backup from
the launch icon on your desktop and log in.
-
Once logged-in, select Backup Online. - Run through the wizard selecting only a couple of small files and run the backup with the option to ‘return to Wizard mode’
selected. - Verify an online backup - Once the backup completes, go to ‘Advanced’ menu on the top right
side of the user interface
and select ‘Classic View’.- You
will see three tabs, ‘Storage View’, ‘Backup Mode’
and ‘Options’.- Select the ‘Options’
tab, and then ‘Backup History’. - In the ‘Backup History’ view, you will be able to view the backup
activity to verify that a backup has taken place.
- Launch
an online restore
- From
‘Classic View’ Click on ‘Tools’, and then ‘Run Wizard’. - Wait
for the software to collect account data (ie. what has been uploaded to the SOS servers). - Press ‘Next’ and you should see the file(s)
you have uploaded
you can select what you wish to recover.
- Run
through the remainder of the Wizard to recover your selections.
Share a File Share a Folder
If you want to back
up multiple computers (or a hardware storage device, such as a Portable
hard
drive), SOS Online can sync your data so all your files are accounted for And there are no
duplicates. It also supports multiple operating systems (in case you Have a Windows computer
at work and a Mac at home for example.) Note you don’t Have to download the SOS Online
program on each computer you want to sync, but you Will use the same account information. All
you need is your username and password and any
Web enabled device….Windows, Mac,
Facebook, iphone, android…Just enter your current account information
when prompted.
To share a file/folder, you can use MyAccount facility which is available from our website
(https://myaccount.sosonlinebackup.com ). Log in to your account using your username and
password and then select the “Online Recovery” link. There
will be a list of machines from which
you have done your backup so far, drill down to which files/folders you want to
share and then
select the “SHARE/RECOVER” link on the right of the table.
Accessing Your Files Online
SOS online can not directly back up SQL, Exchange, SAGE, Intrit, QuickBooks & Quicken and
MYOB files if they
are open.
Bandwidth is dependent upon the internet speed of the user. Some ISP’s high speed internet is
shared, reducing
the actual bandwidth available to the user affecting transfer speeds. A high
speed network of 100mbps may only have a
throughput of 39mbps if the bandwidth is shared
(based on the number of your housemates or neighbors that are online
and their activities).
Security scans use lots of bandwidth which will degrande throughput if they are run during
transfers. Business class networks usually do not experience these problems but they can if the
Systems Admins schedule
scans during backup. Check your ISP’s speed.
Whether you
need to find a single file or restore all your files to a new computer, You
can access
your collection of backed up data from the SOS Online Web site. From the home page, select
My Login link and then enter your username and password. From here you will be able
to view
the files you have backed up and stored in your SOS
Online account.
If you need to restore files or folders to your computer, follow the instructions for the data
you want to download to your computer.
SOS Online is one of many cloud based backup solutions.
Be proactive and find a cloud
Based backup solution
that will work for you, because if you wait until you need a
backup
of your files it’s already too late.
12:06 am est
1/25/2012
Mac OS X Quick Fixes
01/25/12 - Macs
have a reputation for reliability. They are complicated machines that still
encounter problems. Presented here are a
batch of routine problems that Mac users face and
what you can do about Them.
Your Mac crashes
Solution. Your
working on your Mac, when the screen suddenly goes dim, and a message
Appears in several languages. It says, “You need to restart your computer”.
This is a rare
Occurrence
but it is a particularly nasty problem. The immediate solution is to simply follow
The Instructions provided and restart your Mac. Most
likely, this is a transient glitch in the
System that you will not see again. If the crash occurs with great frequency,
then you have a problem. The cause is the recent
Installation of faulty software. Applications can install items called kernel extensions, which
Add features to the core of
the operating system. Check the Extensions folder for anything
That looks like it came from any software you installed recently. To find the folder,
click Go
And
Go to the folder. Then type ‘System/Library/Extensions’ and press ‘ENTER’. If you
Can identify the culprit, refer
to that application’s developers site for an update or to file a
Bug report. Until you find a resolution, move the kernel extension to the trash
and reboot
Your
Mac. Programs
quit unexpectedly Solution. An alarming occurrence
with the Mac is the ‘Quit Unexpectedly’ message. While
Working with any program on the Mac, if it suffers an error, it can simply die,
possibly
Taking
any unsaved data along with it. In the days prior to Mac OS X, such an event
indicated a fundamental instability in the OS,
And experience would quickly teach you to reboot immediately to save further problems.
Thanks to Mac OS X‘s Unix foundation,
applications run in their own protected memory
Space and have little chance of taking out the operating system when they crash. Like Unix,
Life goes on without the need to reboot. You can file a report to Apple… This feature allows you to send general information about
Your system’s specifications,
along with the ‘stack trace’ (a gibberish of text that only makes
Sense to programmers) of the crash to Apple. The company
then makes that information
Available to the developer, who can determine the cause of the crash and fix it. If you don’t
Mind taking the time, filing
a report can improve the quality of the software you use.
You improperly ejected a drive Solution. Sometimes,
when you have a lot going on with your Mac, you will unplug a hard
Drive or pull a USB key out without properly ejecting it. You will get a message
saying ‘The
Disk was not ejected properly. Now, earlier versions of Mac OS X take a more stern tone,
Advising you of the risk of damage to the
drive. The latest version of OS X takes a more
Reassuring tone, saying instead that any damage will be automatically repaired when the
Drive is reconnected. The
risk of prematurely ejecting a hard drive is interrupting a write operation on that drive.
If you were in the midst of
saving a file while you unplugged the drive, it is likely that the file
Will be corrupted. The operating system also performs various file management tasks
in the
Background;
interrupting these tasks could theoretically render the entire file system unusable. If
this happens, do not panic… you probably still have a perfectly safe drive on your hands.
Reconnect the drive and check any files you
were attempting to save to the drive. The next
Time, eject the drive properly by holding the ‘CTRL’ key down while clicking the drive icon
And then choosing ‘EJECT”.
You can not play videos with a .AVI extension
Solution. Certain
video formats the Mac can not play outside of the box. Those videos with an
.AVI file extension are susceptible. AVI (Audio-Video Interleaved)
is a file container format,
which usually contains video encoded with DivX or XviD. The Mac can not play these files. There
is an easy and free solution. Visit www.perian.org and download the free Quick Time
Plug-in. This software installs as a System Preference
pane; once in place, your existing Quick
Time Player application can play a broad variety of video formats, including .AVI’s.
The Finder can’t complete the operation because some data in ‘<Filename>’ can’t
Be read or written (Error code-36) Explanation. During a file, you suddenly run into thei error message… Error 36 is a common
Problem for
the Mac OS, and a search on Google will yield multiple (possible) causes.
Essentially, the error stems from a problem either reading the file being copied
or writing to
The
file’s new location. Solution. To diagnose
the cause of the problem, start with the source file. Is the drive on
Which the file is located still connected and available? You might see this message
when a
Drive
suddenly disappears from the network. Confirm as well that the destination drive is
Connected and available. You might also try duplicating
the file (Command-D) to create
A new copy in the same location as the source file, then moving that new version to the
Ultimate destination. Assuming
all is well with your file locations, check the source file itself. In many cases, this
Error is triggered by corruption
in the file. Try opening it in the file’s default application and
confirm that everything works properly. If
all else fails,you may be dealing with a permissions or hard drive issue. Try opening the
“Disk Utility” application (find
it by navigating to ‘Applications’ and then ‘Utilities’) and,
with the target disk selected, click ‘Repair
Disk Permissions’. While you’re here, you can
also attempt a verification of the drive itself by clicking ‘Confirm Disk’. There is no default application specified
to open the document <document name>.
Explanation.
You have received a file from a friend via e-mail. It has a generic icon, and
When you double-click it to view the contents,
you receive this error message. The message
Will prompt you to locate the application that can work with this type of file, but in my
Experience, if you are getting this message,
you are unlikely to have such an application on
Your Mac. Solution. In many cases,
there is little you can do, but respond to your friend, asking for
The file in a format that you can open. If you are unsure what applications belong
to the
File,
check an online resource such as FILExt (filext.com), where you can enter the file
Extension of the file and see a definition , as well
as a list of applications known to work
With it.
When sharing .ZIP files with PC users, you receive complaints about .DS_Store
Files. Solution.
If you have ever shared files with Windows using colleagues, you have probably
Exulted in the Mac’s built –in support
for creating and opening .ZIP archives. A simple
‘Right’ click or ‘CTRL’ click on a group of files or a folder will reveal the option (Compress
or Archive)
to create a single compressed file that you can readily email to others. Those
Windows users might complain if they receive a compressed folder from you, because
Alongside those handy files you’ve sent are
files that you don’t see. They’re called .DS_Store,
And there is one in every folder. You
don’t see this file on the Mac because of that period preceding the file name; it’s a
Signal to the Finder that this is a hidden
file (Linux and Unix users will recognize this practice).
The Desktop Services Store keeps track of positioning and other options for a particular
Folder. Suffice
to say, this file has no value once it’s placed on a Windows user’s computer,
And it can be safely deleted. You may wish to avoid the nuisance caused by seeing these files. There is a way to strip them
From directories before you
create your .ZIP archive. I.
Open the ‘Terminal’ application via ‘Applications’ and ‘Utilities’. II.
On the newly opened command line, type the command ‘cd’ followed by the file Path of the folder you
are archiving. The tilde (~) represents your home directory, So you don’t need to type that portion of the file path. For example, if
your Folder
is on the desktop , type ‘cd’ ~/Desktop and press ‘ENTER’. III. Issue
the following command, where <your_dir> is the name of the directory you Wish to remove the .DS_Store files from: find
<your _dir> -type f –name .DS_Store –print0 | xargs -0 rm. Continuing from our example
above, if you’re working with a file named Photos –type f –name
.DS_Store –print0 | xargs -0 rm and press ‘ENTER’. This command uses the ‘Find’ utility to do a search through the given folder for files named
.DS_Store. It then forwards
the results of the find to another utility, which deletes the file.
(If this Terminal stuff is too scary, you can use a free little utility by IntraArts
called DSWipe.
It’s
available at www.intrarts.com/software.html). You can now safely zip up the files, and
Your Windows using friends should have little
to complain about.
The Dock acts up
Solution. The Dock is a vital component of the Mac OS X. It serves as both the place to
View your currently
running applications and to store both applications and files for easy
Retrieval. While this tool has its odd points, for the most part, the Dock serves
its duties
With
aplomb. The Dock actually handles more than it appears. In addition to the strip that sits
on the edge
Of
your display, the Dock also runs the Dashboard, the Mac’s widget system, as well as the
Application Switcher, which activates with
the Command-TAB keyboard shortcut. These three apparently different systems can
put a lot of burden on a little system utility.
From supposedly running applications in the Dock that aren’t actually open, to a frozen
Application Switcher, problems
sometimes just pop up. The good news is that a fix is really simple. Open
up the ‘Terminal’ application again and
Issue this single command: ‘killall Dock’. This command force quits
the Dock application,
Which automatically restarts. This usually fixes any problems you may have.
1/23/2012
What Android Permissions Mean
01/23/12 - Installing Where’s My Droid and Password protecting your system is not The only type
of system
security users should become familiar with. Rogue Wi-Fi networks and cracking as a
result of using one are a growing
phenomena. Crackers will set up a network in a hotspot, such
as the book store, airport, library etc, and wait for nearby
users to log in. Once connected, it’s
possible for the intruders to access everything on your device. The key for the user is to never
use unfamiliar networks; only use those that
request a password, and avoid logging into personal
accounts (Bank, etc) while surfing in a hotspot. Try an app like
Wi-Fi Buddy to map
out what’s out there.
Full Internet Access
Many apps require internet access. But how like is it that
a Soduku app will really need full
internet access to the web? Security sense will help you avoid some rogue apps if
you use a
little common sense.
Video calling apps like Skype (securely) allows you to call
and message any of your friends on
Skype for free from your device wherever you are. There are also search apps (such
as Google
search app for Android) that enable instant contact with search results… requiring this
permission
is understandable. However, malicious apps might use this to dial premium-rate
numbers. Beware.
Modify or delete SD card contents
This permission option allows the app to modify data on your
SD memory card. While this can be
malicious in some instances, a lot of apps do require it to function. Some quick background
checks on the app, such as looking at reviews and checking the developer's website can help
you establish whether or
not it is friendly.
Find (GPS) Location Coarse (Network Based) Location
This option effeectively allows the app to track your location,
and is therefore probably more of a
privacy issue rather than a security one. Enabling this is fine when used as part
of a GPS related
app, but otherwise there is not really a legitimate reason for an app to be able to track you.
Read Contact Data, Read Calendar Data
This is fine for social networking apps such as Facebook and
WhatsApp, but otherwise you
should beware. Do you really want to give a game access to your contacts and your calendar?
How To Spot Malicious Apps
With all the information and personal data we can now store
on our phones they are valuable
targets for data theft and cracking and one of the simple ways this can be done is by
disguising
such activity within an app. Spotting such apps can be quite easy though. Look out for what the
app tries
to use when its open. is your 3G suddenly becoming active when you use an app that
requires neither? These could be early
signs that the app in question is trying to have a peek at
your data.
App Store Safety
Only download from trusted sources (Droid Market, Original
Vendor (AVG)). The filtering and
approval process offers users great protection and usually weeds out any apps that cause
harm
to systems. Before You download check out the developers site. If it doesn't look professional,
do not download.
Read The Reviews
Look at the most recent reviews and see what other consumers
think.
1/22/2012
Windows 7 Quick Fixes
01/22/12 - Microsoft’s Windows 7’s knack for running without problems is a testament to it’s
stability.
Even Though it has a good reputation, problems do occur. Solving common
Win7 problems requires Some basic troubleshooting,
but most of these problems have
relatively easy solutions that can Get you back to your regular computing activities
in no time.
1.
The screen is black when you start Win7
Solution. This panic inducing problem is often attributed to minor problems with your graphics
Card or
the cable that connects it to the monitor. First, check that your monitor is plugged into
A power socket and that the
monitor cable (either Video Graphics Array (VGA) or Digital Visual
Interface (DVI)) is firmly connected to both the monitor
and your computer’s graphics Port. If the
monitor flickers when moving the cable itself , so try a replacement
cable if you have one.
Another possibility is that your graphics card’s drivers
need to be updated (this is particularly
Likely if you just installed Win7 and are booting into the operating system
for the first time).
Restart your computer and press the ‘F8’ key during the boot process. When the ‘Advanced
Boot Options’ screen appears, use the arrow keys to highlight ‘Enable Low Resolution Video
(640x480)’,
press ‘Enter’, and wait for Win7 to start. When it does, visit your graphics Card
manufacturer’s Web
site and download the latest drivers for your card. Install the drivers And
restart Win7. If your computer has integrated
graphics instead of a discrete graphics Card, use
‘Windows Update’ (click ‘Start’, click ‘All
Programs’, and click ‘Windows Update’) to obtain the
most recent drivers.
2. When upgrading from
Vista, the Win7 installation process stops at 62%
Solution. Win7 can hang at various points during
the installation process for different reasons,
But one problem occurs more often than others. If your installation stops
at precisely 62%, it’s
Likely because a service has stopped responding. To fix the problem, restart your computer
And
let it roll back to Vista. Once you’re back in Vista, click ‘START’, right click ‘COMPUTER’
And
click ‘PROPERTIES’, Select ‘Advanced System Settings on the left menu. Choose the
‘Advanced’
tab, click ‘Environment Variables’, and click the ‘New’ button under ‘System
Variables’.
Next, type ‘MIG_UPGRADE_IGNORE_PLUGINS’ in the
‘Variable Name’ field, type
‘IphlpsvcMigPlugin.dll’ in the ‘Varible Value’ field,
and then click ‘OK’. Click ‘OK’ to close the
‘Environment Variables box, click ‘OK’
to close the ‘System Properties’ box, and then shut
down your computer. Repeat the Win7 upgrade process.
3. You’re
unable to join a homegroup
Solution. Win7 has eased the home networking
process through its use of homegroups, which
Help automate network creation. However, if you’re unable to join
a homegroup on your Network,
first make sure that a homegroup actually exists. If the homegroup was created On another
computer, check to make sure the homegroup has been created on that computer And that it is
turned on. After verifying
that the homegroup does exist, check that you’re Connected to the
network by clicking the Network icon in your
Taskbar. If you’re not, click ‘Start’. Open the
‘Control Panel’, click ‘Network’
and ‘Internet’, and open the ‘Network and Sharing Center’. Click
‘Connect To A Network’
and follow the instructions to connect to your Local network.
If you’re still unable to connect to the homegroup, make
sure your network location is set to
‘Home’ by opening the ‘Network And Sharing Center’, clicking
‘Public Network’ (or ‘Work
Network’), and then clicking ‘Home Network’. You can also
check to see if ‘Network Discovery’
is turned off, which would prevent you from accessing the home network.
In the Left panel of the
‘Network And Sharing Center’, click ‘Change Advanced Sharing Settings’,Click
the ‘Down’ arrow
button to expand the ‘Home Or Work’ profile, and select the ‘Turn On Network
Discovery’ radio
button. Click ‘Save Changes’ when finished.
If you’re still having problems, make sure the required
homegroup-related services are Running.
Click ‘Start’, open the ‘Control Panel’, select ‘System
And Security’, select ‘Administrative
Tools’, and double click ‘Services’ (You may be prompted
for an Admin password here, so make
sure you have it handy before trying this step). Scroll to the ‘Homegroup Provider’
service under
the ‘Name’ column and make sure “Started” appears under the ‘Status’
column. If it doesn’t,
double click the ‘Homegroup Provider’ entry, click the ‘Start’ button,
and click ’OK’. Repeat this
process for the ‘Peer Networking Grouping’ service.
4. Windows is unable to install
important updates
Solution. In most cases, the Win7 update process is seamless
as it downloads and installs
Important updates in the background. However, the OS occasionally encounters problems With
the update process and cannot install certain updates. If this happens, try manually Updating by
clicking ‘Start’,
clicking ‘All Programs’, and clicking ‘Windows Update’. In the left pane, click
‘Check
For Updates’, and then click ‘Install Updates’ after Windows Finds the important update
(or updates)
it was previously unable to install. Note that some Updates require you to accept
the Microsoft Software License Terms,
so be sure to Accept the terms to ensure a successful
update installation.
Some updates can require a hefty amount of hard drive capacity,
so Windows might have
Problems if your primary hard drive is running low on space. If you have 500MB or less Of drive
space left, run ‘Disk Cleanup’ in the ‘Search’ box, and press ‘Enter’. Select Your primary
drive
(usually C:) in the dropdown menu and click ‘OK’. Follow the Instructions to delete unnecessary
files.
5. Win7 returns a message
that access is denied when you try to open a file
or folder
Solution. If Windows prevents you from opening a file
or folder, check that you have Permission
to open it. ‘Right click’ the file or folder, click ‘Properties’,
choose the ‘Security’ tab, and click
‘Users’ under ‘Group Or User Names’. Under ‘Permissions’,
you’ll see the permissions for
‘Users’ (as opposed to Administrators) for that particular file or folder.
If ‘Read’ and/or ‘Write’ are
not selected under ‘Allow’, you’ll need to log
in with an administrator account to access the file or
folder or have the administrator of that computer change the permissions
for the file or folder. If
you have an admin account, you can choose to change the permissions yourself for your user
account. To do so, choose ‘Users’, click ‘Edit’ on the ‘Security’ tab, click to select
the
appropriate permissions, and click ‘OK’.
6. Win7 prevents you
from logging in to your computer because your user
account Is locked out.
Solution. If someone tries to log in to your account
too many times when using an Invalid
password, Win7 will lock the account. Assuming you have a separate admin Account
(and it is
highly recommended that you do for security purposes), you can Log in to Windows using that
administrator
account and unlock the user account. Click ‘Start’, type
‘lusrmgr.msc’ in the
‘Search’ box, and press ‘Enter’ to launch The ‘Local Users
And Groups’ utility. Click to select
the ‘Users’ entry in the left pane, And double click the locked
account in the right pane. On the
‘General’ tab, click To deselect ‘Account Is Locked Out’, click
‘OK’, close the ‘Local Users And
Group’ utility, and log out of Windows . Log back in using
the user account.
7. Win7 does not start
after being in Sleep Mode
Solution. Microsoft’s latest OS includes a wealth
of power saving options, but they Don’t always
work as designed, especially when the OS is paired with certain
Motherboards. If Win7 refuses
to start after being in Sleep Mode, you can tweak The power options to prevent Win7 from
sleeping. Reboot your computer and Open the ‘Control Panel’, select ‘System And Security’,
open
‘Power Options’. Next to your selected ‘Power Plan’ (for example, Balanced), click ‘Change
Plan Settings’, select ‘Never’ in the drop down menu beside ‘Put The Computer To Sleep’, and
then click ‘Change Advanced Power Settings’. Click to expand the ‘Sleep’ entry, click to expand
the ‘Allow Hybrid Sleep’ entry, click ‘On’, and change the setting in the drop down menu to ‘Off’.
Click ‘OK’.
If you want your computer to go to sleep after a certain period,
this solution will Serve only as a
work around. Because this problem is often related to outdated Motherboard software,
check
your motherboard manufacturer’s Web site for A BIOS (Basic Input/Output) update.
8. You’re unable
to print from a printer connected to your homegroup
Solution. First, check that the printer is plugged in
and turned on. Next, make Sure that the
person who connected the printer to the homegroup didn’t change The sharing
settings, because
if the printer is no longer shared, you won’t have Access to it through the homegroup. If the
printer is active and being shared Through the homegroup, try printing directly to the printer from
the computer To
which it is connected. If the printer doesn’t print from the host computer, You’ll
need to troubleshoot
the printer connection instead of the homegroup Issue. If none of these
steps work, try rebooting both the host computer
and Your computer. You can also try leaving
the homegroup and rejoining.
9. You cannot open or
copy files from the Web
Solution. Win7 is serious about security because plenty
of threats exist on the Internet.
Traditionally, Microsoft has been the lowest flying fruit for crackers And cybercriminals.
When
Win7 security controls are set too strictly, they Can prevent you from accessing files on the
Web. To fix this
problem, click ‘Start’, type ‘Internet Options’ in the ‘Search’ box, and press
‘Enter’.
Choose the ‘Security’ tab, select the ‘Internet’ zone, and move the slider under
‘Security
Level For This Zone’ to a lower level. For example, if the slider is set to ‘High’, move it to
‘Medium
High’. Click ‘OK when finished. If you’re still
having problems opening or copying Web
files after changing this Level, move the security slider to a lower level. If
this problem is
occurring Only with a particular site, return to the ‘Security’ tab in the ‘Internet
Properties’ dialog
box and click the ‘Trusted Sites’ zone. Next, click the ‘Sites’ Button
, copy the site’s URL to the
‘Add This Website To The Zone’ field, Click ‘Add’, click ‘Close’,
and click ‘OK’.
10. More Win7 solutions
Solution. Microsoft Fix It ( support.microsoft.com/fixit )
provides a wide range of Automated
wizards that run diagnostics on your computer to find and solve issues. So if your
experiencing
system slow down, they have helpful wizards available.
Win 7 Total Security 2012
01/22/12 - Win 7 Total Security 2012 is a fake antivirus parasite
that belongs to the fakerean
malware family. The parasite changes names according to the Windows Operating System
(OS) version (it is targeting), thus the same parasite might have Vista or XP instead of Win 7 in
name. The parasite
infects a user system through infected websites, fake shareware or cracked
downloads or by various system vulnerabilities.
Once the system is infected, Win 7 Total
Security 2012 fake antivirus will cause havoc on the system.
Initially, this rogue will display alerts that your system is severely infected.
It will suggest you run
a scan, during which Win 7 Total Security 2012 will display multiple infections that can not
be
fixed without the user purchasing updates through this rogue. However, all the detection this
rogue provides
are fake. The files are either not infected or harmless. You should remove Win 7
Total Security 2012 because it
prevents your PC from performing normal operations.
Win
7 Total security 2012 will try to block your legitimate programs from launching. There are
couple ways how to launch
them:
1. From another user account on Windows 7
system
2. Launching as administrator by right-clicking
on executable and choosing from menu
3. Renaming the executable
to something else, like iexplore.exe so Win 7 Total Security 2012
will not block it.
4. Launching anti-malware programs from safe mode with networking.
5. Stopping Win 7 Total Security 2012 processes with task manager or other
utility.
6. Using codes like 3425-814615-3990
or 9443-077673-5028 to disable malware.
This will allow running legitimate anti-malware programs and completely clean your PC
from Win 7 Total
Security 2012.
You can also use one of the automatic removal tools below to eradicate this parasite.
     
4:26 pm est
1/19/2012
You Need Security Suites, Encryption and a Better Password
01/19/12 - An unscrupulous Storage Facility in Ohio stole my life in 2008 (claiming I had not paid
my storage
fees) I was in NC at the time. (They even have TV programs now which glorify this
unregulated form of piracy.) Family
photo albums, my daughter's doll colection, my son's
baseball (football, basketball) card collection, his Hot Wheel car
collection, my wife's Wedding
Dress, Ball Gowns, shoes and purses, love letters and my military awards, uniforms, medals,
memorabilia, papers (it's legalized home invasion)... My children were both on active duty in the
military... This
was not a good time to be an American (Support The Troops). I served these
people for 21 years. The Attourney General
of Ohio advised me to get a Lawyer. I was betrayed!
This is the danger we face in our digital life (Invasion). Protect
Yourself.

A 2010 report released from McAfee estimates that cybercriminals
stole $1 trillion from users and
companies via the internet in 2008. Examples of major security breaches are numerous.
Albert Gonzalez, ringleader of 'Operation Get Rich or Die Tryin' group of crackers
(who breached
the Security of computer systems that TJX and Heartland Payment Systems operated in 2007
and 2008)
stole credit and debit card numbers to the tune of $200 million dollars got 20 years in
prison. He stole credit card
numbers and cash from ATM's. Gonzalez's prison sentence is the
longest stint a cracker has received in U.S. history and
covers three seperate convictions.
In 2011, hackers caused mayhem at banks, online gaming
networks, universities and healthcare
insurers, stealing the personal data of millions of customers. Sometimes the hacks
were
politically motivated. More often, cybercriminals were after data that could be used in phishing
and identity
scams or credit-card fraud.
Armed with viruses, Trojans and worms, crackers penetrated
the defenses of Citigroup and
brought down Sony's PlayStation Network. And while money remained the number one motive,
ideology drove extremists to raise havoc with San Francisco's subway system.
The Ponemon Institute calculates the average time for
a corporation to restore its reputation
following a headline-grabbing security breach is one year, with the loss to the
value of its brand
ranging from $184 million to $330 million. So lockdown those computers and keep a close eye
on
network traffic, as hackers are unlikely to be less determined in 2012.
In August, the Internet activist group Anonymous attacked
the web site of San Francisco's
subway system, spilling on the web the contact information of hundreds of the site's
users.
The hack drew national attention because Anonymous was
retaliating against BART shutting
down cell phone service during protest against police shootings. Critics accused the
agency of
violating free speech, while BART officials claimed it was necessary to prevent protesters from
communicating
police locations. The data stolen from the BART database included names,
addresses, phone numbers and e-mail accounts.
Anonymous also inserted its own logo on the
agency's web site. BART officials said the web site was separate from the
computer systems
that run the subway. Those systems were not affected.
In May, Health Net reported a security breach that compromised
the personal information of more
than 2.7 million current and past policy holders. The problem was reported two months
after IBM,
which manages the insurer's IT systems, told the company nine server drivers were missing from
its data
center.
At the time, the medical information breach was the third
largest in the Privacy Rights
Clearinghouse database, which tracks breaches across the nation. The incident was the second
time since May 2009 the Woodland Hills, Calif.-based company could not account for customer
medical and financial information.
In the prior case, a portable disk drive with medical and
financial data on 1.5 million customers went missing.
The University of Wisconsin, Milwaukee, reported in August
that a computer virus may have
exposed the names and social security numbers of 75,000 students and staff. The university's
IT
staff discovered the malware in May. University officials said the virus was most likely planted in
an attempt
to steal research documents, not personal information that could be used in identity
scams. The infected server ran software
for managing confidential information for several
departments. The system was shut down immediately after the discovery
and local and federal
police were called. The university says it has put additional security measures in place as a
result of the hack.
As if being unemployed wasn't bad enough, up to 210,000
Massachusetts jobless also had to
contend with having their personal data exposed. The state's Executive Office of Labor
and
Workforce Development reported in May that a virus had been discovered in the department's
computers, exposing
names, addresses and social security numbers to thieves. State officials
acknowledged that although the virus was discovered
shortly after it entered the department's
computer systems, engineers failed to completely eradicate the malware. The
data breach also
affected about 1,200 Massachusetts employers who filed quarterly reports using the agency's
computers.
The virus infected 1,500 computers in the agency's unemployment office.
In September, Vacationland Vendors, a Wisconsin Dells,
Wis.-based supplier of arcade
equipment and vending machines, reported that a hacker stole credit and debit card numbers
from card-processing systems. The Privacy Rights Clearinghouse said 40,000 people were
affected by the break-in. Vacationland
said the hacker had gained access to credit and debit
card transactions from Dec. 12, 2008, to May 25, 2011, at Wilderness
Resorts in Wisconsin and
Tennessee. The intrusion occurred through Vacationland's point-of-sale systems.
The theft was not an inside job, according to Vacationland,
which hired an outside consultant to
help prevent future hacks. Vacationland apologized for the security breach and advised
people
affected by the hack to notify card issuers and call a major credit agency, such as Equifax,
Experian or
TransUnion, to have a fraud alert placed on their files.
In July, Kiplinger Washington Editors reported that a
hacker had stolen the user names,
passwords and encrypted credit card numbers of as many as 142,000 subscribers of the
publishers various newsletters, including the Kiplinger Letter. The company acknowledged a two
-week delay in notifying
customers, saying that it took that long to determine the extent of the
damage. The Washington, D.C.-based company said
at the time that it wasn't sure whether
other data was stolen. While the credit-card numbers were encrypted, Kiplinger
said the
protection wasn't foolproof and recommended subscribers request new cards. The company
believed the
risk of identity theft was small because of the type of data available to the criminal.
In June, a cyber-attack that compromised the personal
information of 1.3 million subscribers of
Sega's online gaming network forced the Japanese video-game maker to shut down
the service.
Thieves stole names, birth dates, e-mail addresses and encrypted passwords before the
intrusion
was detected. No credit card numbers or other payment data were stolen, according to
Sega. The company said
it was "deeply sorry" for failing to prevent the breach of its Sega Pass
network and promised to
strengthen security. Because video-game companies hold a large
amount of financial and personal data from
customers, they have become a prime target for
hackers, experts say.
Citigroup was one of several high-profile companies that
failed to turn back a cyber-attack in
2011. The bank reported in June that 1 percent, or 210,000, of its 21 million card
holders had
their personal data compromised by hackers. The stolen information included names, account
numbers and
e-mail addresses. The banks said other identifying information, such
as birth dates
and social security numbers, was untouched. While the data stolen was limited, security
experts
said it was enough to be used in phishing attacks and other social-engineering schemes.
Citigroup did not release details
on how the breach occurred. The attack brought increased
scrutiny from the FDIC and other federal regulators who were
considering a systemic overhaul of
the banking industry's security and data protection systems.
In May, Fidelity National Information Services reported
that profits had taken a hit from a $13
million loss due to "unauthorized activities." While the prepaid debit
card processor provided few
details, media reports said a group of criminals had hacked the company's network and gained
access to its central database where card balances are kept.
The criminals then obtained 22 legitimate prepaid cards,
and made copies that were shipped to
conspirators in Greece, Russia, Spain, Sweden, Ukraine and the United Kingdom. Having
penetrated Jacksonville, Fla.-based, Fidelity's systems, the crooks were able to increase the
balances of the cards,
making it possible for their partners to withdraw cash from dozens of
ATMs during a 24-hour period. No arrests have been
made in the sophisticated heist.
Sony had the dishonor this year of topping CRN's list
of Biggest Security Stories Of 2011, as well
as the list of top security breaches. In April, a massive cyber-attack on
the entertainment Sony's
PlayStation Network and Qriocity services led to the compromise of 77 million user accounts.
In
hacking the Japanese company's database, thieves made off with scads of personally identifying
user information,
including date of birth, e-mail and home addresses and login credentials.
While credit-card data appeared to be safe at first,
the company later acknowledged that 12
million credit card numbers were unencrypted and could easily be read. After restoring
the
services, Sony had to take down the PlayStation Network in May, because of a snafu in the
password reset system
that hackers had started to exploit. Sony expected the breach to lower
operating profit by $178 million. Dozens of class-action
lawsuits were filed against the company.
In January 2012 Zappos' website was hacked, compromising
the personal information
of millions of customers.

Zappos.com has taken pains to assure customers that their credit card information is safe after a
data breach,
which was reported over the weekend, compromised information of up to 24 million
customers, including names, mailing
and billing addresses, phone numbers, truncated credit
card numbers and “cryptographically scrambled” passwords.
Consumers shouldn’t be
complacent when it comes to how their online data is encrypted, stored and sometimes left
vulnerable. Crackers could do plenty of damage with the information they did grab.
“Some of these details are what constitutes authentication
at a call center or website. This
means a crook with access to, say, a person’s mailing address might be able to
go online and
pretend to be that person — and then possibly find out their credit card information or other
details.
Zappos sent customers an email over the weekend instructing
them to change their passwords to
try and prevent further compromising of their personal information. The retailer, which
is owned
by Amazon, also recommended that customers change their passwords if they used their
Zappos password on
other sites.
It appears that the hack might have been the work of
“malicious code” that infected one or more
servers, as opposed to an all-out attack on the retailer’s
main site. But the bad news, is that
reading between the lines
leads him to suspect customers’ passwords could be exposed. “You
look for certain words,” how the company
described the exposed information. In communication
with customers, Zappos didn’t say that the compromised passwords
were encrypted, only
“cryptographically scrambled,” a virtually meaningless term that could indicate crackers
might be
able to easily figure out the actual passwords.
In an increasingly sophisticated criminal marketplace,
crackers will keep files on victims,
accruing pieces of information a little bit at a time until they have a profile
they can use to open
fraudulent accounts. “The thing people need to understand is the crime of identity theft isn’t
just
about credit card data.
The most important step consumers can take is to use
a variety of passwords for their online
shopping. Reusing the same passwords for multiple accounts heightens your chances
of having
your identity stolen. Another important, although easy, step is to create separate email accounts
for
your online retail activity and online financial services communication. That way, even if
crackers gets into a retailer
site, they won’t be able to trace that identity to your bank account
or credit card.
This is the continuance of a very powerful Industry:
- Cyber crime is the fastest growing crime today according to the Federal Trade
Commission.
- Cyber crime cost $67 billion dollars in 2009.
- Over 90% of all companies
experience data breach in one form or another.
- Cyber thieves attack individuals, corporations
and institutions, no one is safe.
- Social networking sites have become fertile
playground for crackers and cyber
criminals.
- More than 11 million
Americans were victims of identity theft last year.
- In the UK one cyber crime
is committed every 10 seconds.
- Protect your client?s electronic information,
it?s the law.
- Sensitive laptops stolen from Fla. [a health insurance provider]
exposes over
200,000. Feb 2010.
- Payroll processing firm Ceridian
Corp. hacked ? Feb 2010.
- Crackers access Iowa Racing and Gaming Commission database
? Feb 2010.
- Laptop containing UCSF medical school patient information stolen ?
February 2010.
- Thief steals 57 hard drives from BlueCross BlueShield
of Tennessee ? January
2010.
- Financial services firm notifies 1.2
million of data breach ? January 2010.
- An external drive containing the
sensitive data of thousands of patients was
stolen from an employee of health insurance provider Kaiser Permanent
- January
2010.
- A cracker recently accessed a computer server hosting
the online banking system
of Long Island, N.Y.-based Suffolk County National Bank (SCNB), putting thousands
of customer's login information at risk. ?January 2010.
- A cracker
accessed the computer network of Eastern Washington University in
Cheney, Wash., placing sensitive student information
at risk like Social Security
numbers and birth dates for 130,000.
- Protecting Customers? Personal Information Is Not An Option, But Legal Obligation.
- Study Puts Identity Theft Cost at $54B in 2009.
- In December 2009, a cracker used a SQL (Structured
Query Language) Injection flaw
to break into a database the Rock You (www.rockyou.com), a maker of social
networking applications, used to store
user account information (in plain text
no less), including email addresses and passwords for 32 million users.
Of the
32 million passwords, less than 1% of the passwords users created when creating
their accounts
were considered strong. The most popular password was 123456. Most
users also used identical or similar passwords
for all of their digital accounts.
- Days after the iPad debuted in 2009, a Group called Goate Security used a
security flaw in AT&T's
Web Site to expose about 114,000 email addresses of new
iPad users...including celebrities, media and technology
figures, and military
and elected officials who signed up for AT&T wireless 3G service. They exploited
the 'login' process.
- FBI arrested 100 peolple in October 2009 in the United States and Egypt accused
of scamming bank account numbers and other personal information from users as
part of "Operation
Phish Phry" with $1.5 million in stolen funds to fake
accounts. 33 U.S. residents were charged with wire,
bank, computer fraud,
identity theft and international money laundering.
- Research firm Javelin
estimates that more than 11 million Americans were victims
of identity theft last year, a 12 percent increase
that led to tens of billions
of dollars in costs.
- Identity
Theft Is No. 1 Consumer Complaint ? according to the Federal Trade
Commission.
- Medical Identity Theft Could Mean Life or Death to Its Victims -
HealthNewsDigest.com. The survey also
stated that 50 percent of large hospitals
experienced at least one data breach in 2009.
- Shell has been hit by a massive data breach - the contact database for 176,000
staff and contractors
at the firm has been copied and forwarded to lobbyists and
activists opposed to the company. Feb 16, 2010.
- Firewalls are not enough?..According to Richard Kirk,
UK Director for Fortify
Software because a firewall provides a gateway for users to explore the outside
world, it becomes the very doorway by which hackers gain entry.
- Crackers broke into computer systems at Wyndham Hotels & Resorts recently,
stealing sensitive customer
data.
- Medical identity
theft is a rising problem in Nevada, and, once a thief gets
enough information they can pretend to be you and
get services in your name,
even medical care.
- Data security company Imperva warns that hackers have transformed and automated
their attacks to make
them more efficient and boost the profitability of their
scams.
- Imperva, the data security leader, today released a new report warning that
crackers have become industrialized
and represent an exponentially increased
threat to individuals, organizations and Government.
- Symantec's 2010 Enterprise Security study found that 75% of organizations
globally experienced cyber
attacks in the past 12 months.
- Symantec says 42% of organizations now rate security as their top concern, more
than natural disasters,
terrorism and traditional crime combined.
- Identity crime is on the rise as criminals become cyber savvy and fish around on
social networking sites
for personal information, experts say.
- Lockheed Martin plans to find new methods to predict and prevent wide-scale
cyber attacks carried out
to compromise classified information and passwords.
- HSBC was fined £3m by the Financial Services Authority for failing to properly
look after its customers'
information and private data, as such breaches led to
at least two losses of customer data.
- Crackers made off with at least 285 million electronic records in 2008. - A new
study by Verizon Communications
Inc.
- Crackers broke into
computer systems at Wyndham Hotels & Resorts recently,
stealing sensitive customer data in 2009 and 2010.
-
500,000 members of BlueCross and BlueShield of Tennessee affected by data breach.
- FBI finds 90% of firms hit by Cybercrime.
- Cybercriminals still consider hotels easy targets for credit card info.
***Protect Yourself with one of the automated security suites listed below.
     
Ace Club Casino
01/19/12
- Ace Club Casino is a new one Casino software using iGlobalMedia software.
From the Ace Club Casino developer:
The Company is committed to protecting your personal information and respecting your privacy
in accordance with
best business practices. By disclosing your personal information to
Company, you consent to the collection, storage,
transfer and processing of your personal
information for the purpose of completing your Account related transactions
and for Company's
internal administration and analysis. Further, to provide you with better service, Company will
collect information from you through various technologies, including the use of cookies, and may
inform you of changes,
new services and promotions that Company determines you may find
interesting. Moreover, Company has the right to access
and disclose your information as
necessary to properly operate Company systems, protect Company and other end users,
and to
comply with any regulatory or governmental requests. Because of the complex and constantly
changing nature
of our technology and business, Company does not guarantee error-free
performance regarding the privacy of your personally
identifiable information and Company shall
not be liable for any incidental, consequential or punitive damages relating
to the use or release
thereof. By accepting any prize and/or winnings from Company, you consent to the use of your
name and/or likeness for advertising and promotional purposes without additional compensation
except where prohibited
by law.
Ace Club Casino properties:
• Shows commercial adverts
To eradicate this parasite from your system, use one of the automated security suites below.
     
6:56 am est
1/12/2012
Access Your PC From Anywhere
01/12/12
- With
GoToMyPC, you have the freedom to:
• Work on your Mac or PC from home — in real
time
• Travel anywhere and use your computer remotely
• Access your files, programs, email and network
• Go mobile using a free GoToMyPC app, It’s easy to enjoy
the convenience of secure access
to your computer from any browser – or one of our mobile apps.

Whether you're across the room or across the globe, there are
various methods of remotely
accessing your box. If you know how to use a web browser, then you already have the know-how
to log into your, say, office PC from anywhere.
You may not already know this, but before the creation of remote
desktop applications that make
this sort of thing a piece of cake, users were already remotely logging into their boxes
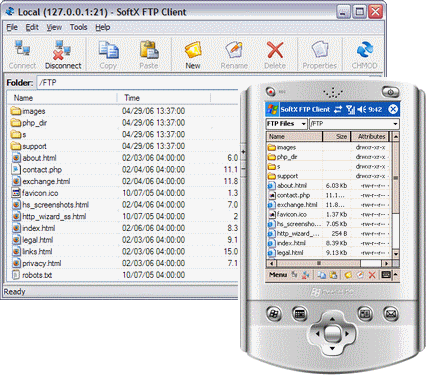
One way of doing this is via FTP, which is an acronym for
File Transfer Protocol. Put simply,
you'd install an FTP server on the computer you'd wish to log into and ensure that
the FTP
port, usually port 21, is open so that you can access it remotely. Once your FTP server is up and
running
on the host computer, you'd install and run an FTP client from a PC in a remote location,
10 feet way or 100 miles away,
for example. The FTP client communicates with the FTP server,
effectively letting you log into a directory structure
where you can transfer files to and fro. FTP is
not incredibly intuitive to use, but it's one of the first examples of
remotely accessing your
computer.
Another more arcane example is called telnet. The process is
basically the same as FTP: a
telnet server runs on the host computer while you'd log into it via a telnet client. Telnet
is even
less intuitive than FTP since it's all text-based, so if you're not used to command-line tools, as
many
*NIX users are, you may dislike telnet from the get-go if you're a Windows user.
Nowadays, it's recommended that you
use the more secure SSH--secure shell--as it's less
prone to exploits than telnet and much safer to use from a security
standpoint.
GoToMyPC
As technology inevitably marches on and improves upon itself
evermore increasingly, the web
browser is becoming more and more the mother application to run all children applications
from, so to speak. Desktop apps are being elbowed aside to make room for more convenient,
web-based apps that execute
inside your favorite browser fluidly and without a hitch, as web
browsers are becoming more powerful and more intelligent
as processing power gets cheaper
and new coding techniques, not to mention standards, dictate the norm.
GoToMyPC is the number one remote PC program on the market and it works on Mac;s
and
PC's. It comes with a free 30 day trial and it is touted as a way to access your home or
office computer
from anywhere you please. You're not simply limited to a text-based shell
interface or a crude representation of a designated
file structure from a remote location, but
you're given the full power to access all of your precious files and all your
PC's resources,
graphically. Distantly log in from your home PC into your work PC and grab your e-mails,
documents
and applications. As long as your remote PC is internet-capable and has a web
browser installed, then you can access
your distant PC that's running GoToMyPC. Of course,
the issue of security and exploits pop up when anyone talks about
opening up an Internet
gateway into your PC; for peace of mind, GoToMyPC uses 128-bit AES encryption, so you can
feel
relatively secure using this remote desktop solution.
The
beauty of GoToMyPC is that it installs over the web through a simple and sound process.
You don't
need to install or download any bloated applets to communicate with your host PC;
you can use any web browser to do this
task! A lot of desktop solutions have issues running
behind a firewall or proxy server, but GoToMyPC doesn't have any
problem running behind
most security software. One feature that comes in handy is the ability to allow guest access to
your remote PC, allowing you to set time limits for which guest access should expire for an
extra layer of security.
Transferring files and printing from a remote location has not been this
easy, so if you're in the market for a remote
desktop app, give GoToMyPC a test drive.
10:43 am est
Removing a Trojan
01/12/12 - If your computer
has a virus its security software can't detect of remove, it's time to
roll up your sleeves and go after the bug yourself.
Each month, we show you how to root out
deeply entenched viruses.
Trojan-Spy.Win32.Zbot.gen
Trojan-Spy.Win32.Zbot.gen is that nasty piece of malware every computer user
fears.
Although often classified as a Trojan, Trojan-Spy.Win32.Zbot.gen has
been known to use backdoor security exploits to
sneak its way onto a system.
Once there, Trojan-Spy.Win32.Zbot.gen sits in the background, recording key-
strokes
and, according to some, taking screenshots of your PC. Captured data
can include such sensitive information as credit
card data, username and pass-
word combinations, and other highly sensitive information of a personal or
financial
nature.
Is It On
Your System
Trojan-Spy.Win32.Zbot.gen is designed to run in the background
and be as
unobtrusive as possible. As a result, symptoms can be extremely hard to spot.
Obviously, if you're having
problems with identity theft, you should thoroughly
scan your system. If you have a lot of malware on your PC, this malware
may
well be on your scanner's list of found problems.
Manual Removal
You should begin by searching for and removing the files created by
Trojan-Spy.Win32.Zbot.gen. Some of the resident
files may not appear on the
infected system.
The first file you must locate is '1053.exe'
Windows XP
Go to the 'Start' menu and click 'Search'
Click 'All Files and Folders'
on the left side of the 'Search Results' window
In 'All
or Part of the Filename' type '1053.exe'
Click the
arrow next to the 'More Advanced Options'
Make sure there is a check next to 'Search System Folders' and Search
Hidden Files and Folders.
Click the 'Search' button to begin the search.
Windows Vista and Windows 7
Type '1053.exe' in the 'Search Programs and Files' field in the 'Start' menu
and press 'Enter'.
*If you don't receive initial results, click the Computer button under 'Search
Again' in.
Whether
you're using WinXP, Vista or Win7, if you rerceive any results,
'Right-Click' the result and select 'Delete' while pressing
the 'SHIFT' key to
permanently delete the file and skip the 'Recycle Bin'.
Repeat the steps for each of the following files:
Bana.execog.exe
Chi45.sys
Crypt_ldr.exe
Demo.exe
Dondom.exe
Dropped.exe
Eag1b.exe
Four
additional files are located in the Windows System folder. The exact location
of this folder depends on the version of
Windows you're running, but you can use
a variable consistent across all versions of Windows to quickly point you in
the
right direction.
Open 'My Computer'
In the Address bar, type %SYSTEM% and press 'ENTER'.
Search for
and remove the following files:
Ntos.exe
Twext.exe
Wsnpoem.exe
To remove the last file, click the Drivers folder in your Windows System folder.
Search for and delete:
Wsnpoem.sys
Now you must remove a few Registry entries. In the left side
of the Registry Editor
navigate to:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion
Right click the Network value on the right side of the Registry
Editor and select
'Delete'. Next select the 'Winlogon=%System% subfolder and remove:
Ntos.exe
Userinit.exe
You have now eradicated this parasite from your system. This is just one trojan out
of the multitude that are
floating around the net (each with its own character-
istics). You can attack them (one by one) or you can eliminate
a trojan fast with
one of the automated removal tools listed below.
     
1/7/2012
Surf Safely
01/07/11 - Most Web links are harmless. but some of them are designed to pose as normal
links to lure you
into dangerous territory. This makes it difficult to predict whether your friend's
email links to the cute web video
that's promised or to a malicious web site. To avoid becoming a
victim of a malicious link, some have turned to programs
that inspect web sites and assign them
safety ratings.
Don't Fall Victim
According to the IBM X-Force
2011 Trend and Risk Report, malicious links grew by 345% in 2011
from the previous year, which means cybercriminals have
found a profitable business model. For
example, phishing schemes (http://www.phishtrackers.com) found in messages include a link
that is similar to a legitimate company's
URL (uniform resource locator) to track victims into
going to a malicious Web site. Once at the malicious web site (which
often looks much like the
company's site), victims share information , such as usernames and passwords. Cybercriminals
are also able to download malware onto your computer if you click a bad link.
These links appear in all types of messaging, including email, chat and social networking.
Programs such as McAfee's Site Advisor Plus (www.mcafee.com) can help thwart these
criminals through both Web site safety ratings
and anti-phishing features. When you get an
email from what seems to be a legitimate source (such as your bank or your
credit card
company), SiteAdvisor Plus lets you know whether the attached link will really take you to the
organizations
site. SiteAdvisor Plus can also block connections to sites and downloads it deems
unsafe. That's particularly useful
when you plan to give personal information to the site you are
visiting.
Know Before You Go
The Web safety ratings from SiteAdvisor Plus lets you see whether a Web site has
any risks before you click it.
When your seach query nets results on popular
search engines, SiteAdvisor Plus adds an icon next to each of the results
that
signals whether the site could be harmful.
If you get a green circle with a check mark in the middle, the Web site has been
verified and is safe. The yellow
icon with an exclamation point indicates you
should proceed to the Web site with cauion. A red circle with an X means
the
Web site is known to be malicious. The same icons are used for links that show
up in emails, instant messenger
messages, and social networking messages. When
SiteAdvisor labels a Wev site, you can move the mouse cursor over the
top of the
icon to find out more about the threats associated with that site.
SiteAdvisor Plus also adds a button to your browser's address bar to rate the
URL's you enter. The button's colot
code is simple: Green indicates a safe,
legitimate site, yellow, cauions that the site may (or may not be) be legitimate:
and red denotes it is a malicious site.
Safety
First
The Web has created new and easy ways
to do everyday things, such as gather
information, shop and bank. However, it is important to make sure you're doing
these things safely and protection yourself from fraud or malware. You can best
protect yourself with Web safety programs
that guide you toward safe sites and
help you steer clear of the malicious ones.
1/6/2012
Windows, Linux and Mac OS Password Protection
01/06/12 - Let Password Dragon do your heavy lifting
Most people now have a slew of passwords they must remember
for email,
online-banking, social networking, and many sites and services. Some people
have dozens or even hundreds
of online accounts.
In these cases I have seen users applying the same password
to multiple
accounts (give or take a digit or two). That makes it easy to remember but
it's very insecure. A cybercriminal
can crack one website with weak security
to get your password and unlock your entire digital life.
On the other hand, if you use a different password on each
site everytime
you sign up for a new service or membership, you have a very slim chance at
remembering very many
of them.
There are a few tricks to get around the problem of remembering
passwords,
but you can use a password manager such as Password Dragon (freeware
www.passworddragon.com) to do the remembering for you.
You can download Password Dragon for free. During the installation
you will
be prompted to create a Master Password. Choose this password wisely because
it will be the key to all
of your personal data. It must be both very strong
(with a variety of letters, numbers and symbols) and also memorable,
lest
you forget. Do not write it down as all of the information you enter into
Password Dragon is protected by this
password.
Once the program is installed, it can be launched from a usb
drive. Password Dragon is a free, easy and secure password
manager that works on Windows,
Mac and Linux. View the screenshot.
First of all it’s free. No strings attached. Password
Manager does not contain
any spyware or ad-ware.
The application is very intuitive, user friendly and easy to use. Password
Management has never been so secure and
easy.
Files are encrypted with BlowfishJ
algorithm. Remember only the master password.
Works on Windows, Mac and Unix as this is written in Java. Can be launched
directly from USB thumb drive.
Organize all your userid, password, url and notes information in one file
Store additional information using the 10 additional customizable attributes
Data files are encrypted with BlowfishJ algorithm
Command line extension. Ability to view records from the command line without
launching GUI.
Available in Multi Language.
Built-in random flexible password generator
Copy UserId and password to clipboard
Password Strength indicator
Data
files are automatically backed up.
Application
Inactive timeout. i.e Lock the aplication if not used for x minutes
File Locking Facility
Launch URL from the application
Either Choose browser for URL launch or use system default browser.
Records can be grouped using user defined categories. Very flexible category
management.
Import records from text file
Export
all/selected records to text,HTML and XML file
Search records on all/specific columns
Record sorting based on column names.
Password can be masked in the main table and in the record view.
Ability to specify the startup sort order and startup category
Ability to choose the look and feel. (Kunststoff Look and Feel is the default.)
Pro
FREE: First of all it’s free. Password Manager is a freeware.
EASY: The application is very intutive, user friendly and easy to use.
SECURE: Files are encrypted
with BlowfishJ algorithm. Remember only the master
password.
MULTI-PLATFORM:
Works on Windows, Mac and Unix as this is written in Java. Can
be launched directly from USB
thumb drive.
Store all your userid, password, url, notes, custom attributes etc. in an
encrypted file
Con
Must be launched
from a usb drive
Conclusion
Nice program. Simple and platform-independent. I have it on my USB-Stick
Encrypt Important Data
01/06/12 - Protect Your Files
Medical records, tax documents and other files with personal information are often stored on
personal
computers. If you don't encrypt files that include personal information, you risk making
yourself an easy target for
cybercriminals. Encrypted folders, which are referred to as vaults, can
lock down your information, so it's unavailable
to anyone without your password.

Encrypt-Stick is the most advanced
portable security application available on the market today.
Encrypt-Stick software converts your USB flash drive into
a personal vault and the key to
access and secure your private files. Encrypt-Stick requires a serial numbered
USB flash drive
to run. It gives you the ability to create unlimited invisible encrypted vaults on an unlimited
number
of computers, removable hard drives or networked drives. If a vault is burned to a
DVD/CD you can securely access it
using the original USB used to create the vault. Encrypt
-Stick provides you with the highest level of protection from
identity theft, hackers, phishers and
will never leave a footprint on the host computer.
With a USB drive in your pocket you can carry around personal
notes, in-process documents
from work, or even top secret military communications. But a hole in that pocket
could quickly
become a major security leak. Encrypt Stick 5.0 ($39.99 direct) equips any USB drive with a
secure
encrypted vault for safe data transport. It can also serve as the key for any number of
local vaults on home or work
PCs, and it has a secure browser and password manager built in.
Note - Once you've activated your software on a particular USB drive you
can't move it to another
drive. Before you install Encrypt Stick, you'll want to select a high- quality USB drive
with as
much storage capacity as you anticipate you'll ever need. Conveniently, you can install the Mac
and Windows versions of the software on the same USB drive and access your protected files
from either platform.
Once you've downloaded Encrpt Stick (or using an installation CD/DVD)
your ready to create an encrypted vault.
Creating An Encrypted Vault
The setup wizard walks you through the steps necessary to install and activate Encrypt Stick on
your USB
drive. During this process you'll create a strong master password, something that
you'll remember but that nobody
would guess. The password-entry box has a built-in password
strength meter to help you make a good choice.
Your home system probably doesn't have a malicious keylogger
running, but if you're worried you
can enter that strong password using Encrypt Stick's virtual keyboard. For added
security
against monitoring software the virtual keyboard scrambles the location of the characters.
Encrypt Stick uses your password, along with device-specific
information, to generate a unique
512-bit (polymorphic) encryption key. That means your files are protected by
two-factor
authentication: something you have (the USB key), and something you know (the password).
Gaining
access to protected data requires both.
The wizard includes a recommended optional step that makes
a local backup of the decryption
key. That way if you lose the USB drive containing Encrypt Stick, you can still recover
encrypted
files stored on your computer. Files on the lost drive itself are gone, of course, but at least
nobody
else will be able to read them.
Vaults for File Protection
On initialization, Encrypt Stick creates an encrypted folder
right on the USB drive. When you've
entered the master password, you can freely move files into and out of this
folder or launch and
edit the files. Outside of the Encrypt Stick interface nothing is visible except encrypted filenames
and encrypted data.
You can also create any number of vaults on any PC or Mac to
protect local files on that system.
Encrypt Stick acts as a key to open these locked vaults. The product's
main window displays
available vaults in its upper portion and offers a view of the unencrypted main file system in its
lower portion.
To encrypt one or more files you simply drag them onto a vault. When you copy files into a vault,
Encrypt Stick offers to securely erase the originals. The help videos call
this "military wipe,"
implying a connection with the DoD standard for overwriting files before deletion. Basically,
it
erases the data and writes over it 7 times for the minimum DoD standard.I It also definitely
bypass' the
Recycle Bin, which is sufficient to foil casual recovery of secure files.
For additional security you can set Encrypt Stick to automatically
lock after a period of inactivity
(10 minutes by default) and require a periodic change of the main password (every
30 days by
default). This is near military grade encryption (in a commercial usb casing).
Private Browser
Encrypt Stick includes a built-in private browser. When you're
browsing from a "foreign" computer
your favorites, history, cached files, and all other browsing traces remain
on the device. Once
you unplug the device nothing remains on the host computer.
The private browser doesn't have every possible feature, but
it does support tabbed browsing, and
it can handle Flash and other popular content types. I was mildly
annoyed to find that Ctrl+Enter
in the address bar doesn't complete an address by adding "www." and ".com",
but I didn't find
any page that it couldn't display. I verified that no trace of surfing with the private browser
remains behind on a host system.
Encrypt Stick lacks the ability to take private browsing to
another level with the option to browse
using a fully encrypted secure session. This is what Intel Operators use when
they are
connected through a compromised network in a shady Internet café (the bad guys won't be able
to
sniff out private data from your network packets).
Limited Password Management
Encrypt Stick also includes a password management system linked
to its private browser. You
can store any number of passwords and group them in a hierarchy of categories, but you'll
do all
the work yourself—copying and pasting URLs from your browser and manually entering
username and password
data (with an option to use the virtual keyboard for passwords).
If you're setting up a new online account, you can use Encrypt
Stick to generate a strong
password. However, there's no provision to adjust the password generator to match a site's
password policies. Key Safe's password generator lets you set the length and choose which
character types to use. It
even includes an option to create passwords like "purrPler0ks"
that are easy to remember because you can pronounce
them.
Full-powered password managers automatically capture login data as you log
in to a site
manually using a supported browser. I was surprised to find that Encrypt Stick doesn't offer
this level
of automation, given that it has total control over the browser.
Key Safe also lacks most features of full-featured password
managers, but it does at least have
the ability to automatically launch IE, navigate to a saved page, and fill in the
login credentials.
With Encrypt Stick you must click a link to open the URL in the private browser, then right-click
the username and password fields individually to paste in the saved credentials. For some sites
this right-click process
didn't work; for others the "fill in" menu choices didn't appear.
You can import existing passwords from a .CSV file, but it's
not easy. To make use of a similar
feature in Key Safe I simply took a file exported from LastPass and rearranged the
data columns
to the order expected by the import facility. Key Safe can also import directly from several other
data types.
Getting my LastPass data into a form that Encrypt Stick would accept took half
an hour of
manual editing. I did succeed in the end, but only after requesting a sample of the correct format
from
ENC Security Systems' tech support.
Why didn't I just export a sample and study that to learn the
format? The export to .CSV feature
doesn't work. It produces a file, but the file is filled with gibberish.
After some experimentation I
determined that the "gibberish" is actually an encrypted copy of the password
data, not the
promised .CSV file. The password management feature could definitely use some work.
I also checked the help system to see if it would explain the
import process. Or rather, I tried.
There is in fact no help system, just a link to the product's online FAQ. To get
help for anything
that is not covered in the FAQ you have to e-mail tech support.
Working Out The Kinks
Encrypt Stick offers a good implementation of file protection
by encryption. It uses two-factor
authentication, and it can protect portable files on the device itself as
well as local files on any
number of other computers. The onboard private browser lets you surf the Web on a foreign
PC
without any risk of leaving private data behind.
The password management doesn't seem as polished as the rest
of the product. It looks good,
but it lacks the automation that would make it actually useful. And its import/export
system
doesn't work quite right. If you're looking for a portable password manager, look elsewhere. Still,
if you
need encryption-based protection for local files and portable files, with private
browsing as a bonus, Encrypt Stick
can be quite useful.
Pros
Turns any USB drive into secure portable storage. Can create local encrypted folders with two
-factor authentication. Private browser allows surfing on foreign PCs leaving no traces behind.
Includes password management. Virtual keyboard for safe password entry. Generates strong
passwords.
Version 4.2 is freeware.
Cons
Password manager requires manual entry of all data. Limited
ability to automatically open
Web sites using saved credentials. Password import/export facility not
working correctly. Can't
configure password generator to match specific password policies.
In Conclusion
Encrypt Stick 5.0 turns any USB drive into
secure portable storage for your important files. It
also serves as the key to unlock local encrypted
folders. An onboard private browser lets you
surf without leaving traces. Its weak point is the password
manager, which doesn't
seem quite finished. It's all good though... I have it on my USB stick. It
is 'AWESOME' !!!
1/5/2012
Ardamax Keylogger
2:55 am est
|
|
Q. How do I avoid rogue antispyware and antivirus software? A. Make sure you 'Choose Industry Certified "Security Program"
Solutions'! If your PC is connected to
the internet, uses e-mail, has software of an unknown origin
installed and comes into contact with recordable media (jump drives, dvd's, cd's, etc) Antispyware and Antivirus protection is a requirement. They help prevent attacks through e-mail (and/or attachments sent with e-mail) and surfing the web.
They also help you eradicate infections which are the result
of security holes and bugs in software. (The e-mail, web surfing
and software holes and bugs result in the most serious internet
attacks). One
way to know you're purchasing a trustworthy application is to confirm that the program
you choose has earned certification from the leading labs.
Industry certification
from ICSA Labs, Virus Bulletin, West Coast Labs, the National Association
of Specialist Computer Retailers, and others all require antispyware/ antivirus programs to meet stringent requirements to receive certification.
Smartphone and Tablet Tips to create a safe passcode. Smartphones and tablets open the
door to your Work, friends, family, bank details, etc... No matter which device you use, follow these tips to keep your data secure.
1. Always use a passcode. If someone gets hold of your device, the person has immediate access to your apps and
data. 2. Make your passcode difficult to guess. Codes such as 1234 or 2580 can be cracked in seconds. Go for something that’s
unique but easy for you to remember. 3. Longer is stronger. The longer the passcode, the harder it is to crack. Make yours a minimum of six
digits. 4. Mix numbers and letters. If your device allows, use a passcode that combines numbers, letters and punctuation. Avoid dictionary words and
choose a memorable combination. 5. Make it unique. Don’t use the same passcode for anything else, including other devices,
bank cards or online accounts. That way, if one passcode gets hacked the rest stay secure.
6. Be discreet. Look around and make sure no one is watching you enter your passcode, just as
you would protect your PIN at the ATM machine.
Q. What steps need to be taken to secure
mobile devices (smartphones) for personal/work phones and
tablets.
A. Follow these steps to secure your mobile
devices. 1. Secure your device a.
Always lock it
b. Apply a complex passcode
c. Shield your passcode
d. Apply the latest patches
2.
Prevent Malware Infections a.
Don't click on unsolicited links
b. Think before downloading apps
c. Don't "jailbreak" or "root" your mobile
3.
Be data aware a.
Be careful what you share
b. Encrypt sensitive data
4. Stay compliant
a. Know and follow your organizations security
policies
Q. Do you have an example of an Organizational 'Mobile Device Security Policy'
A. Here is EZMobilePC's policy.
1.
Introduction Mobile devices, such as smartphones and tablet computers, are important tools for the organization and their use
is supported to achieve business goals. However, mobile devices
also represent a significant risk to information security and data security as, if the
appropriate security applications and procedures are not applied, they can be a conduit for
unauthorized access to the organization’s data and IT infrastructure.
This can subsequently lead to data leakage and system infection.
EZMoblePC has a requirement to protect its information assets in order to safeguard its customers, intellectual property and reputation. This document outlines a set of practices and requirements for the safe use of mobile devices. 2.
Scope
1. All mobile devices, whether owned by EZMoblePC or owned by employees, that have
access to corporate networks, data and systems, not including corporate IT-managed
laptops. This includes smartphones and
tablet computers. 2. Exemptions: Where there is a business need to be exempted from this
policy
(too costly, too complex, adversely impacting other business requirements) a risk assessment
must be conducted being authorized by security management.
3. Policy - Technical Requirements
1.
Devices must use the following Operating Systems: Android 2.2 or later,
iOS 4.x or later.
2. Devices must store all user-saved passwords in an encrypted password store.
3. Devices must be configured with a secure password that complies with EZMoblePC's
password policy. This password must not be the same as any other credentials used
within the organization.
4.
With the exception of those devices managed by IT, devices are not allowed to be
connected directly to the internal corporate network.
3.1 User Requirements 1.
Users must only load data essential to their role onto
their mobile device(s).
2.
Users must report all lost or stolen devices to EZMoblePC
IT immediately.
3.
If a user suspects that unauthorized access to company
data has taken place
via a mobile device, they must report the incident in alignment
with EZMoblePC’s
incident handling process.
4. Devices must not be “jailbroken”* or have any software/firmware installed
which
is designed to gain access to functionality not intended to be
exposed to the user.
5.
Users must not load pirated software or illegal content
onto their devices.
6.
Applications must only be installed from official platform-owner
approved sources.
Installation of code from un-trusted sources is forbidden.
If you are unsure if an
application is from an approved source contact EZMoblePC IT.
7. Devices must be kept up to date with manufacturer or network provided patches.
As a minimum patches should be checked for weekly
and applied at least once a month.
8.
Devices must not be connected to a PC which does not
have up to date and enabled
anti-malware protection and which does not comply with corporate
policy.
9.
Devices must be encrypted in line with EZMoblePC’s
compliance standards.
10.
Users may must be cautious about the merging of personal
and work email accounts on
their devices. They must take particular care
to ensure that company data is only sent
through the corporate email
system. If a user suspects that company data has been sent
from a personal email account, either in body text or as an attachment, they must notify
EZMoblePC IT immediately.
11.
(If applicable to your organization) Users must not
use corporate workstations to backup or synchronize device content such as media files, unless such content is required
for legitimate business purposes. *To jailbreak a mobile device is to remove the limitations imposed by the manufacturer. This gives access to the operating system, thereby unlocking all its features and enabling the installation of unauthorized software.
Q. What is the first thing I should
do when I turn on my computer.
A. Back up important files
If you follow these tips, you're more likely to be free of interference from
hackers,
viruses,
and spammers. But no system is completely secure. If you have important files stored on your computer, copy them onto a removable disc or
an external
hard
drive, and store it in a safe place.

Q. How do I protect my password? A. Protect your passwords
Keep your passwords in a secure place, and out of plain sight. Don't share them
on the Internet, over email, or on the phone. Your Internet Service Provider (ISP)
should never ask for your password. In addition, hackers
may try to figure out your passwords to gain access to your computer. To make it tougher for
them:
Use passwords that have at least eight characters and include numbers or symbols.
The longer the password,
the tougher it is to crack. A 12-character password is
stronger than one with eight characters.
Avoid common word: some hackers
use programs that can try every word in the dictionary.
Don't use your personal information, your login name, or adjacent keys on the
keyboard as passwords.
Change your passwords regularly (at a minimum, every 90 days).
Don't use the same password for each online account you access.
Q. What steps need to be taken when
setting up Wireless Home Network Security. 1) Change Default Administrator Passwords (and Usernames)
Changing the default password is important because everyone
that purchases the same Wireless access device, knows your password. 2) Turn on (Compatible) WPA / WEP Encryption
By default, your Wireless device comes
without the encryption enables. WPA / WEP are security programs that forced your computer to provide
an encrypted password before you are allowed access
to the wireless access point. 3) Change the Default SSID
SSID is the network name of your wireless network;
most people leave the default name, such as, Linksys or NetGear. By changing the name, intruders have a more difficult time identifying your system and use known vulnerabilities. (And
of course, use the unchanged default password.) One
mistake people make is naming their home network their family name and or address. When cruising a neighborhood of wireless devices, its always scary to see Bobsnet444.
4) Disable SSID Broadcast
In Wi-Fi networking, the access point or router typically broadcasts
the network name (SSID) over the air at
regular intervals. This feature was designed for businesses and mobile hotspots where Wi-Fi clients may come and go. In the home, this feature is
unnecessary, and
it increases the likelihood an unwelcome neighbor or hacker will try
to log in to your home network.
5) Assign Static IP Addresses to Devices
Most home networkers gravitate toward using dynamic IP addresses.
This means that the IP Address, (the IP
Address is needed to participate on a network.) is typically
assigned automatically. A dynamic IP address on an unsecure system can also supply a hacker with a IP Address. 6) Enable MAC Address Filtering Each piece of Wi-Fi gear possesses a unique identifier called the "physical address" or "MAC address." Access points and routers keep
track of the MAC addresses of all devices that connect to them. Many such products offer the owner an option to key in the
MAC addresses of
their home equipment that restricts the network to only allow connections from those devices. Do this, but also know that the feature is not so powerful as it may seem. Hacker software programs
can fake MAC addresses easily.
7) Turn Off the Network During Extended Periods of Non-Use
The ultimate in security measures for any wireless network
is to shut down, or turn office your wireless access point
when you are not using. You are the most vulnerable at work or asleep, and mischief minded people know it.
8) Position the Router or Access Point Safely
Wi-Fi signals normally reach to the exterior of a home. A small amount
of "leakage" outdoors is not a problem,
but the further this signal reaches, the easier it is for others to detect and exploit. Wi-Fi signals often reach across streets and through neighboring homes. When installing a wireless home network, the position
of the access point or router determines it's reach. Try to position these devices near the center of the home rather than near windows to minimize
this leakage.
Q: What are the first security steps I should take before I connect my computer to the internet?
A: Practices Before You Connect a New Computer to the Internet
We advise home users to download and install software patches as soon as possible after connecting a
new computer to the Internet. However, since the background intruder scanning activity is constant, it may not be possible for the user to complete the download and installation of software
patches before the vulner- abilities they are trying to fix are exploited. We recommend the following actions 'before' connecting computers to the Internet
so
that
users can complete the patching process without incident.
Q. Are there any references you can recommend? A. References: A. Computer Emergency Response Team (CERT) B. Microsoft Windows
C. Apple Macintosh
OSX D. Linux
Q. How do I keep my system up to date once I go online. A. Keep your operating system
and Web browser Up-to-Date, and learn about their security features.
Hackers also take advantage of Web browsers (like Firefox or Internet Explorer) and operating system software
(like Windows or Mac's OS) that don't have the latest security updates. Operating system companies issue security
patches for flaws that they find in their systems, so it's important to set
your operating system and Web browser software to download and install security patches
automatically. In addition,
you can increase your online security by changing the built-in security and privacy settings in your operating system or browser. Check
the "Tools" or "Options" menus to learn how to upgrade from the default
settings. Use your "Help" function for more information about your choices. If you're not using your computer for an extended period, disconnect
it from the Internet. When it's disconnected, the computer doesn't send or
receive information
from the Internet and isn't vulnerable to
hackers.

Q. How do I keep my security software up to date. A. Use security
software that updates automatically Keep
your security software active and current: at a minimum, your computer should have anti-virus and anti-spyware software, and a firewall.
You can buy stand-alone programs for each element or a security suite that includes these programs from a variety
of sources, including commercial vendors or from your Internet Service Provider. Security software that comes pre-installed
on a computer generally works for a short time unless you pay a subscription fee to keep it in effect. In any
case, security software protects against the newest threats only if it is up-to-date. That's why it is critical to set your
security software to update automatically.Some scam artists distribute
malware disguised as anti-spyware software. Resist buying software in response to unexpected pop-up
messages or emails, especially ads that claim to have scanned your computer and detected malware. That's a tactic
scammers have used to spread malware. OnGuardOnline.gov can connect you to a list of security tools from legitimate security
vendors selected by GetNetWise, a project of the Internet Education Foundation.Once you confirm that your security software is up-to-date, run it to scan your computer
for viruses and spyware. If the program identifies a file as a problem, delete it. Anti-Virus Software Anti-virus software protects your computer from viruses that can destroy your data, slow your computer's performance, cause
a crash, or even allow spammers to send email through your account. It works by scanning your computer and your incoming
email for viruses, and then deleting them.
Anti-Spyware
Software Installed on your computer without
your consent, spyware software monitors or controls your computer use. It may be used to send you pop-up ads, redirect your computer
to websites, monitor your Internet surfing, or record your keystrokes, which, in turn, could lead to the theft of your personal
information. A computer may be infected with spyware if
it: Slows down, malfunctions, or displays repeated error messages
Won't shut down or restart
Serves up a lot of pop-up ads, or displays them when you're not surfing the web Displays web pages or programs you didn't intend to use,
or sends emails you didn't write. Firewalls
A firewall helps keep hackers from using your computer
to send out your personal information without your permission. While anti-virus software scans incoming email and files,
a firewall is like a guard, watching for outside attempts to access your system and blocking communications to and from sources
you don't permit. Don't Let Your Computer Become Part of a "BotNet"
Some spammers search the Internet for unprotected computers they can control and
use anony- mously to send spam, turning them into a robot network, known as a "botnet." Also known as a "zombie
army," a botnet is made up of many thousands of home computers sending emails by the millions. Most spam is sent remotely
this way; millions of home computers are part of botnets.Spammers
scan the Internet to find computers that aren't protected by security software, and then install bad software – known as "malware"
– through those "open doors." That's one reason why up-to-date security software is critical.Malware may be hidden in free software applications. It can be appealing to download free software like games, file-sharing
programs, customized toolbars, and the like. But sometimes just visiting a website or down- loading files may cause
a "drive-by download," which could turn your computer into a "bot." Another way spammers take over your computer
is by sending you an email with
attachments,
links or images which, if you click on or open them, install hidden software. Be cautious about opening any attachments or downloading files from emails you receive. Don't open an email attachment —
even if it looks like it's from
a
friend or coworker — unless you are expecting it or know what it contains. If you send an email with an attached file, include a text message explaining what
it is.
Q. What do I do in an emergency?
A. Here is what to do in an e-mergency
If you suspect malware is lurking on your computer, stop shopping, banking, and
other online activities that involve user names, passwords, or other sensitive information. Malware
could be sending your personal information
to identity thieves.
- Confirm that your security software is up-to-date, then use it to
scan your computer.
- Delete everything the program identifies as a problem.
- You may have to restart your computer for the changes to take effect.
- If the problem persists after you exhaust your ability to diagnose and treat it, you
might want to call for professional help.
- If your computer is covered by a warranty that offers free tech support, contact
the manufacturer.
- Before you call, write down the model and serial number of your computer, the
name of any software you've installed, and a short description of the problem.
- Your notes will help you give an accurate description to the technician.
- If you need professional help, if your machine isn't covered by a warranty, or if
your security software isn't doing the job properly, you may need to pay for
technical support.
- Many companies — including some affiliated with retail stores — offer tech
support via the phone, online, at their store, or in your home.
- Telephone or online help generally are the least expensive ways to access
support services — especially if there's a toll-free helpline — but you may
have to do some of the work yourself. -
Taking your computer to a store usually is less expensive than hiring a technician or
repair person to come into your home.
- Once your computer is back up and running, think about how
malware could have been downloaded
to your machine, and what
you could do to avoid it in the future.
- Also, talk about safe computing with anyone else who uses the computer.
Q. Where do I report
Hacking or Malware activity?
A. Here is where to report:
Hacking or a Computer Virus
Alert the appropriate authorities by contacting: Your ISP and the hacker's ISP (if you can tell what it is). You can usually find an ISP's email
address on its website. Include information on the incident from your firewall's log file. By alerting the ISP to the
problem on its system, you can help it prevent similar problems in the future. The FBI at www.ic3.gov. To fight computer criminals, they need to hear from you.
Internet
Fraud If a scammer takes advantage of you through an
Internet auction, when you're shopping
online, or in any other way, report it to the Federal Trade Commission, at ftc.gov. The FTC enters Internet, identity theft, and other fraud-related complaints into Consumer Sentinel, a secure, online database available to hundreds of civil and criminal law enforcement agencies in the U.S. and abroad.
Deceptive
Spam If you get deceptive spam, including email phishing
for your information, forward it
to spam@uce.gov. Be sure to include the full header of the email, including all routing information. You also may report phishing email to of ISPs, security vendors, financial institutions and law enforcement agencies, uses these reports to fight phishing.
Divulged
Personal Information If you believe you have mistakenly
given your personal information to
a fraudster, file a complaint at ftc.gov, and then visit the Federal Trade
Commission's Identity Theft website at ftc.gov/idtheft to learn how to minimize your risk
of damage from a potential theft of your identity.
Parents Parents sometimes can feel outpaced by their technologically savvy kids. Technology aside, there are lessons that parents can teach to help kids stay safer as they socialize online. Most ISPs provide parental
controls, or you can buy separate
software. But no software can substitute for parental supervision. Talk to your kids about safe computing practices, as well as the things they're seeing and doing online.
Social Networking
Sites Many adults, teens, and tweens use social networking sites to exchange information about themselves, share pictures and
videos, and use blogs and private
messaging to communicate with friends, others who share interests, and sometimes even the world-at-large. Here are some tips for parents who want their kids to use these sites safely:
Use privacy settings to restrict who can access and post on your child's website. Some social networking sites have strong privacy
settings. Show your child how to
use these settings to limit who can view their online profile, and explain to them why this is important. Encourage your child to think about the language used in a blog, and to think before posting pictures and videos. Employers, college
admissions officers, team coaches,
and teachers may view your child's postings. Even a kid's screen name could make a difference. Encourage teens to think about the impression that screen names could make. Remind your kids that once they post information online, they can't take it back. Even if they delete the information from a site, older
versions may exist on other people's
computers and be circulated online.
Talk to your kids about bullying. Online bullying can take many forms, from spreading rumors online and posting or forwarding private messages
without the sender's OK, to sending
threatening messages. Tell your kids that the words they type and the images they post can have real-world consequences. They can make the target of the bullying feel bad, make the sender look bad
— and, some- times, can bring
on punishment from the authorities. Encourage your kids to talk to you if they feel targeted by a bully. Talk to your kids about avoiding sex talk online. Recent research shows that teens who don't talk about sex with strangers online
are less likely to come in contact
with a predator.
Tell your kids to trust their instincts if they have suspicions. If they feel threatened by someone or uncomfortable because of something online, encourage
them to tell you. You can then help
them report concerns to the police and to the social networking site. Most sites have links where users can immediately report abusive, suspicious, or inappropriate activity.

Q. What is the best way to keep malware
out.
A.
Try to minimize the threat.
Minimizing
the Effects of Malware on Your Computer
Malware is short for “malicious software;” it includes viruses —
programs that copy themselves without your permission — and spyware, programs installed without your consent to monitor or control your
computer activity. Criminals are hard at work thinking up creative ways to get malware on your computer. They create appealing web sites, desirable downloads, and compelling
stories to lure you to links that will download malware, especially on computers that don’t use adequate security software. Then, they use the malware to
steal personal information, send spam, and commit fraud.It doesn’t have to be that way.
So says a website with tips from the federal government and the technology industry that is helping consumers be on guard against Internet fraud, secure their
computers, and protect their personal malware can wreak, and reclaim their computers and their electronic information. Computers may be infected with malware if they:
-
slow down, malfunction, or display repeated error messages;
- wont shut down or restart; -
serve up a lot of pop-up ads, or display them when youre not surfing
the web;
or
-
display web pages or programs you didnt intend to use, or send emails
you
didnt write.
If you suspect malware
is on your computer
If you suspect malware is lurking on your computer, stop shopping, banking, and other online activities that involve user names, passwords, or other
sensitive inform- ation.
Malware on your computer could be sending your personal information to identity thieves.
Then, confirm that your security software is active and current:
at a minimum, your
computer
should have anti-virus and anti-spyware software, and a firewall. You can buy stand-alone programs for each element or a security suite that
includes these programs
from a variety of sources, including commercial vendors or from your Internet Service Provider. Security software that comes pre-installed on a computer
generally works
for a short time unless you pay a subscription fee to keep it in effect. In any case, security software protects against the newest threats
only if it is up-to- date.
Thats why it is critical to set your security software and operating system (like Windows or Apples OS) to update automatically.
Some scam artists distribute malware disguised as anti-spyware software. Resist buying software in response to unexpected pop-up messages or emails,
especially ads
that claim to have scanned your computer and detected malware. Thats a tactic scammers have used to spread malware, and that has attracted the attention
of the Federal
Trade Commission, the nations consumer protection agency, as well as a security tools from legitimate security vendors selected by GetNetWise, a project
of the Internet
Education Foundation.
Once you confirm that
your security software is up-to-date, run it to scan your compu- ter for viruses and spyware. Delete everything the program identifies as a problem.
You
may have to restart your computer for the changes to take effect.If you suspect that your computer still is infected, you may want to run a second anti-spyware
or anti-virus
program. Some computer security experts recommend installing one program for real-time protection, and another for periodic scans of your machine
as a
way to stop malware that might have slipped past the first program.
Finally, if the problem persists after you exhaust your own ability to diagnose and treat it, you might want to call for professional
help. If your computer is covered by a warranty that offers free tech support, contact the manufacturer. Before you call, write down the model and serial number of
your computer, the name of any software you’ve installed, and a short description of the problem. Your notes will help you give an accurate description to the technician.If you need professional help, if your machine isn’t covered by a warranty, or if your security software isn’t
doing the job properly, you may need to pay for technical support. Many companies — including some affiliated with retail stores —
offer tech support via the phone, online, at their store, or in your home. Telephone or online help generally are the least expensive
ways
to access support services — especially if there’s a toll-free helpline — but you may have to do some of the work yourself.
Taking your computer to a store usually is less expensive than hiring a technician or repair person to come into your home.
Once your computer is back
up and running, think about how malware could have been downloaded to your machine, and what you could do to avoid it in the future. If your security software or operating system was
out-of-date, download the newest version and set it to update automatically. Use the opportunity to back up important files by copying them onto a removable disc. Other
ways to minimize the chances of a malware download in the future:
-
Don’t click on a link in an email or open an attachment unless you
know who sent it and what it is. Links in email can send you to sites
that automatically download malware to your machine. Opening
attachments — even those that appear to come from a friend or
co-worker — also can install malware on your computer.
-
Download and install software only from websites you know and trust.
Downloading free games, file-sharing programs, and customized
toolbars may sound appealing, but free software can come with
malware.
-
Talk about safe computing. Tell your kids that some online activity
can
put a computer at risk: clicking on pop-ups, downloading free games or
programs, or posting personal information.
Finally, monitor your computer
for unusual behavior. If you suspect your machine has been exposed to malware, take action immediately. Report problems with malware to your ISP so it can try to prevent similar problems and
alert other

Q. What Should Parents know about Social
Networking Sites?
A. Social Networking
Sites
"It's 10 p.m. Do you know where your
children are? "Remember that phrase from your own childhood? It's still a valid question, but now, it comes with a twist: "Do you know where your kids are — and who they're chatting with online? "Social networking sites have morphed into
a mainstream medium for teens and adults. These sites encourage and enable people to exchange information
about themselves, share pictures and videos, and
use blogs and private messaging to communicate with friends,
others who share interests, and sometimes
even the world-at-large. And that's why it's important
to be aware of the possible pitfalls that come
with networking online. Some social networking
sites attract pre-teens – even kids as young as 5 or 6. These younger-focused sites don't allow the same kinds of communication
that teens and adults have, but there are still things that parents can do to help young kids socialize
safely online. In fact, when it comes to young kids, the law provides some protections – and gives parents some control over the type of information that children can disclose online. For sites directed to children under age 13, and for general audience sites that know
they're dealing with kids younger than 13, there's the Children's Online Privacy Protection Act (COPPA). It requires
these sites to get parental consent before they collect, maintain, or use kids' Information. COPPA also allows parents to review their child's online profiles and blog pages. Parents sometimes can feel outpaced by their technologically savvy kids.
Technology aside, there are lessons that parents
can teach to help kids stay safer as they socialize online.
Help Kids Socialize Safely OnlineOnGuard Online shares these tips for safe social networking:
Help
your kids understand what information should be private. Tell them why it's important to
keep some things – about themselves, family members and friends
– to themselves.
Information like their full name, Social Security number, street address, phone number,
and
family financial information — like bank or credit card Account numbers
— is private and
should stay that way. Tell them not to choose a screen name that gives away too
much
personal information.
Use privacy settings to restrict who can access and post on your child's website. Some
social networking sites have strong privacy settings.
Show your child how to use these settings to limit who can view their online profile,
and
explain to them why this is important.
Explain that kids should post only information that you — and they — are comfortable
with others seeing. Even If privacy settings are turned on, some — or even all
— of your
child's profile may be seen by a broader audience Than you're comfortable with.
Encourage your child to think about the language used in a blog, and to think before
Posting pictures and videos. Employers, college admissions officers, team coaches,
and teachers may view your child's postings.
Even a kid's screen name could make a difference. Encourage teens to think about the
impression that screen names could make.
Remind your kids that once they post information online, they can't take it back.
Even if they delete the Information from a site, older versions may exist on other
people's computers and be circulated online.
Know how your kids are getting online. More and more, kids are accessing the Internet
through their cell phones.
Find out about what limits you can place on your child's cell phone. Some cellular
companies have plans that limit downloads, Internet access, and texting; other plans
allow kids to use those features only at certain times of day.
Talk to your kids about bullying. Online bullying can take many forms, from spreading
rumors online and posting or forwarding private messages without the sender's
OK, to
sending threatening messages. Tell your kids that the words they type and the
images
they post can have real-world consequences. They can make the target of the
bullying feel bad, make the sender look bad – and, sometimes, can bring on
punishment from the authorities.
Encourage your kids to talk to you if they feel targeted by a bully.
Talk to your kids about avoiding sex talk online. Recent research shows that teens who
don't talk about sex with strangers online are less likely to come in contact with
a
predator.If you're concerned that your child is engaging in risky online behavior,
you can
search the blog sites they visit to see whatinformation they're posting. Try searching
by their name, nickname, school, hobbies, grade, or area where you live.
Tell your kids to trust their gut if they have suspicions. If they feel threatened by someone
or uncomfortable because of something online, encourage them to tell you. You
can then
help them report concerns to the police and to the social networking site. Most
sites have
links where users can immediately report abusive, suspicious, or inappropriate
online
behavior.
Read sites'
privacy policies. Spend some time with a site's privacy policy, FAQs, and
parent sections to Understand its features and privacy controls. The site should
spell out
your rights as a parent to review and delete your child's profile if your child
is younger
than 13.
A Few More Tips to Protect Pre-TeensMany of the tips above apply for pre-teens, but
parents of younger children also can: Take
extra steps to protect younger kids. Keep the computer in an open area like the
kitchen or family room, so you can keep an eye on what your kids are doing online.
Use the Internet with them to help develop safe surfing habits.
Consider taking advantage of parental control features on some operating systems
that let you manage your kids' computer use, including what sites they can visit,
whether they can download items, or what time of day they can be online.
Go where your kids go online. Sign up for – and use – the social networking spaces
that your kids visit. Let them know that you're there, and help teach them how to act
as they socialize online.
Review your child's friends list. You may want to limit your child's online “friends” to
people your child actually knows and is friendly with in real life.
Understand sites' privacy policies. Sites should spell out your rights as a parent to
review and delete your child's profile if your child is younger than 13. For More InformationTo learn more about staying safe online, visit the websites of the following organizations:
Federal Trade Commission — www.OnGuardOnline.gov The FTC works for the consumer to prevent fraudulent, deceptive, and unfair business
practices in the marketplace and toprovide information to help consumers spot, stop, and avoid them.
To file a complaint or to get free information onconsumer issues, visit ftc.gov or call toll-free, 1-877-FTC-HELP
(1-877-382-4357); TTY: 1-866-653-4261.The FTC manages OnGuardOnline.gov, which provides practical tips
from the federal government and the technologyindustry to help you be on guard against Internet fraud,
secure your computer, and protect your personal information. ConnectSafely — www.connectsafely.org ConnectSafely is a forum for parents, teens, educators, and advocates designed
to give teens and parents a voice in thepublic discussion about youth online safety, and has tips, as
well as other resources, for safe blogging and socialnetworking. Along with NetFamilyNews.org, it is
a project of the non- profit Tech Parenting Group. Cyberbully411 — www.cyberbully411.org Cyberbully411 provides resources and opportunities for discussion and sharing
for youth - and their parents - who havequestions about or may have been targeted by online harassment.
The website was created by the non-profit Internet Solutions for Kids, Inc., with funding from the Community
Technology Foundation of California. GetNetWise — www.getnetwise.org GetNetWise is a public service sponsored by Internet industry corporations and
public interest organizations to helpensure that Internet users have safe, constructive, and educational
or entertaining online experiences. The GetNetWise coalition works to provide Internet users with the
resources they need to make informed decisions about their and theirfamily's use of the Internet. iKeepSafe.org is a coalition of 49 governors/first spouses, law enforcement,
the American Medical Association, the American Academy of Pediatrics, and other associations dedicated
to helping parents, educators, and caregivers byproviding tools and guidelines to promote safe Internet
and technology use among children. NCMEC is a private, non-profit organization that helps prevent child abduction
and sexual exploitation; helps find missingchildren; and assists victims of child abduction and sexual
exploitation, their families, and the professionals who serve them. staysafe —
www.staysafe.org staysafe.org is an educational site intended to help
consumers understand both the positive aspects of the Internet aswell as how to manage a variety of
safety and security issues that exist online. WiredSafety.org is an Internet safety and help group. WiredSafety.org provides
education, assistance, and awareness on cybercrime and abuse, privacy, security, and responsible technology
use. It is also the parent group of Teenangels.org, FBI-trained teens and preteens who promote Internet
safety. See also: Social Networking Sites: Safety Tips for Tweens and Teens What to Do if There's a ProblemTrust your gut if you have
suspicions. If you feel threatened by someone or uncomfortable because of something online,Tell an adult
you trust, and report it to the police and the social networking site.The Children's Online Privacy
Protection Act (COPPA) requires websites to obtain parental consent before collecting, using,or disclosing
personal information from children under age 13.
Q. What are
Nigerian con-men or internet scams?
A.
Phony Lotteries, Nigerian 419s, Advanced Fee Fraud, and Scams
While you're online:
Know who you're
dealing with. In any electronic transaction, independently confirm the other party's name, street
address, and telephone number. Resist the urge to enter foreign lotteries. These solicitations are phony
and illegal. Delete requests that claim to be from foreign nationals
asking you to help transfer their money through your bank account. They're fraudulent. Ignore unsolicited
emails that request your money, credit card or account numbers, or other personal information.
If you are selling something over the Internet, don't accept a potential buyer's offer to send you a check
for more than the purchase price, no matter how tempting the plea or convincing the story. End the transaction immediately
if someone insists that you wire back funds.The Internet gives buyers access to a world of goods and services, and gives sellers access to a world of customers.
Unfortunately, the Internet also gives con artists the very same access. But being on guard online can help you maximize the
global benefits of electronic commerce and minimize your chance of being defrauded. OnGuard Online wants you to know how to
spot some cross-border scams — including foreign lotteries, money offers, and check overpayment schemes — and
report them to the appropriate authorities. Foreign Lotteries For years, scam operators have used the telephone and direct mail to entice U.S. consumers into buying chances in supposedly
high-stakes foreign lotteries. Now they're using email, too — either to sell tickets or suggest that a large cash prize
has your name on it. No matter what country's name is used to promote a lottery, the pitch follows a pattern: you should send
money to pay for taxes, insurance, or processing or customs fees. The amount may seem small at first, but as long as you keep
paying, the requests for funds will keep coming — for higher and higher amounts. Some victims have lost thousands of
dollars.Most scam operators never buy the lottery tickets on your behalf. Others buy some tickets, but keep the "winnings"
for themselves. In any case, lottery hustlers generally try to get you to share your bank account or credit card numbers,
so they can make unauthorized withdrawals.If you're thinking about responding to a foreign lottery, OnGuard Online wants you to remember: Playing
a foreign lottery is against the law.
There are no secret systems for winning foreign lotteries. Your chances of getting any money back are
slim to none. If you buy even one foreign lottery ticket, you can expect many more bogus offers
for lottery or investment "opportunities." Your name will be placed on "sucker lists" that fraudsters
buy and sell. Keep your
credit card and bank account numbers to yourself. Scam artists often ask for them during an unsolicited sales pitch. Once
they get your account numbers, they may use them to commit identity theft.Resist solicitations for foreign lottery promotions. Report them to the appropriate government officials, then hit delete.View a sample fraudulent foreign lottery solicitation.
"Nigerian" Foreign Money Offers
The "Nigerian" scam got its name from emails that supposedly came
from Nigerian "officials" who needed your help getting at their money — which was tied up due to strife in
their country. Today, people claiming to be officials, businesspeople, or the surviving relatives of former government honchos
in countries around the world send countless offers via email to transfer thousands of dollars into your bank account if you
will just pay a fee or "taxes" to help them access their money. If you respond to the initial offer, you may receive
documents that look "official." But then, you will get more email asking you to send more money to cover transaction
and transfer costs, attorney's fees, blank letterhead, and your bank account numbers, among other information. Subsequent
emails will encourage you to travel to another country to complete the transaction. Some fraudsters have even produced trunks
of dyed or stamped money to verify their claims.The emails are from crooks trying to steal your money or commit identity
theft. Victims of this scam report that emergencies arise that require more money and delay the "transfer" of funds;
in the end, you lose your money, and the scam artist vanishes. According to the U.S. State Department, people who have responded
to these solicitations have been beaten, subjected to threats and extortion, and in some cases, murdered.If you receive an
email from someone claiming to need your help getting money out of another country, don't respond. After all, why would a stranger from another country pick you out at random to share thousands of
dollars? Report the solicitation to the appropriate government officials, and then hit delete.View a sample fraudulent foreign money offer.
Check Overpayment Schemes
Say
no to a check for more than your selling price, no matter how tempting the plea or convincing the story. Check overpayment
schemes generally target people who have posted an item for sale online. The con artist, posing as a potential buyer from
a foreign country (or a distant part of the U.S.), emails the seller and offers to buy the item with a cashier's check, money
order, personal check, or corporate check. Or the scammer may pretend to be a business owner from a foreign country, needing
"financial agents" to process payments for their U.S. orders; in exchange, they promise a commission.Regardless of the cover, here's what happens:
The scammer sends you a check that looks authentic — complete with watermarks — made payable for more money than
you expected. They ask you to deposit it in your bank account, and then wire-transfer some portion of the funds to a foreign
account. They provide convincing reasons why the check is for more than the necessary amount, and why the funds must be transferred
quickly. Sometimes, the counterfeit checks fool a bank teller, but be aware that the check still can bounce. The scammer vanishes
with the money you wired from your own account and you are on the hook for the entire amount of the worthless check. In addition,
a scammer who has your bank account number is likely to use it to withdraw more money from your account.
Reporting a Cross-Border Scam If you think you may have responded to a cross-border scam, file a complaint at www.econsumer.gov, a project of 20 countries of the International Consumer Protection and Enforcement
Network. Then visit the FTC's identity theft website at www.ftc.gov/idtheft. While you can't completely control whether you will become a victim
of identity theft, you can take some steps to minimize your risk.If you've responded to a "Nigerian" scheme, contact your
local Secret Service field office using contact information from the Blue Pages of your telephone directory, or from www.secretservice.gov/field_offices.shtml.In addition, report telemarketing fraud and check overpayment scams to your state
Attorney General, using contact information at www.naag.org.Report unsolicited email offers to spam@uce.gov — including offers inviting you to participate in a foreign
lottery, looking for help getting money out of a foreign country, or asking you to wire back extra funds from a check you
received.If you receive what looks like lottery material from a foreign country through the postal mail, give it to your local
postmaster.
For More InformationForeign Lottery Scams
U.S. Federal Trade Commission — The FTC works for the consumer to prevent fraudulent, deceptive,
and unfair business practices in the marketplace and to provide information to help consumers spot, stop, and avoid them.
To file a complaint or to get free information on consumer issues, visit www.ftc.gov or call toll-free, 1-877-FTC-HELP (1-877-382-4357); TTY: 1-866-653-4261.
The FTC enters Internet, telemarketing, identity theft, and other fraud-related complaints into Consumer Sentinel, a secure,
online database available to hundreds of civil and criminal law enforcement agencies in the U.S. and abroad.Competition Bureau in Canada — The Competition Bureau is an independent law enforcement agency
in Canada that investigates anti-competitive practices and promotes compliance with the
laws under its jurisdiction. To file a complaint or to get free information, visit www.competitionbureau.gc.ca or call toll-free, 1-800-348-5358. The Bureau has the ability to refer criminal matters to the Attorney General of Canada,
who then decides whether to prosecute before the courts.United Kingdom's Office of Fair Trading — The United Kingdom's
Office of Fair Trading is responsible for making markets work well for consumers. They protect and promote consumer interests
throughout the United Kingdom, while ensuring that businesses are fair and competitive. To file a complaint or to get free information,
visit www.oft.gov.uk or send an email to enquiries@oft.gsi.gov.uk.Australian Competition and Consumer Commission — The Australian Competition and Consumer Commission encourages vigorous
competition in the marketplace and enforces consumer protection and fair trading laws. To file a complaint or to get more
information, visit www.accc.gov.au. The ACCC advocates consultation and negotiation as the first and
best option to settle disputes, but once the ACCC pursues legal action any sort of mediation becomes less likely. "Nigerian" Advance-Fee Scams U.S. Secret Service — The Secret Service investigates violations of laws relating to financial
crimes, including access device fraud, financial institution fraud, identity theft, and computer fraud. To file a complaint
or to get free information, visit www.secretservice.gov or call 202-406-5708.U.S. Department of State — The Department of State's mission is to create a more secure, democratic,
and prosperous world for the benefit of the American people and the international community. As part of that mission, the
Department of State seeks to minimize the impact of international crime, including cross-border internet scams, on the United States and its citizens. To get free information, visit www.state.gov.
Q. What should I do prior to disposing of an old computer?
A. Computer Disposal Once you have a “clean” computer,
consider recycling, donating, or reselling it – and keep the environment in mind when disposing of your computer.If you want to get rid of your old computer, options include recycling,
reselling, and donating. But before
you log off for thelast time, there are important
things to do to prepare it for disposal. Computers
often hold personal and financial
information, including passwords, account numbers, license keys or registration numbers for software programs, addresses and phone numbers, medical and prescription information, tax returns, and other personal documents. Before getting rid of your old computer, it’s a good idea to use software to “wipe”the hard drive clean. If you don’t, consider your old hard drive a 21st century treasure chest for identity thieves
and information pirates. The Federal Trade Commission
(FTC), the nation’s consumer
protection agency, says you can deter identity theft and information piracy by taking a few preventive steps.
Understanding Hard Drives A computer’s hard
drive stores data, and maintains an index of files. When you save a file, especially a large one, it is scattered around the hard drive in bits and
pieces. Files also are automatically created by browsers
and operating systems. When you open a file, the hard drive checks the index, then gathers
the bits and pieces and reconstructs them. When you
delete a file, the links between the index and the file disappear, signaling to your system that the file isn’t needed any longer and that hard drive space
can be overwritten. But the bits and pieces of the deleted file stay on your computer until they’re overwritten, and they can be retrieved with a data recovery program.
To remove data from your hard drive permanently,
it needs to be wiped clean.
Cleaning Hard Dives Before you clean your hard
drive, save the files that are important to you on an external storage device – for example, a USB drive, a CDRom, or an external
hard drive – or transfer them to a new computer. Check your owner’s manual, the manufacturer’s website, or its customer support line for information on how to
save data and transfer it to a new computer. Utility programs to wipe your hard drive are available both online and in stores where computers are
sold. They’re generally inexpensive; some are available on the Internet for free. Wipe utility
programs vary in their capabilities: some
erase the entire disk, while others allow you
to select files or folders to erase. They also vary in their effectiveness: programs that overwrite
or wipe the hard drive many times are very effective; those that overwrite or wipe the drive only once may not prevent information being wiped from being recovered later.
If your old computer contains sensitive information that would be valuable to an identity
thief, consider using a program that overwrites or wipes the hard drive many times. Or, remove the hard
drive, and physically destroy it. One more thing to keep in mind: If you use your home or personal
computer for business purposes, check with your employer about how to manage information on your computer that’s business-related. The law requires businesses to follow
data security and disposal requirements for certain information that’s related to customers. Disposal
Options
Once you have a “clean”
computer, here’s how to dispose of it:
Recycle it. Many computer manufacturers have programs to recycle computers
and components. Check their
websites or call their toll-free numbers
for more information. The Environmental Protection Agency (EPA) has information on electronic product recycling
programs at
program. Check with your county or local government,
including the local landfill office for regulations.
Donate it. Many organizations collect old computers and donate them to charities.
Resell it. Some people and organizations buy old computers.
Check online. Keep
the environment in mind when disposing of your computer. Most computer equipment contains hazardous materialsthat don’t belong in a landfill. For example, many computers have heavy metals that can contaminate the earth. The EPA recommends that you check with your local health and sanitation agencies for ways to dispose of electronics safely.
www.hypersmash.com
hostgator promo
|
|